When it comes to cyber attacks, e-mails are still in most cases the initial point of compromise. Users are either lured to enter their credentials on a spoofed website or malware is attached in an obfuscated way. For example, by leveraging Office macros or making the user to “Enable content” which is disabled by default in current versions of Microsoft Office.
Recently, Exchange Online Protection, Office 365 Advanced Threat Protection, and most third-party appliances have gotten quite effective in blocking malicious content from e-mails and attachments. However, all of those products rely on being able to scan said files. What if those are encrypted, e.g. by using Azure Information Protection labels that include a protection setting that only let’s the targeted recipient open it?
In this post, I’ll try to explain some concepts that could be implemented to defend against obfuscated malicious content via e-mail – even if you might assume it is already to late. Those might also apply to similar scenarios like other forms of encrypted mails / attachments or malicious mails in general.
So, the main question for this post is: what are the second-line defences we have at hand?
Full mitigation: only allow known partner tenants to send RMS-protected content (or block it completely)
This is the most obvious solution. Some companies are already leveraging this approach to make sure only scanable content can be received by users. However, if you want to make use of Azure Information Protection with external partners, this solution is not feasible. Which of course leads to a major problem: nothing will be scanned. Neither ATP safe-attachments nor safe-links will be able to work. Depending on whether the complete e-mail or only attachments are encrypted, impersonation could still be detected if the attacker uses a spoofed account or domain to impersonate an external partner.
If you don’t want to rely on mail scanning to only partially detect parts of malicious content you can block RMS-protected content (e-mails / attachments) by Exchange Online transport rules:
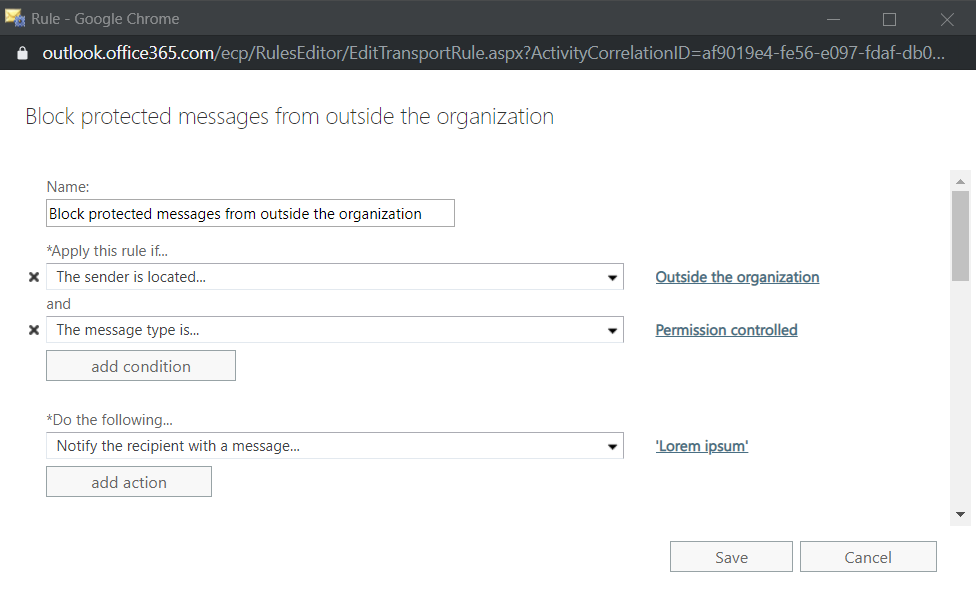
You can also remove any attachments that can’t be scanned in an O365 ATP safe attachments policy:
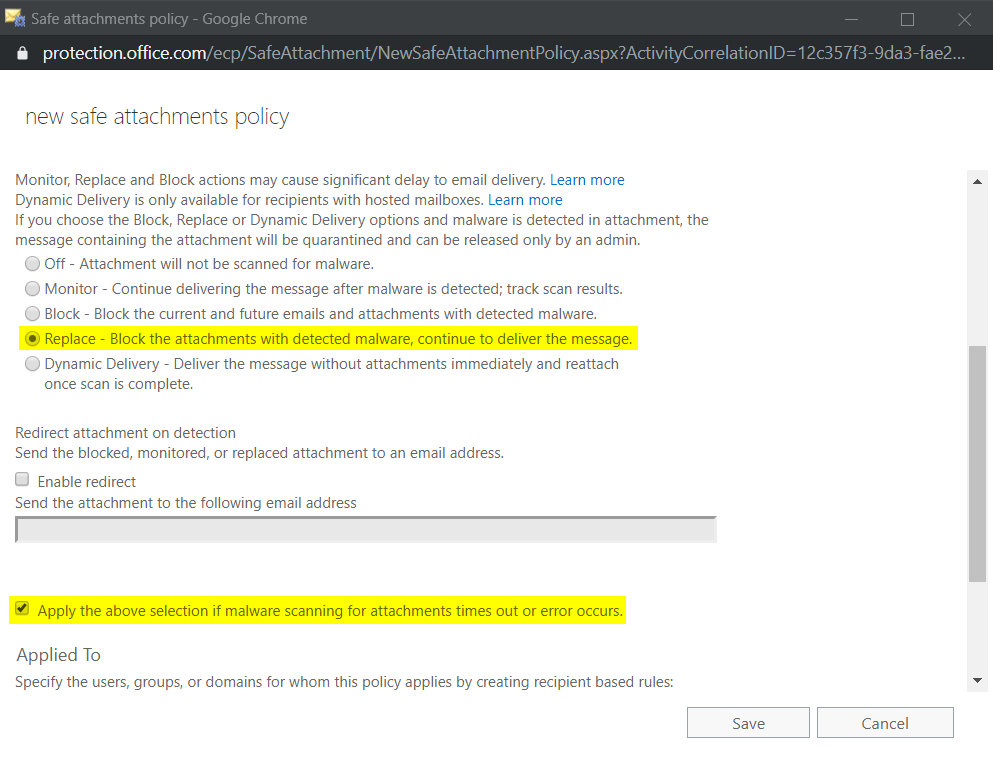
RMS is becoming increasingly important for organizations. What if we can’t block those mails?
