The journey continues. Microsoft has just announced the public preview of Defender ATP for Android. In this post, I‘d like to give you a short overview of its capabilities and how it fits in MDATP‘s existing features. Getting started At the moment, the public preview works with standalone or Android devices in Device Administrator mode….
Category: Blog
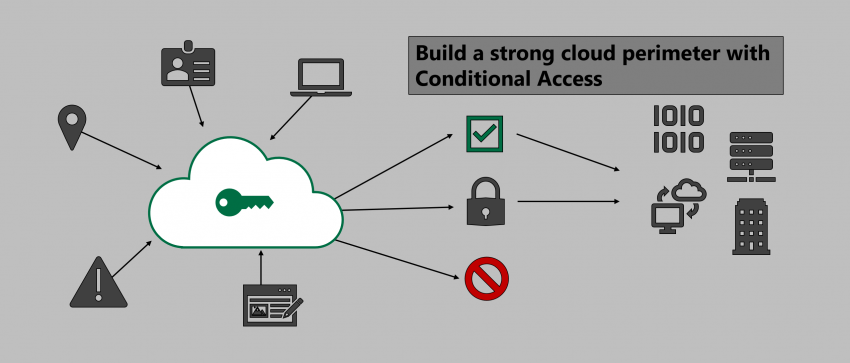
Build a strong cloud perimeter with Conditional Access
Phew, another article about Conditional Access. That’s right, there a quite a few already. Fortunately, this topic never gets old. Here’s why: In the cloud there are no traditional network perimeters anymore. On-prem appliances are rendered useless as cloud services can be accessed world-wide. All you need is a valid set of credentials to sign-in….
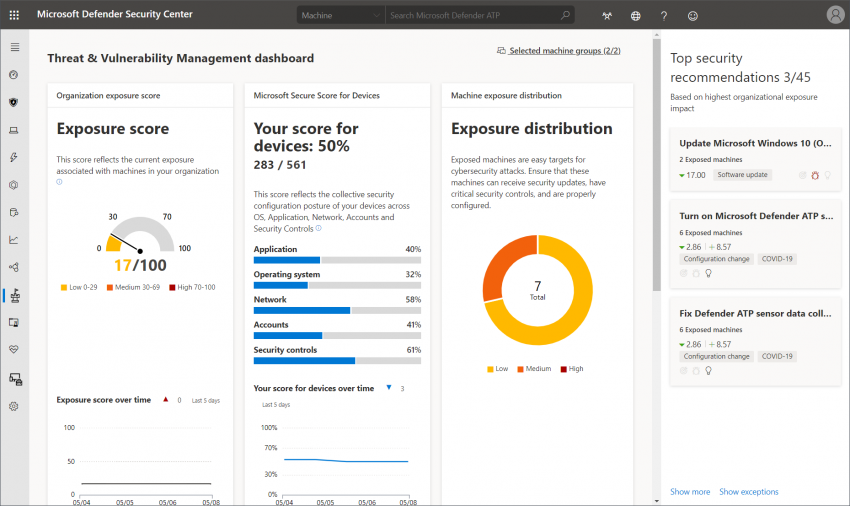
Threat & Vulnerability Management – improve client security with MDATP
Staying on the pre-breach side of things is the main goal in IT security. How can you achieve this state on Windows clients? A large amount of malicious software relies on unpatched vulnerabilities or misconfiguration that can be abused. A few months back, Microsoft added Threat & Vulnerability Management to Microsoft Defender Advanced Threat Protection…

