Controlling clients at the network level has been a use case for many companies for the last decades. In most cases, local network infrastructure like proxies or firewalls are used to control which resources can be accessed by a client. What if devices are on the road? In the cloud, this concept has been adapted by third-party solutions like ZScaler (and many others) using a cloud endpoint as a gateway to enforce policies. Both solutions create a significant overhead.
Luckily, Microsoft Defender ATP now offers functionality to satisfy those use cases at the client level:
- Blocking unsanctioned apps as defined in Microsoft Cloud App Security
- Defining custom Indicators (IP addresses, URLs, domains)
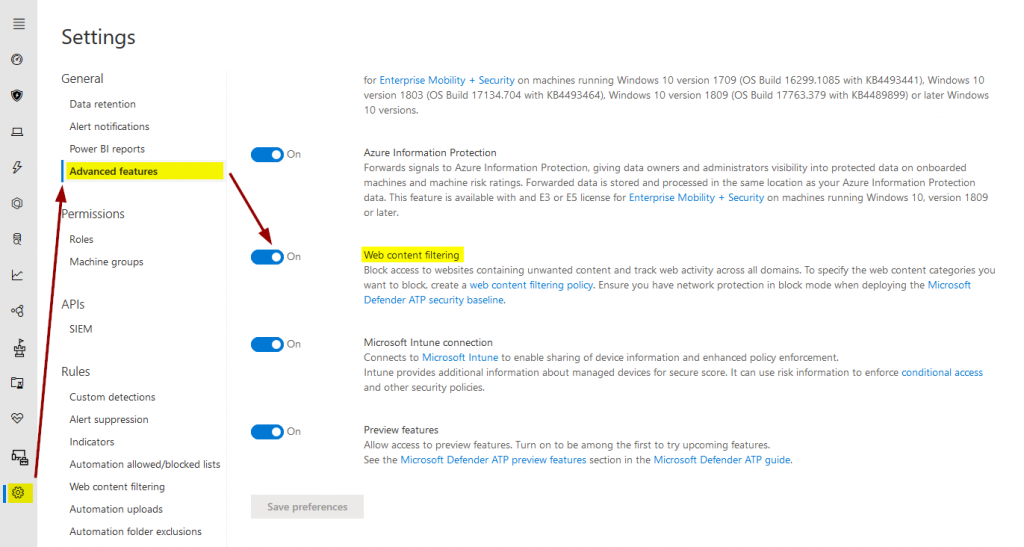
- Using web content filtering to block access to websites containing unwanted content and track web activity across all domains.
Requirements
All functions are based on Windows Defender Network Protection: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/network-protection
By default, network protection blocks HTTP(S) access attempts to resources with low reputation as defined by Microsoft. Moreover, it is the technological basis for all following features.
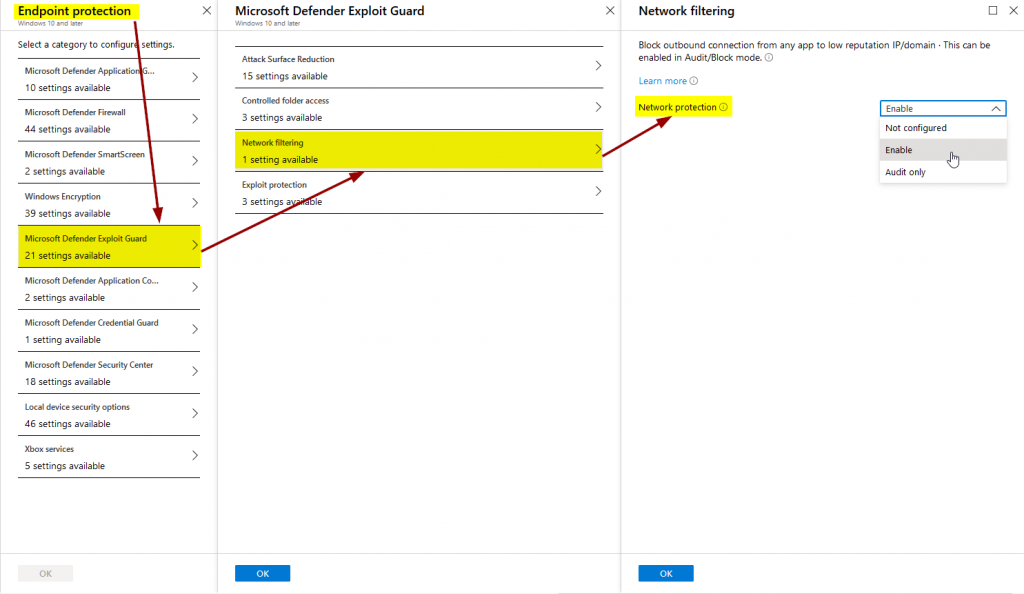
It can be enabled via either Group Policy or an Intune configuration policy. For all scenarios it must be set to block mode.
