Note
This post is part of a series about Microsoft Threat Protection. You can find part 1 about unified hunting here: https://chrisonsecurity.net/2019/12/15/microsoft-threat-protection-unified-hunting/
In my last post about Microsoft Threat Protection (MTP) I talked about unified hunting where you can use data signals from Defender ATP, Office ATP, and (coming soon) MCAS / Azure ATP to build queries. If you want to learn how to enable MTP follow the link above.
Now, let’s have a look at another feature of MTP: unified incidents. You can find them using the direct link to the new Microsoft 365 Security portal: https://security.microsoft.com/incidents
Let’s jump right in, what can we see there? Unified incidents are very similar to incidents in Microsoft Defender ATP. That’s why we get basic information like incident names, severity, categories, number of (active) alerts that have been aggregated, impacted entities (devices, users, apps, …).
Of course, every incident can be investigated further. This gives you additional information about each column of the table.
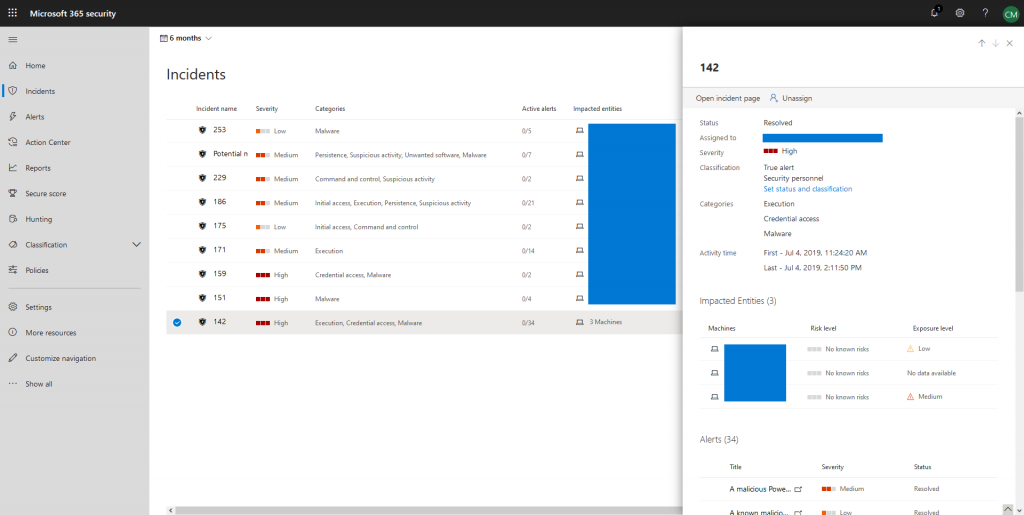
Incident details
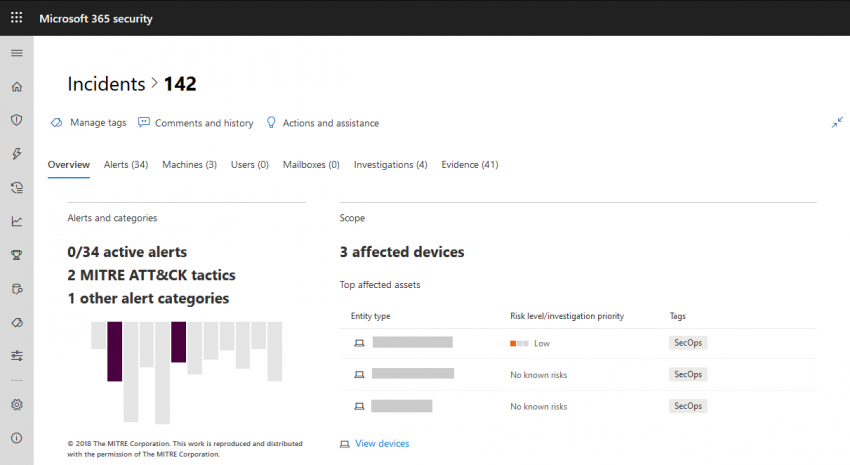
Now let’s have a look at a single incident:
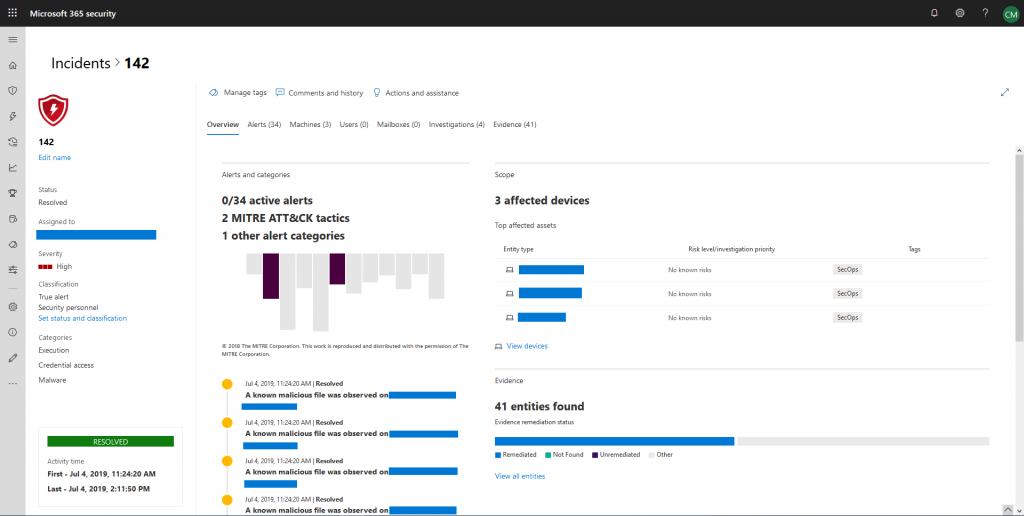
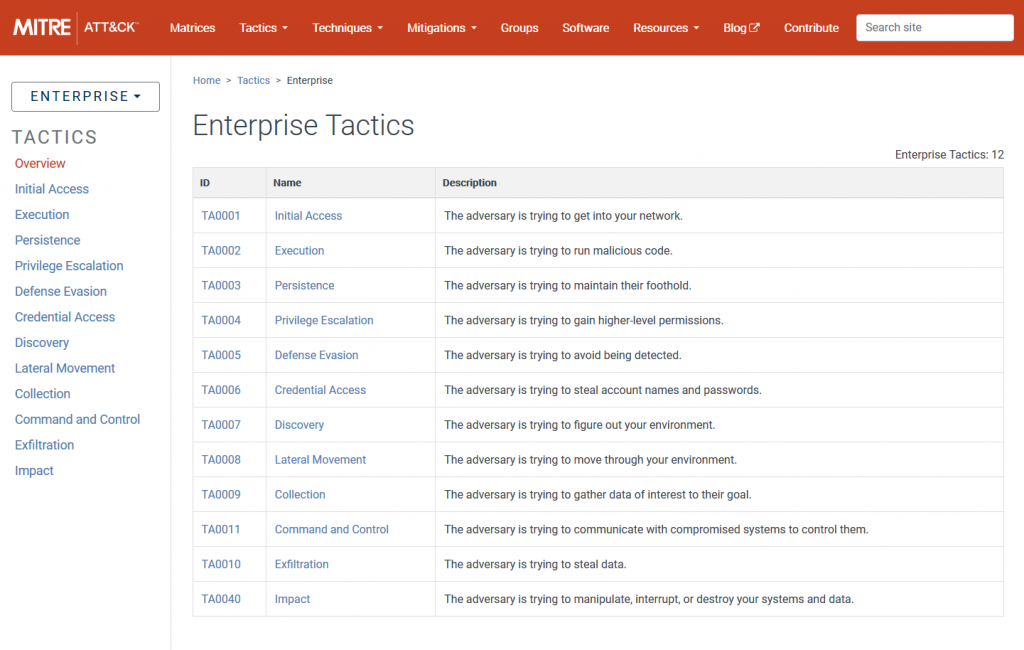
What you’ll notice right away is the new overview panel which does not exist in MDATP incidents. What you get is – again – a quick view at all relevant facts. The vertical grey and purple bars on the left give you attack tactics that were used at a single glance. They are based on MITRE ATT&CK. Each bar represents a different type of attack tactic from their enterprise matrix:
Now we can have a more detailed look at the tabs: Alerts, Machines, Users, Mailboxes, Investigations, Evidence.
Alerts
Alerts are the main entities that are combined to different incidents. The idea is to correlate single events to get an idea about what really happened. A single event may easily be overlooked, however, if you can see that there were in fact multiple affected systems, mailboxes, etc. the big picture becomes obvious. This saves valuable time.
