Read what’s new for Microsoft Security & Compliance in December 2022 including Azure AD, Microsoft Defender / Sentinel, and Microsoft Purview.
Category: Blog

What’s new: Microsoft 365 Security & Compliance November 2022
Read what’s new for Microsoft Security & Compliance in November 2022 including Azure AD, Microsoft Defender / Sentinel, and Microsoft Purview.
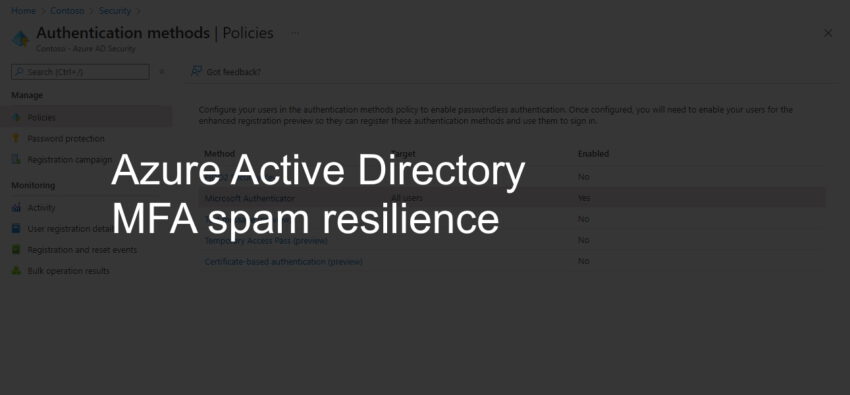
Counter MFA spam attacks with Azure Active Directory
Recently, Microsoft and other vendors have been successfully targeted by the LAPSUS$ attack group using MFA spam as Microsoft describes in this blog post on the MSRC: https://www.microsoft.com/security/blog/2022/03/22/dev-0537-criminal-actor-targeting-organizations-for-data-exfiltration-and-destruction/ Analysis One of the techniques that were used in the attacks is “MFA spamming” which basically means that the attackers prompted users with MFA requests until they…
Windows 11 security – a first look
“Windows 10 will be the last Windows version.” Yeah, not really. Microsoft recently announced Windows 11 being in development with a targeted release in late 2021. Even more than Windows 10, it focuses on a secure hardware root of trust as a foundation for the operating system’s overall security posture. So let’s have a look…
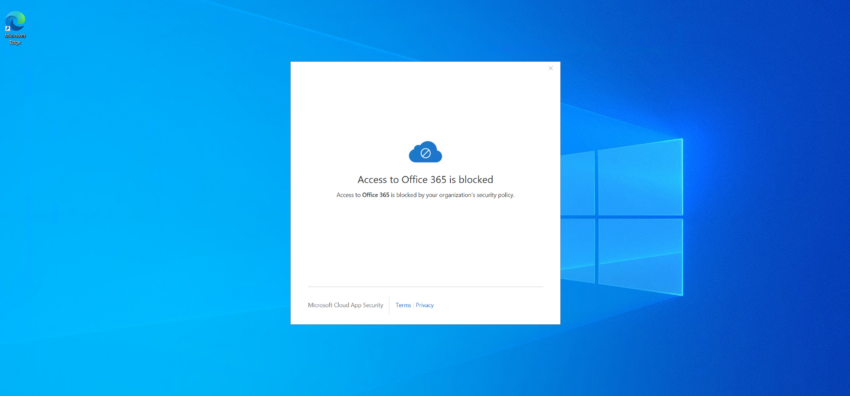
Conditional Access – device identification using certificates
Note Microsoft Cloud App Security (MCAS) has been renamed to Microsoft Defender for Cloud Apps (MDCA) at Ignite 2021. This post does not yet reflect that name change. Conditional Access is great. However, when it comes to managed devices it only allows to check for Hybrid Azure AD join and Intune compliance. With Microsoft Cloud…
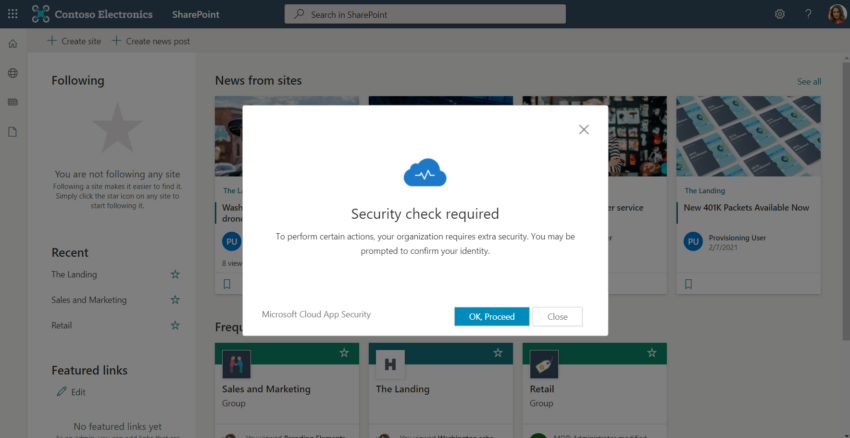
Conditional Access Authentication Context – Protect sensitive data
