Note
This post is part of a series about Microsoft Threat Protection. You can find part 2 about unified incident management here: https://chrisonsecurity.net/2020/01/24/microsoft-threat-protection-unified-incidents/
When you work on security incidents, information is key. What is just as important: correlation. The value of data heavily increases if it can be associated with other signals. At Ignite 2018, Microsoft announced “Microsoft Threat Protection” (MTP) as a collective term for their ATP lineup (O365 ATP, Azure ATP, Defender ATP).
Since then, those services grew together more and more. Now, MTP is not only a term anymore and just entered the public preview phase. Advanced Hunting, Automated Investigations, and correlated incidents can now be run across Office and endpoint data.
In this post, I’d like to show the capabilities of unified Advanced Hunting.
Enabling MTP
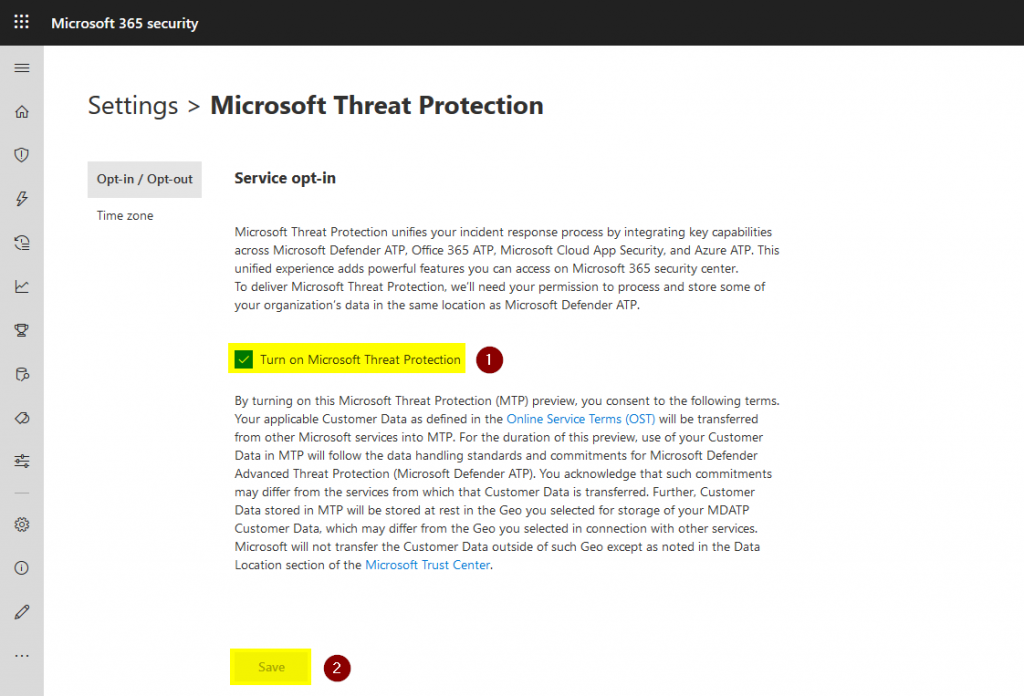
First, you need to head over to the opt-in page that can be found here: https://security.microsoft.com/enable_mtp/mtp_consent
On the settings page, you need to select “Turn on Microsoft Threat Protection” and confirm the selection via the “Save” button.
Note
Please be aware of the service terms Microsoft mention in their description under the opt-in toggle before you enable MTP
After activation, let’s jump over to Advanced hunting at https://security.microsoft.com/hunting
The layout is pretty straight-forward. On the left you get a schema reference (1) to look up table names und columns. Queries are written in the input field at the top right (2), the respective output is shown at the bottom right (3).