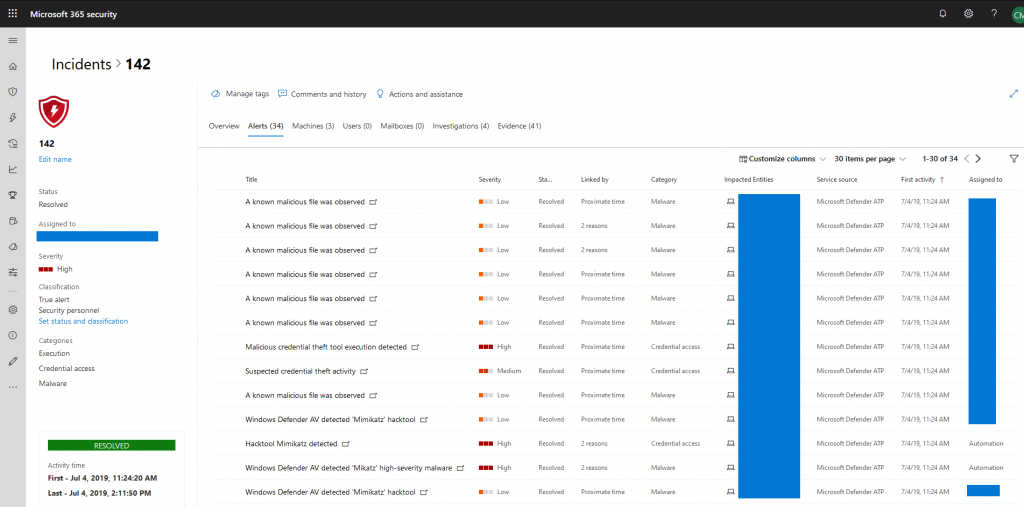
I think it is quite tiring to describe screenshots by text, however, as you can see from the picture, alerts also give you all relevant information. You can go further and investigate each alert. As you may have noticed: each alert title contains a symbol at the end. That’s because you will be forwarded to MDATP for full alert details.
Investigations
Microsoft also provides automated investigations for incidents / alerts. In this case, you can see some coming from MDATP. Automated investigations are intended to provide automated remediation capabilities to Microsoft Threat Protection. In collaboration with – e.g. – Microsoft Defender on Windows endpoints, they will search for additional signals that might indicate compromise and clean up local files, services, etc.