Group Policy:
Computer configuration > Administrative templates > Windows components > Windows Defender Antivirus > Windows Defender Exploit Guard > Network protection > “Block”
Intune:
Blocking unsanctioned apps via MCAS
As a Cloud Access Security Broker (CASB), Microsoft Cloud App Security provides visibility and insights about usage of cloud resources by using data from either log uploads of network infrastructure (firewalls and proxies, e.g.) or signals from all Microsoft Defender ATP endpoints.
The latter can now also be used to enforce blocking of cloud apps that have been marked as unsanctioned (= unwanted) in MCAS.
All we have to do is enable the connector in MDATP…:
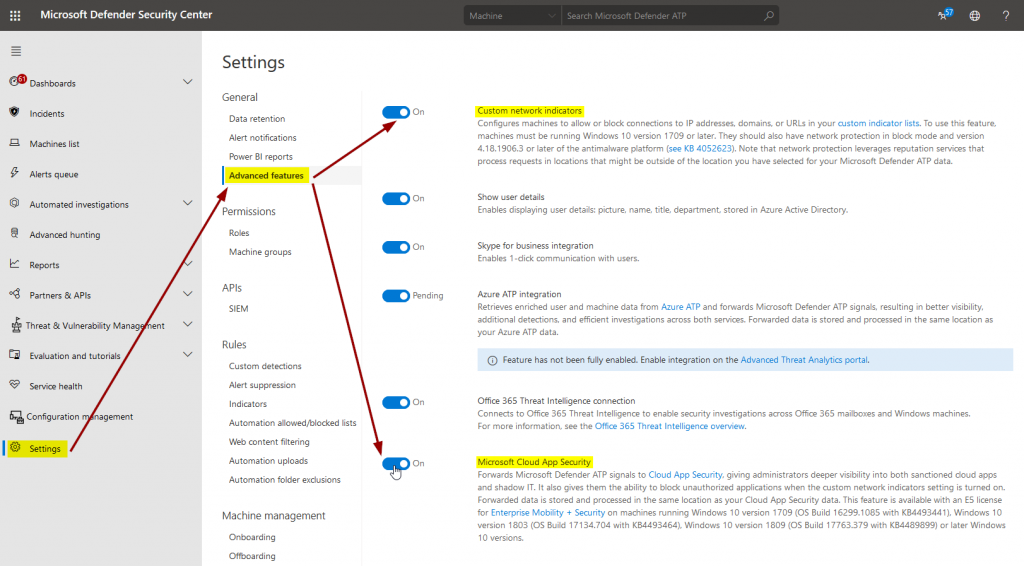
… MCAS …:
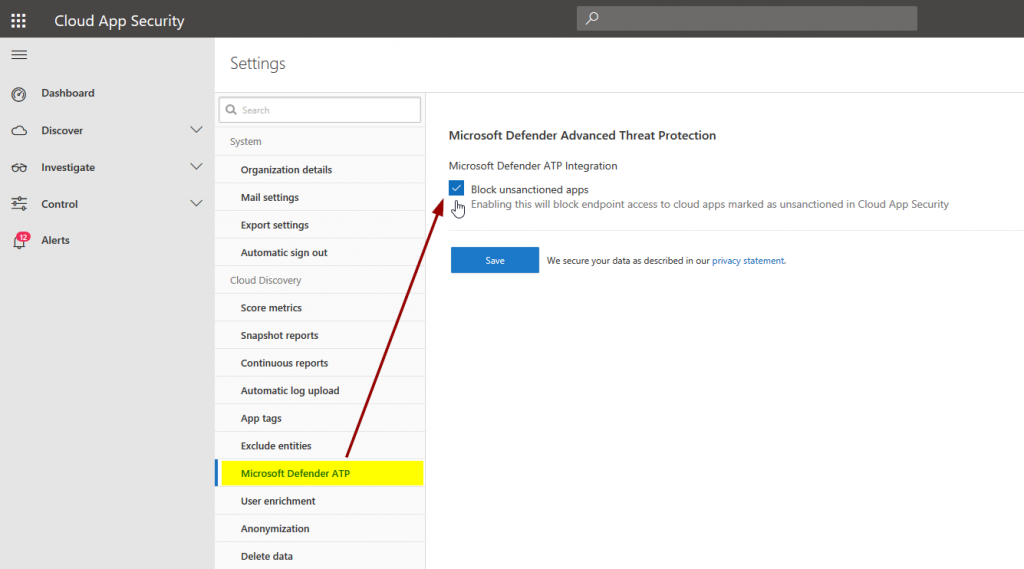
… and mark one or more cloud apps in MCAS as unsanctioned to test functionality:
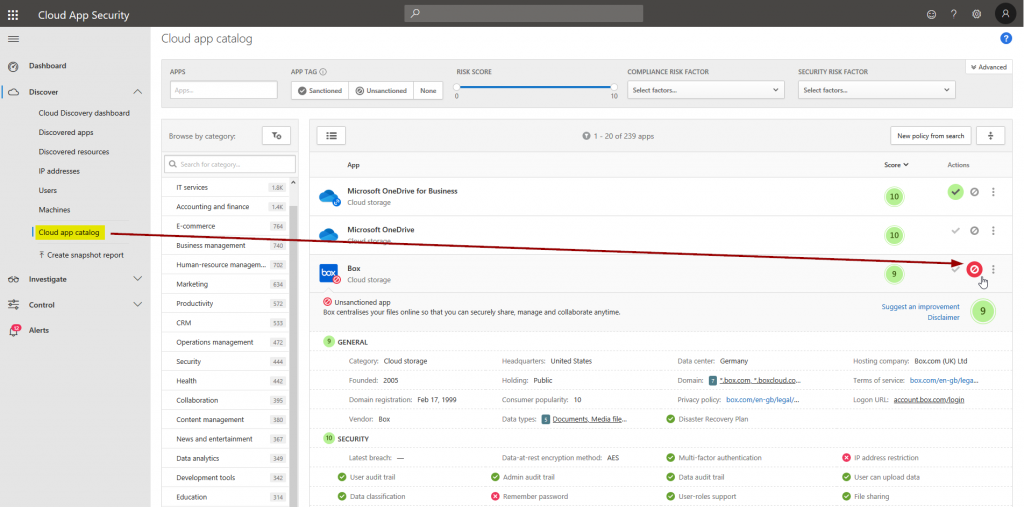
After a short period of time MDATP will sync that information …
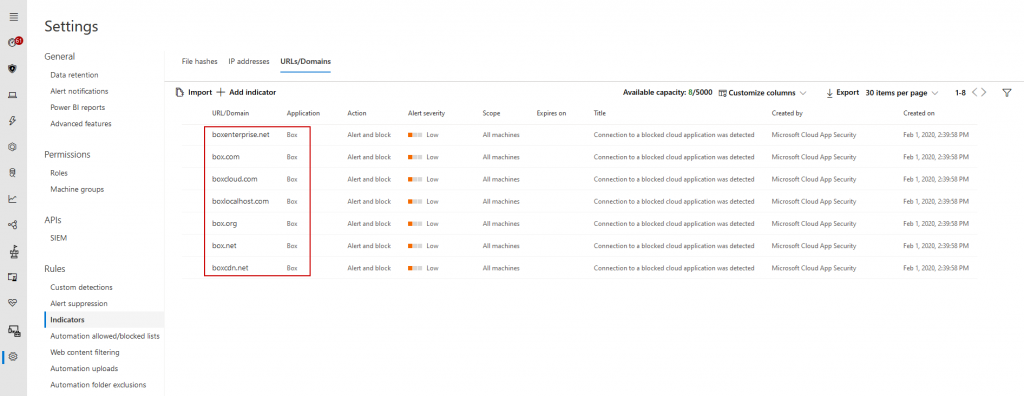
… and block those apps (thanks to Network Protection) independent from the browser that is used. In Microsoft Edge, users get a quite useful error message.