Mitigation 2: Harden Microsoft Office and Windows 10
Although Azure Information Protection can also be applied to file formats other than Microsoft Office, they are the most critical for AIP-based attacks as macros and other active content can easily be run. Handling is also much easier: other file types would require the AIP viewer which results in a higher probability that documents are opened. So, assuming that we are not able to block RMS-protected content, what can be done to limit impact on the client side:
- Deactivate Office macros, at least for files from the internet (e.g. via Group Policy: “Block macros from running in Office files from the Internet“)
- If you really need macros: sign them!
- Block active content and child processes from running, e.g. by implementing Attack Surface Reduction (ASR) rules which are part of Microsoft Defender Exploit Guard. There are a couple of rules that target Office and file execution: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/attack-surface-reduction#attack-surface-reduction-rules
- Limit local administrative rights to make it as hard as possible for an attacker to gain persistence on a device.
- Activate Windows 10 Network Protection to block malicious URLs system-wide: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/network-protection
- Enable SmartScreen for Microsoft Edge and File Explorer: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-smartscreen/windows-defender-smartscreen-overview
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-smartscreen/windows-defender-smartscreen-available-settings
Mitigation 3: Use Microsoft Defender Advanced Threat Protection
To tackle malware that was obfuscated by e-mail or attachment encryption, a powerful AV/EDR solution should be in place. While Windows Defender that is natively built into Windows 10 has closed the gap to third party solutions and is now leading the market it is very hard to monitor centrally.
But there’s Microsoft Defender ATP (MDATP) to the rescue! It provides central monitoring, automated investigations, and a complete timeline for each device to investigate incidents. It is also connected to Office 365 ATP via the Microsoft Intelligent Security Graph. Both tools can work together to remediate threats together. So, if O365 ATP was unable to detect a threat, MDATP will mitigate it on the client.