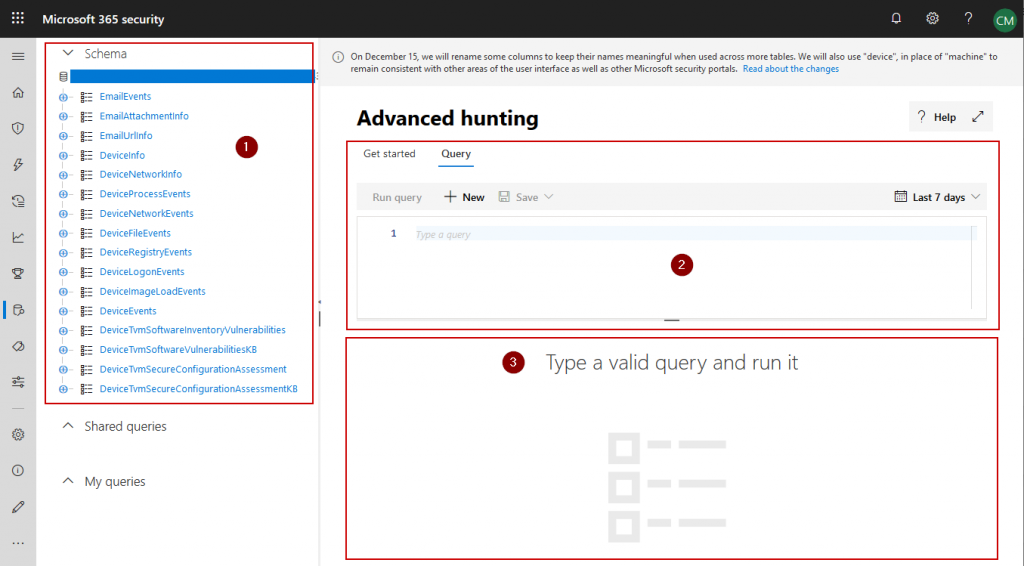
As you can see from the screenshot, like many other services Advanced hunting is also subject to frequent changes. At the moment, Microsoft is working on completing the schema to match the different data sources of Microsoft Threat Protection.
You can find the announcement here: https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Advanced-hunting-data-schema-changes/ba-p/1043914
To put is shortly: the prefix of each table name indicates the data source.
| Data source | Prefix | Example |
| Microsoft Defender ATP | Device | DeviceProcessEvents |
| Office 365 ATP | EmailAttachmentInfo | |
| Microsoft Cloud App Security + Azure ATP | App | AppFileEvents |
If you read this post at a later date, this change is probably already implemented. Every table consists of multiple columns that contain the actual information. E.g. EmailAttachmentInfo holds the following columns:
- Timestamp
- AttachmentId
- NetworkMessageId
- SenderFromAddress
- RecipientEmailAddress
- RecipientObjectId
- FileName
- FileType
- SHA256
- MalwareFilterVerdict
- MalwareDetectionMethod
Every table has different columns, however, sometimes they overlap for the most common info types.
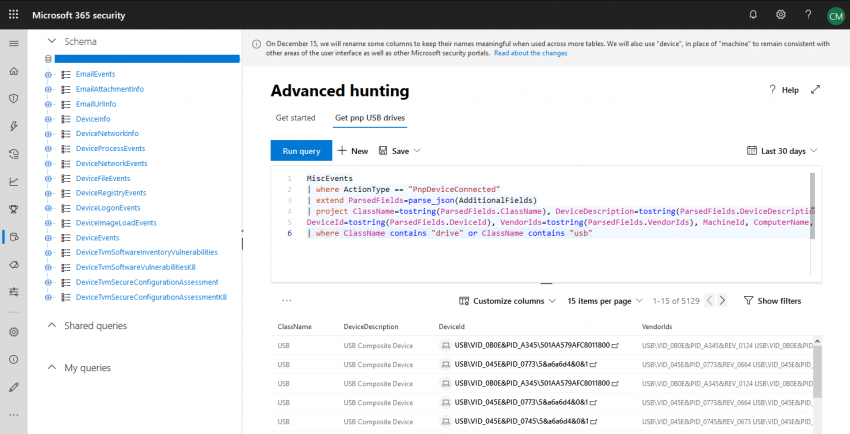
Here is an example on how a query might look like. In this case, it searches for pnp events that are created by mass storage devices:
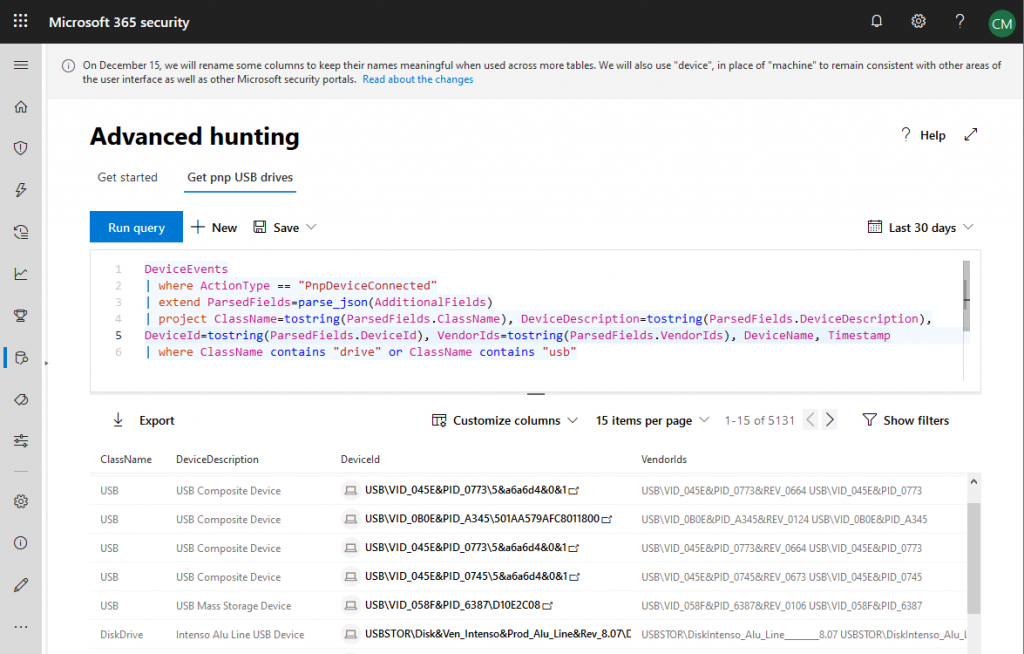
Building you own queries is pretty straight-forward. However, there are some things to learn that are way too comprehensive for a blog post. If you want to know more, there are resources published by Microsoft:
- Short introduction: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/advanced-hunting-query-language
- Full Kusto Query Language (KQL) documentation: https://docs.microsoft.com/en-us/azure/kusto/query/
The MDATP schema
The MDATP Advanced hunting schema has been with us for quite some time now. Besides the renaming to reflect the additions made by MTP, not much has changed.
| Table | Description |
| DeviceInfo | General information about machines, like computer name, OS Build, logged on users, … |
| DeviceNetworkInfo | Network configuration of machines (adapters, IP and MAC addresses, …) |
| DeviceProcessEvents | Process creation and related events |
| DeviceNetworkEvents | Network connection events |
| DeviceFileEvents | Events related to file creation, modification, … |
| DeviceRegistryEvents | Creation and modification of registry entries |
| DeviceLogonEvents | User logon and authentication events |
| DeviceImageLoadEvents | DLL loading events |
| DeviceEvents | Various device events, especially regarding security controls (Application Control, Windows Firewall, etc.) |