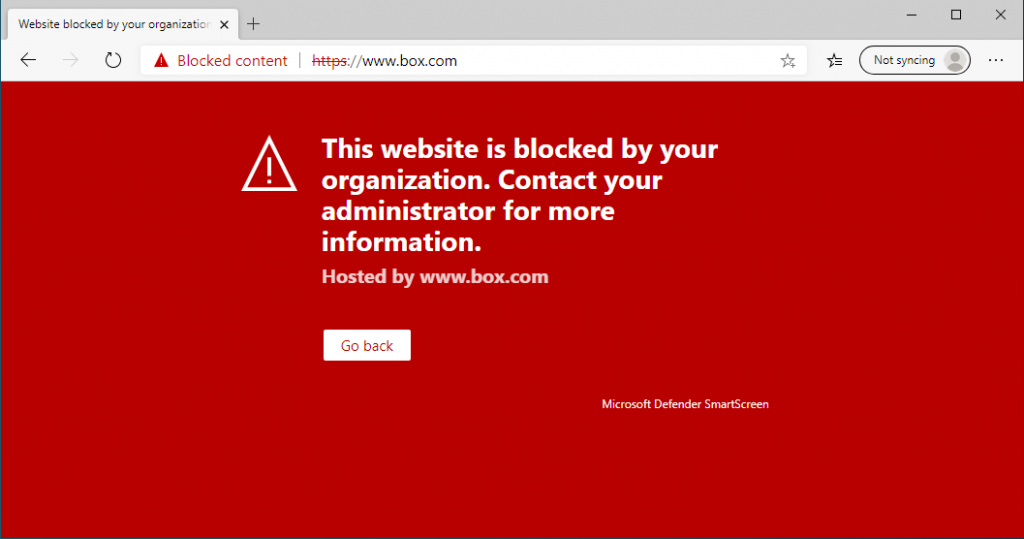
Other browsers just show a generic HTTPS error:
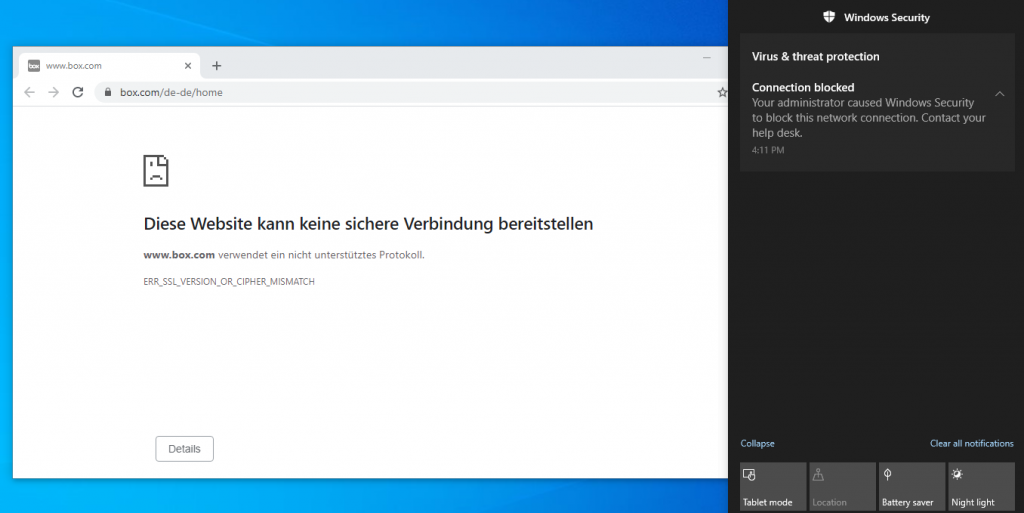
Blocking custom resources in MDATP
MCAS is not the only data source that allows blocking. You can also use custom network indicators to enter specific custom IPs, URLs, or domains. This comes in handy if MCAS does not list a certain cloud app or website.
Again, Network Protection must be active on endpoints as described previously. You also need to enable custom network indicators in the MDATP portal as shown in the MCAS scenario.