Azure Sentinel – monitor servers using Sysmon
In this post I’m showing how to connect Windows servers to Azure Sentinel, install Sysmon, how to parse those events, and what to do with them. After all, Sentinel is a cloud-native SIEM, but luckily, it’s not cloud-only. Setting up Azure Sentinel This step is quite simple. Sentinel is basically just a solution that builts…
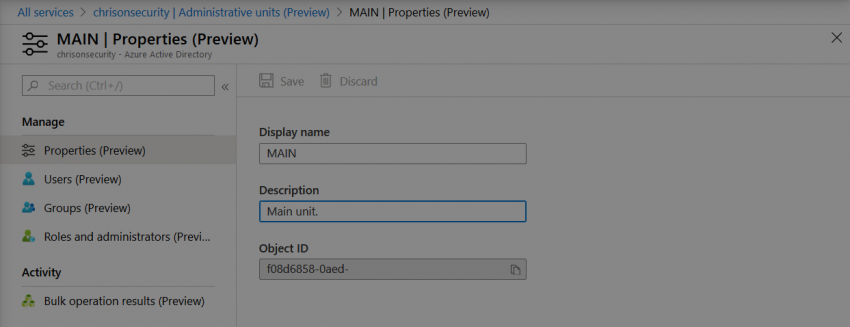
Getting started with Azure AD Administrative Units
Azure AD always had a big advanced over on-premises Active Directory: a very granular RBAC approach when it come to administration. However, there is also a downside – roles can only be applied globally without a limited scope. This has changed now. Being in a PowerShell based preview for quite some time, Azure AD Administrative…

Microsoft Defender ATP for Linux
Microsoft Defender ATP for Linux is here! Again, Microsoft expand their MDATP ecosystem to match the commitment to open source and operating systems other than Windows (Server). Azure resources are heavily depending on Linux, so this is a logical next step. In the course of 2020, MDATP’s capabilities will also be extended to iOS and…

Going passwordless with Azure Active Directory – part 3
I already posted a few things about FIDO2 and other passwordless authentication scenarios for Azure AD (introduction / additional info). Now (or to be more precise: in Q1/2020), the real funky stuff begins! As Microsoft announced at Ignite 2019, they will be extending FIDO2 support to hybrid Azure AD joined devices which will also grant…

Microsoft Defender ATP – network control made easy
Controlling clients at the network level has been a use case for many companies for the last decades. In most cases, local network infrastructure like proxies or firewalls are used to control which resources can be accessed by a client. What if devices are on the road? In the cloud, this concept has been adapted…
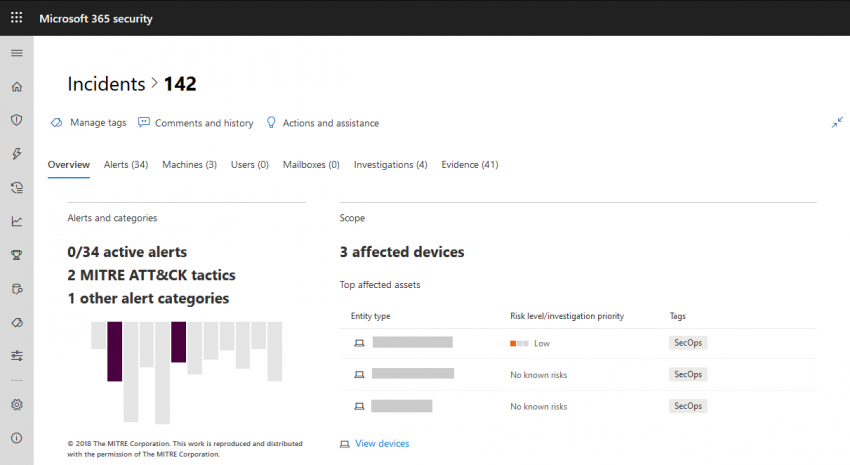
Microsoft Threat Protection – unified incidents
Note This post is part of a series about Microsoft Threat Protection. You can find part 1 about unified hunting here: https://chrisonsecurity.net/2019/12/15/microsoft-threat-protection-unified-hunting/ In my last post about Microsoft Threat Protection (MTP) I talked about unified hunting where you can use data signals from Defender ATP, Office ATP, and (coming soon) MCAS / Azure ATP to…

Looking back at 2019
Hello everyone! While I usually only post about technological topics, I will also speak about some personal topics of the year (and decade) that is now almost finished. The blog But first lets have a look at what happened on my blog this year. Although I started it in November 2018, I only started writing…