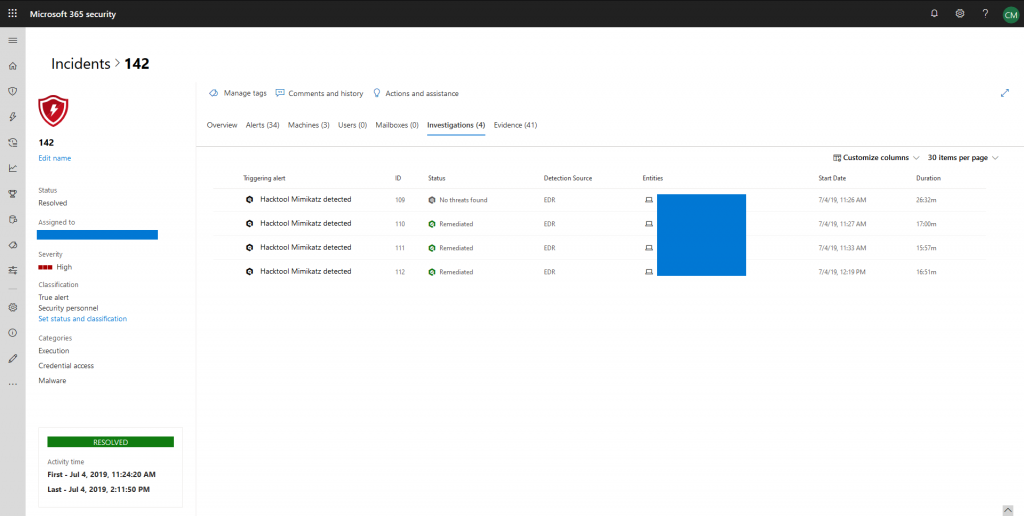
As with all incident related entities you get an overview of relevant facts:
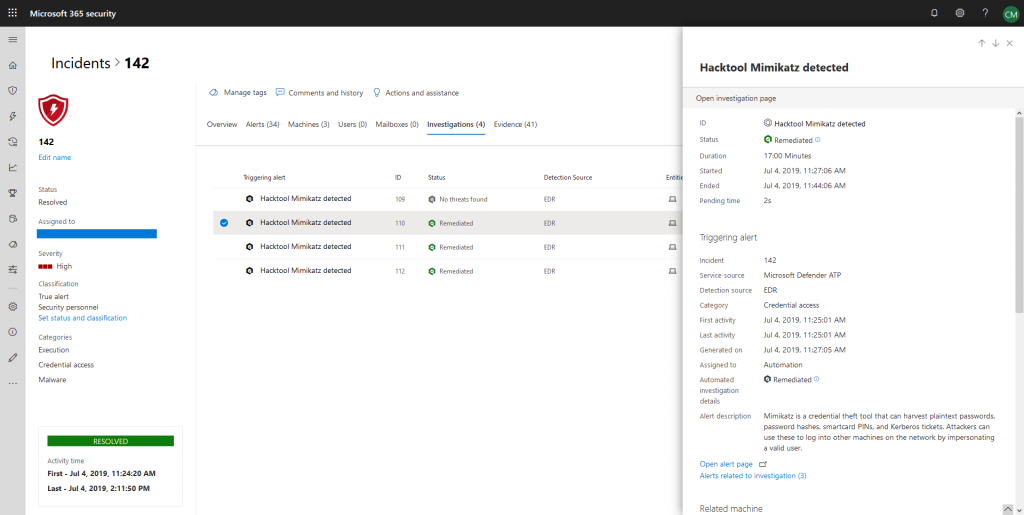
Unlike alerts not being available in the Microsoft Security portal, you can fully explorer automated investigations here:
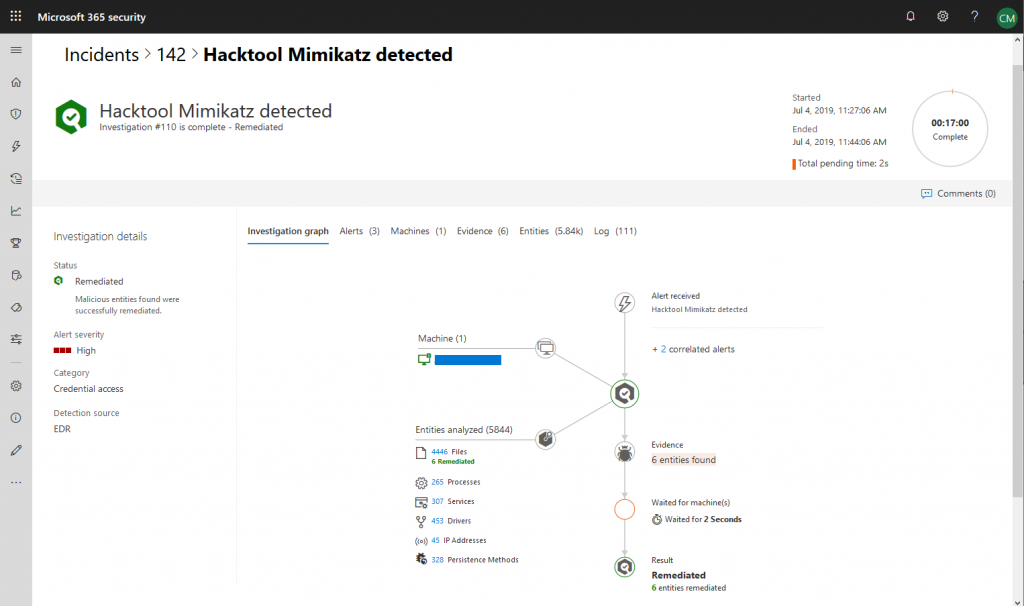
What you need to consider: like incidents (the main topic of this post), automated investigations also group single alerts. If you are a SecOps engineer that works with MDATP or MTP it might take some time to get an understand on where to look first.
Microsoft Threat Protection aims to fix this issue, but it can not replace the necessity of training and some basic understanding.
