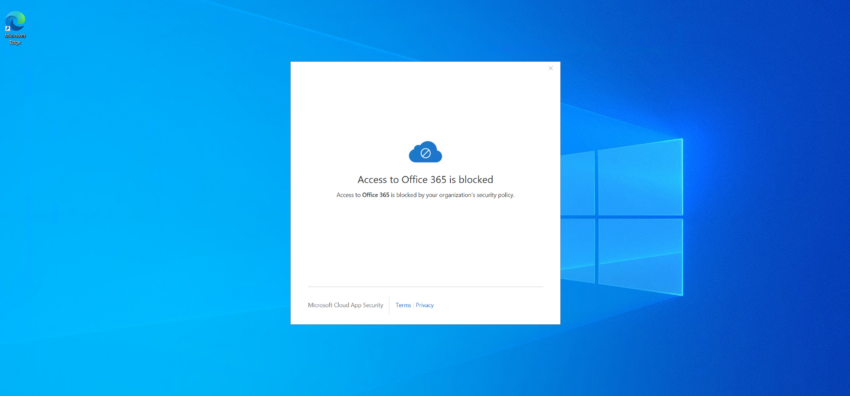
Note Microsoft Cloud App Security (MCAS) has been renamed to Microsoft Defender for Cloud Apps (MDCA) at Ignite 2021. This post does not yet reflect that name change. Conditional Access is great. However, when it comes to managed devices it only allows to check for Hybrid Azure AD join and Intune compliance. With Microsoft Cloud…
Tag: Conditional Access
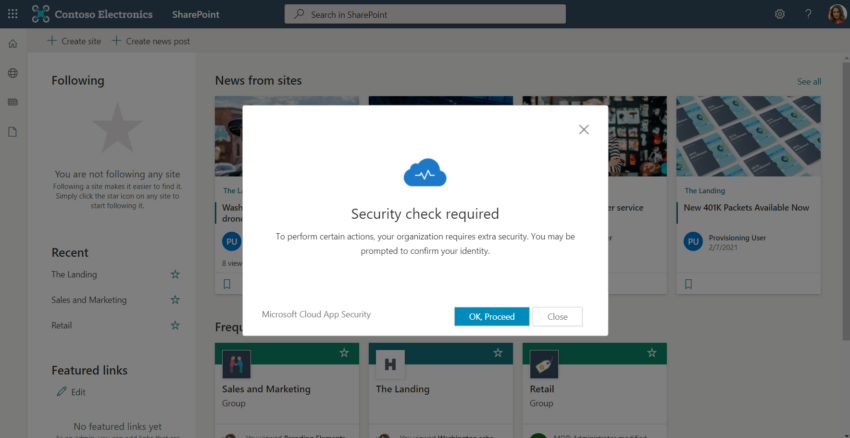
Conditional Access Authentication Context – Protect sensitive data
As part of Microsoft’s Zero Trust strategy, Conditional Access has been the central control mechanism in Azure AD to define which kind of access controls must be fulfilled to access cloud apps that are integrated with Azure AD. However, until now it was not possible to define more granular controls. With Conditional Access Authentication Context…
Build a strong cloud perimeter with Conditional Access
Phew, another article about Conditional Access. That’s right, there a quite a few already. Fortunately, this topic never gets old. Here’s why: In the cloud there are no traditional network perimeters anymore. On-prem appliances are rendered useless as cloud services can be accessed world-wide. All you need is a valid set of credentials to sign-in….
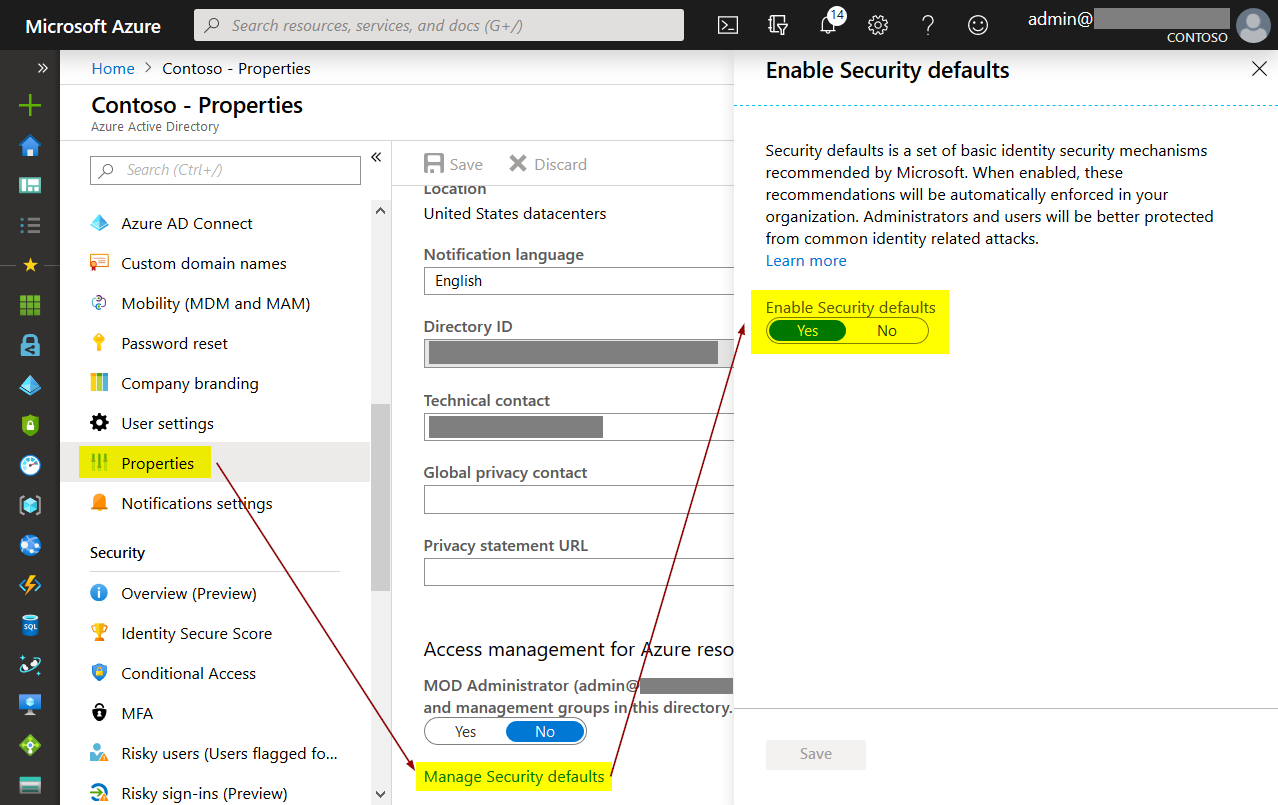
Azure AD Security Defaults – one click and done?
Security in the Microsoft world has never been an on/off switch. Looking back at Windows and especially Active Directory there have always been multiple steps that had to be considered. With the cloud and Azure AD, some companies used the possibility not to start with the same mistakes that were made in the past. Unfortunately,…

Defending against obfuscated malicious content via e-mail
When it comes to cyber attacks, e-mails are still in most cases the initial point of compromise. Users are either lured to enter their credentials on a spoofed website or malware is attached in an obfuscated way. For example, by leveraging Office macros or making the user to “Enable content” which is disabled by default…