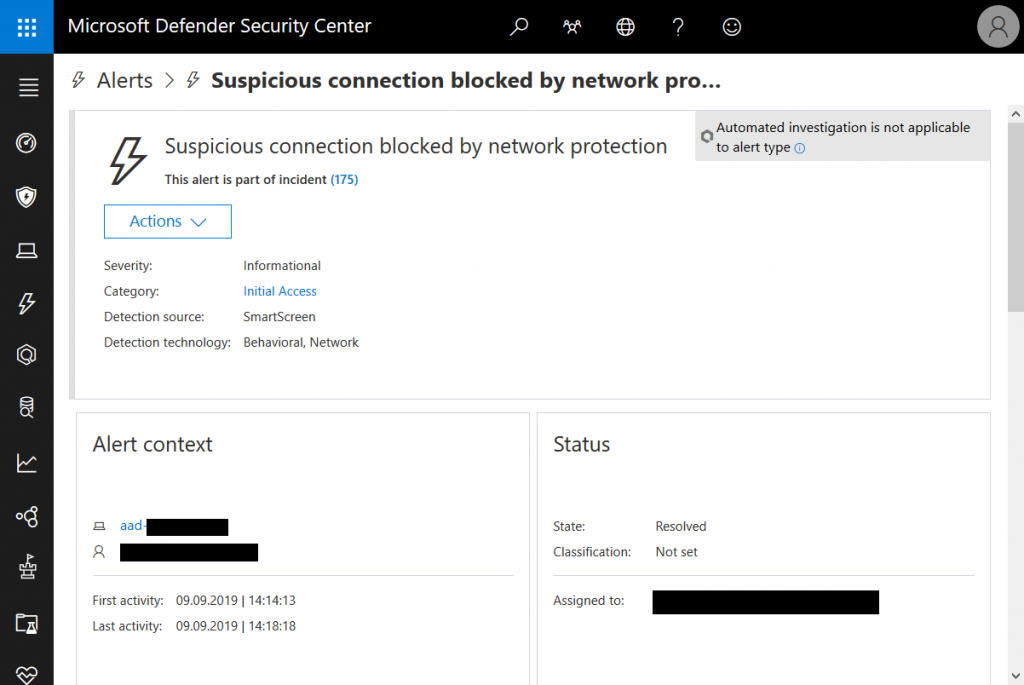
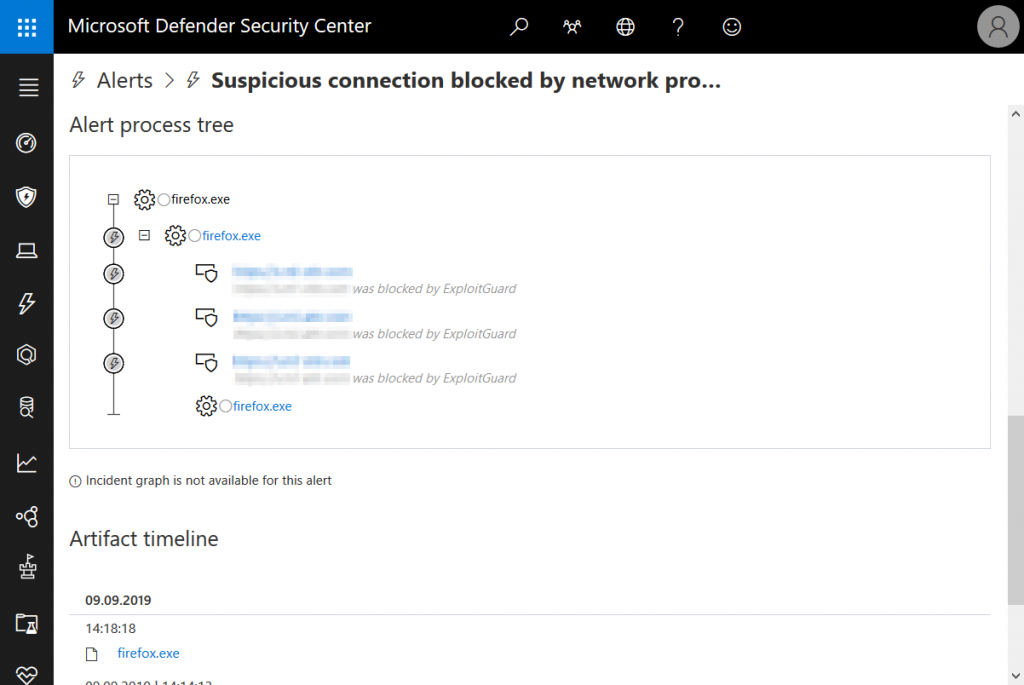
Of couse, MDATP will not only detect suspicious connections but also most if not all kinds of malware – known or unknown.