| DeviceTvmSoftwareInventoryVulnerabilities | Software inventory and vulnerabilities provided by Threat & Vulnerability Management (TVM) |
| DeviceTvmSoftwareVulnerabilitiesKB | List of vulnerabilites from TVM |
| DeviceTvmSecureConfigurationAssessment | Assessment events for specific security configuration from TVM |
| DeviceTvmSecureConfigurationAssessmentKB | Information about secure configurations (includes risk information, industry benchmarks, and MITRE ATT&CK techniques) |
The OATP schema
The Office 365 ATP schema has been added with the (preview) release of MTP. It uses Office 365 mail data.
| Table | Description |
| EmailEvents | General information about email |
| EmailAttachmentInfo | Information about email attachments |
| EmailUrlInfo | Information about URLs in emails |
Note
If you want to learn more about mail hunting have a look at Alex Verboon’s blog post: Microsoft Threat Protection – Using advanced hunting to see what’s going on with your mail.
Useful queries
Microsoft publishes some queries on their official GitHub repository: https://github.com/microsoft/WindowsDefenderATP-Hunting-Queries
I am not a big fan of listing predefined queries as they must be adapted to your own environment in most cases anyway. However, here are some use cases that can be enhanced by Advanced Hunting:
- Monitor your Windows Firewall configuration by using data from the DeviceNetworkEvents table
- Monitor your Application Guard / AppLocker configuration by using the DeviceEvents table
- Use EmailEvents, EmailAttachmentInfo, and EmailUrlInfo to monitor Office 365 ATP actions, such as delivery actions, detected malware and phish, and URL information from ATP safe links. I personally find Advanced Hunting way more convenient than using the Threat Explorer in the “old” Security & Compliance center.
- You can also use hunting to detect if users have overwritten security warnings triggered by SmartScreen. e.g.
- If you are unable to block external mass storage devices you can use hunting to detect bulk data exfiltration. This can be used to be part of you general DLP configuration.
- Check update status for OS and anti-virus.
- Monitor local administrators, and administrative logons.
- Of course, you can also just search for indicators of compromise in the whole company if a particular incident occurred.
In a future post, I will cover some of those scenarios in more detail.
Conclusion
Knowledge is power: nothing describes better what Advanced Hunting in Microsoft Threat Protection offers to security personnel. Many scenarios were already covered in Defender ATP, however, with the addition of Office 365 ATP data (followed by MCAS and Azure ATP in the future) you can now use it for centralized queries across your major cloud-powered defenses.
Thanks for reading!
Chris