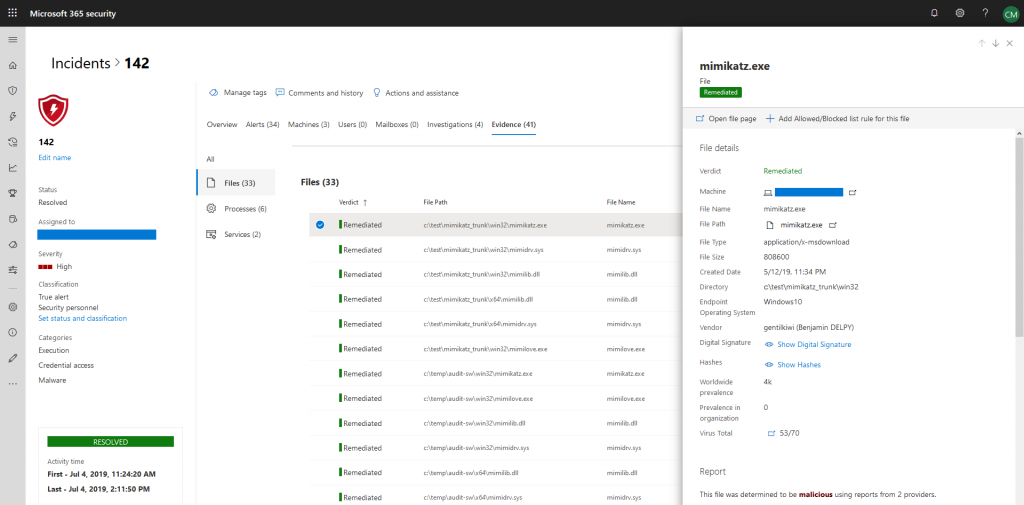
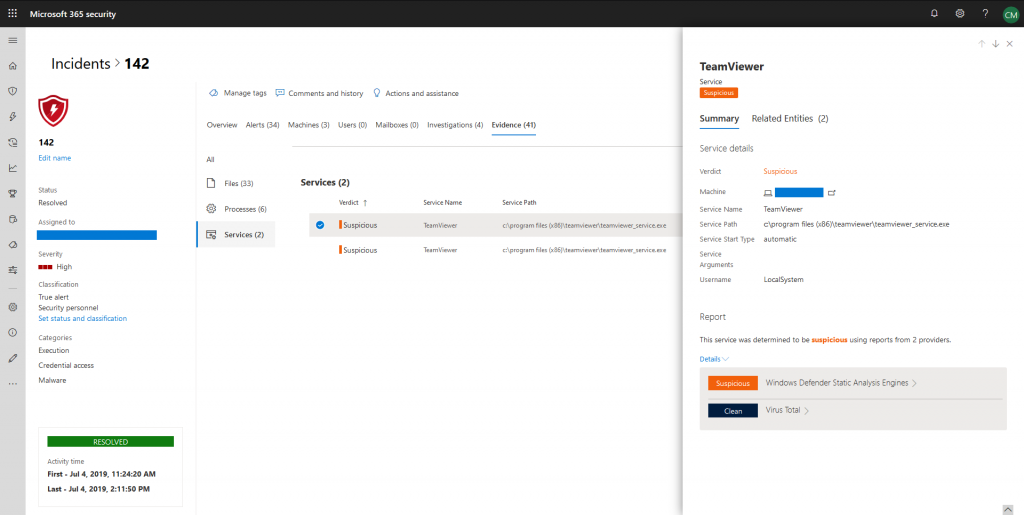
Evidence
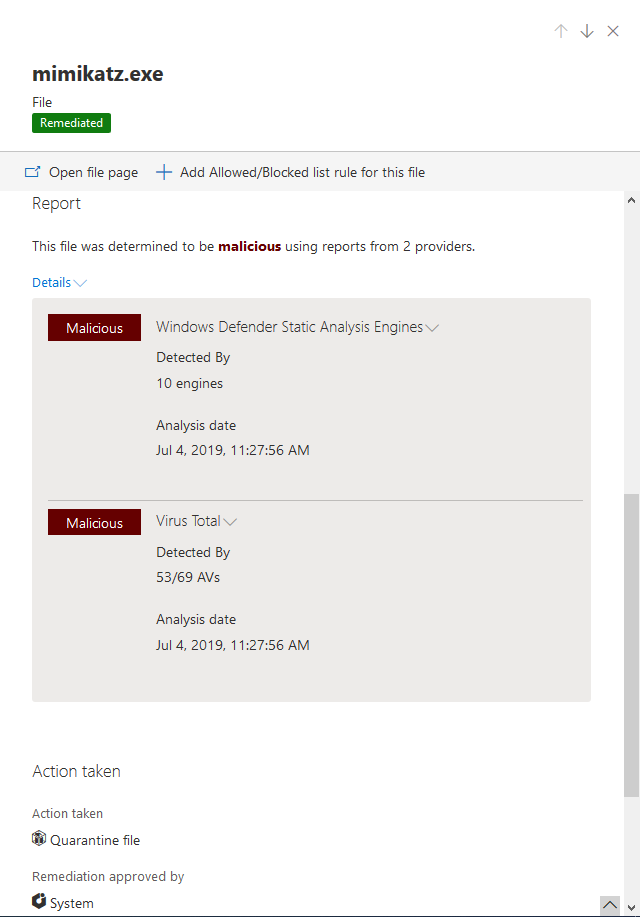
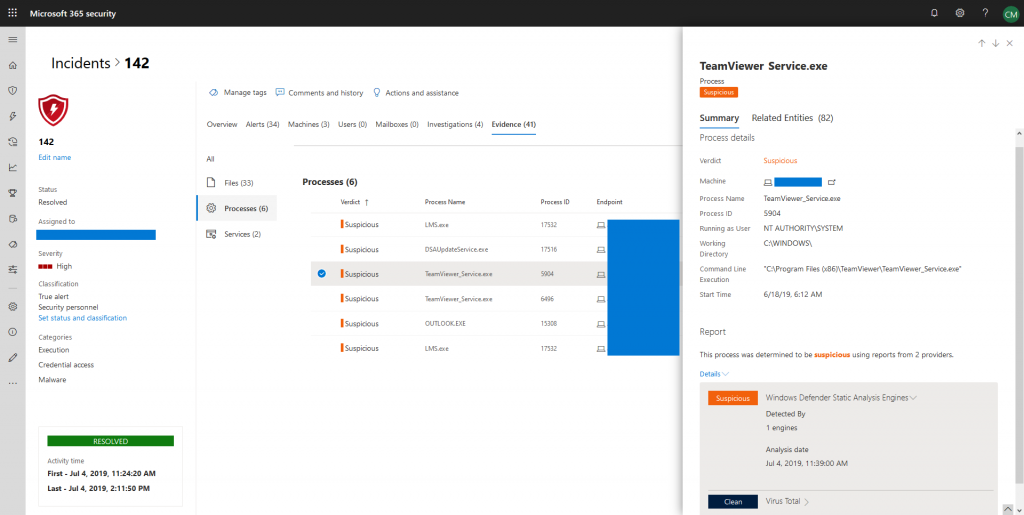
Lastly, incidents also provide evidence about events. This is one of the most useful features as you are able to review affected files, processes, and services at a single location. Each evidence entity is enriched with additional data, like digital signatures, file hashes, vendors, etc. As I already pointed out, describing every little detail of a dashboard of a security tool with this level of sophistication is really tiresome.
So, I let some screenshots speak for themselves:
Notes from the field
Some additional comments on unified incidents:
- Microsoft Threat Protection has multiple data sources (MDATP, OATP, MCAS, AATP, Azure AD, Microsoft Information Protection): define responsibilities and train employees to work with all those tools. Especially, if they need to respond to incidents.
- As I mentioned in part 1 of my MTP series: Microsoft Threat Protection is currently in preview. There will be enhancements and fixes (although it already works pretty well).
- Incidents, alerts, automated investigations: all those entities can have an impact on how to react to threats – learn how to work with those. Unfortunately, this takes time and time spent on it (more than a blog post can teach you).
- Incidents and alerts can be resolved individually. Define who classifies and resolves them.
- Always keep in mind that Microsoft Threat Protection definitely focuses on the “threat” part. It gets enriched by identity & access telemetry as well. However, a comprehensive cloud security concept needs additional consideration, especially regarding data governance. If you want to learn more about M365 security feel free to have a look at my security baselines:
Conclusion
Everyone working with Microsoft 365 knows the trouble: there are dozens of dashboards and features. While many products can be administered separately, security knows no boundaries. In order to prevent security personnel from having to look at various locations, Microsoft Threat Protection has done a great job to centralize incidents in the new Microsoft 365 Security portal. A welcome change to get information more quickly.
Thanks for reading!
Chris