Mitigation 4: Use Microsoft Cloud App Security and Azure AD Identity Protection to detect phished accounts and malicious activities
Let’s assume it is already too late and the user’s account was phished by a URL that was part of an encrypted document. It’s still not game-over. With Identity Protection in place, and governance controls in MCAS it is still very likely that the attacker’s logon will be detected as an unusual sign-in event.
The best way to investigate those events is MCAS. There, you will be able to dig into the user’s activity log and force them to sign-in again or lock the account. You can also automate those task, of course.
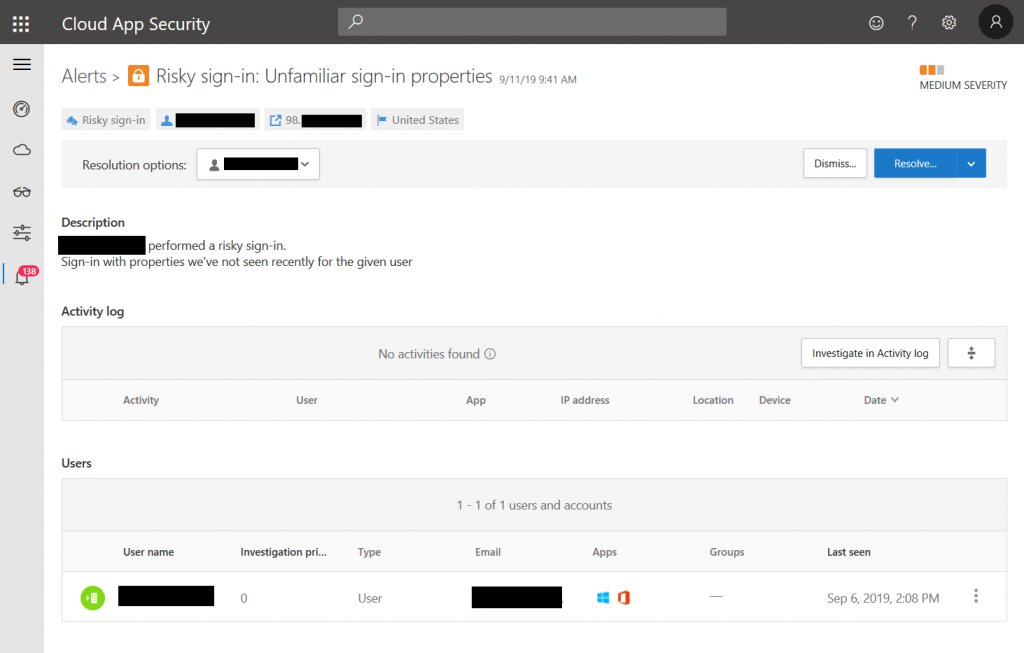
There are different versions of sign-in related alerts, e.g.:
- Activity from infrequent country
- Impossible travel activity
- Risky sign-in: Unfamiliar sign-in properties
- Activity from anonymous IP addresses
- Activity from suspicious IP addresses
To learn more about MCAS you might also want to have a look at this previous post: Microsoft Cloud App Security – 5 reasons to start using it