As part of Microsoft’s Zero Trust strategy, Conditional Access has been the central control mechanism in Azure AD to define which kind of access controls must be fulfilled to access cloud apps that are integrated with Azure AD. However, until now it was not possible to define more granular controls. With Conditional Access Authentication Context…

Microsoft Ignite 2021 – Security News
It’s Ignite time. Again! In this post I cover the Microsoft Ignite 2021 security news that have been announced at the second virtual version of Microsoft’s conference. Azure Active Directory Passwordless authentication is now generally available, Temporary Access Pass (a new feature providing a time-limited code to users) is now in preview. The latter allows…
Microsoft Ignite 2020 – Security News
Microsoft Ignite 2020 has started and with it we already got quite some announcements from the security perspective. In this post, I’d like to give a short roundup of everything that was announced regarding security operations. Microsoft 365 Defender We have a new name for a product family: Microsoft 365 Defender. M365 Defender is an…
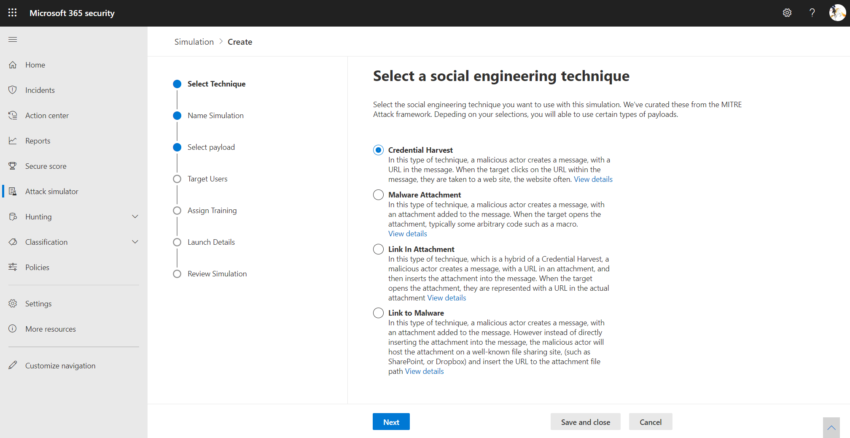
Microsoft Ignite 2020 – Defender for Office 365
You might have heard that Microsoft Office Advanced Threat Protection is now officially called “Microsoft Defender for Office 365” (MSDO). In this post, I’d like to give you a short overview about the MSDO news from Ignite 2020. Threat Protection Advanced Threat Protection is gone but we still got our protection policies. The news being…
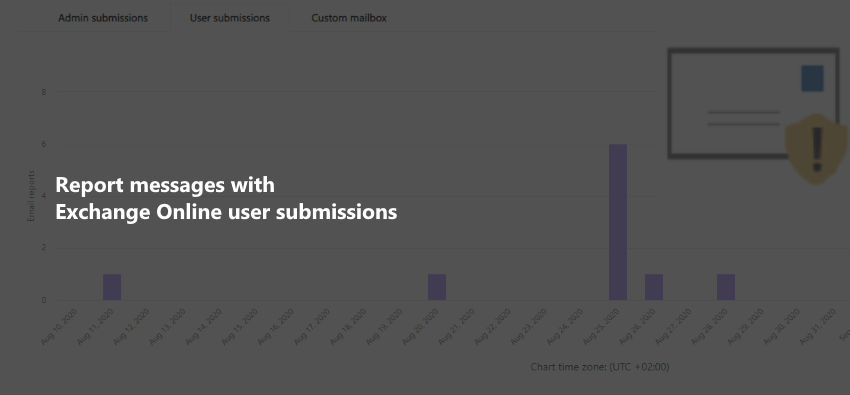
Report messages with Exchange Online user submissions
Note 11/11/2021 This post includes some information and screenshots that do not reflect the current status of the portals. It will be updated at a later date. Mail filtering and security solutions have come a long way since AI and machine learning became mainstream. Still – being highly dependent on reputation levels – no system…