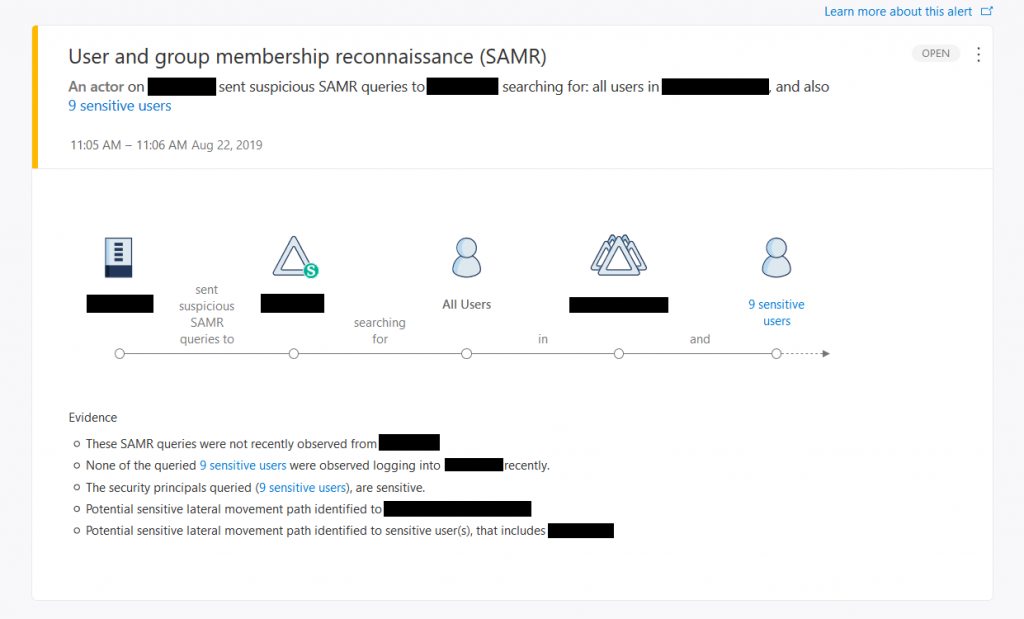
In a hybrid infrastructure, Azure Advanced Threat Protection can also help to detect reconnaissance or active attacks performed by a compromised user account. Here’s an example:
Mitigation 5: Block risky users from accessing cloud apps
Besides MCAS, the user’s risk level can also be applied to not allowing access to cloud apps by using Conditional Access in Azure AD:
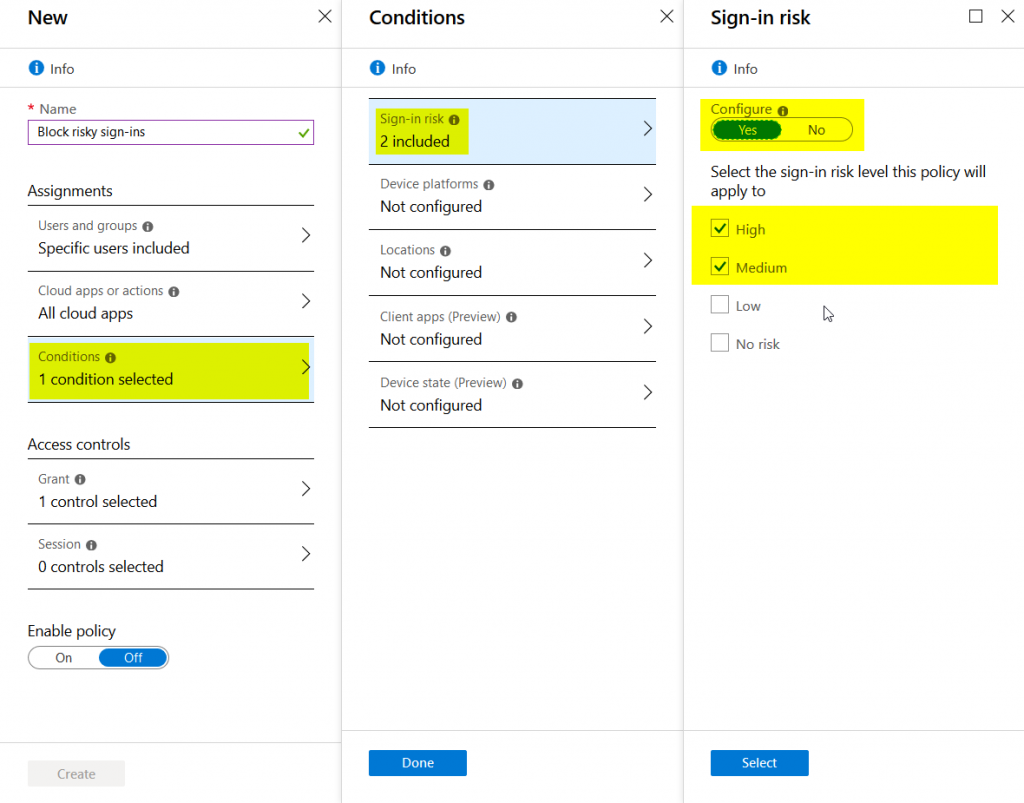
This is just a quick example, of course Conditional Access can be much more granular.
Mitigation 6: Educate users
Besides all technical mitigations, educating users on how to stay safe is still a key factor in IT security. So, make sure not to forget that the human factor often makes the difference between a successful or failed attack.
Summing it up
What I wanted to show with this blog post is that even if a malicious e-mail was not detected (for whatever reasons) there is still a high chance of containing the breach if other defences are in place.
Thanks for reading!
Chris