We may then go ahead and enter indicators:
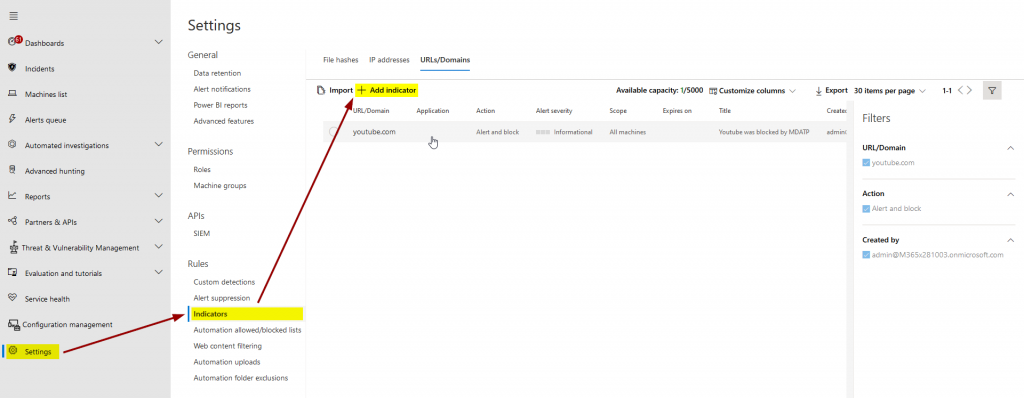
As always: the examples I use for my blog posts are completely random. YouTube is great. 😉
After a short delay (maximum of 2 hours), MDATP will now also enforce those settings:
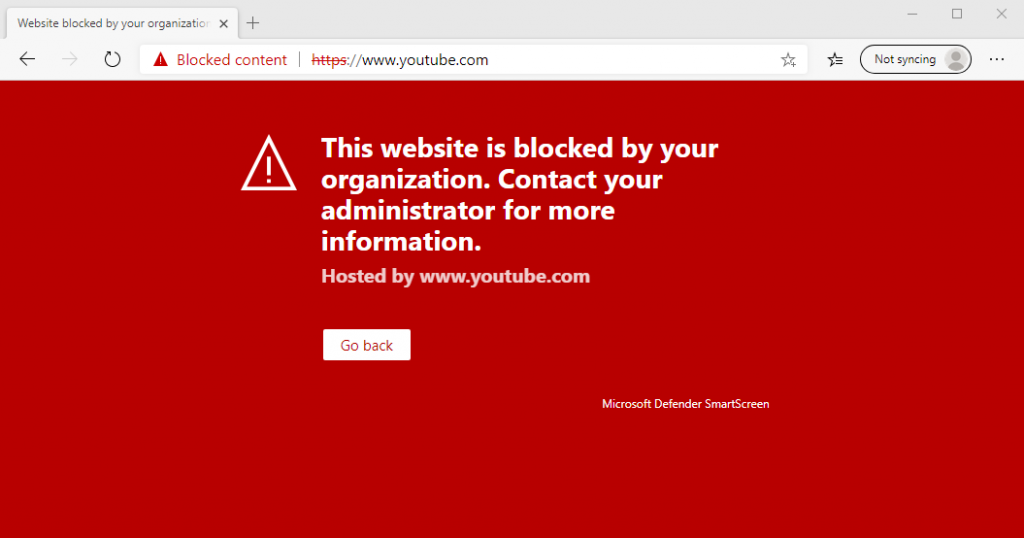
Blocking unwanted content
Now let’s talk about the newest addition to MDATP: web content filtering. The concept is not new: like many third-party tools MDATP can now also block web resources from certain categories like sexual content or gambling.
Note
I previously described that a third-party Cyren license was needed for web content filtering to work. Luckily, in July 2020 Microsoft just announced that this functionality will be built right into Defender ATP without any further cost.
I therefore removed the part about Cyren onboarding from the post.
Again, we need to head over to the settings to enable web content filtering:
We will then proceed to select the categories that should be blocked under the “Web content filtering” menu:
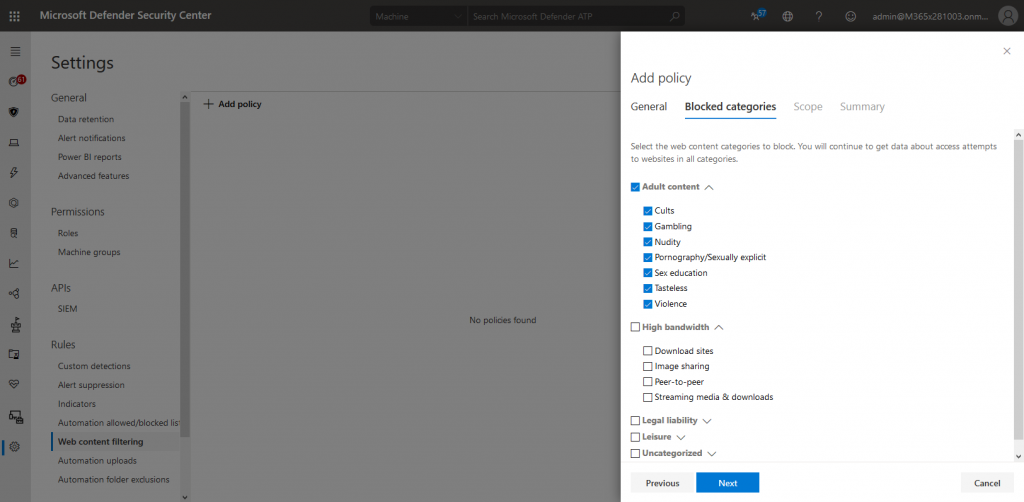
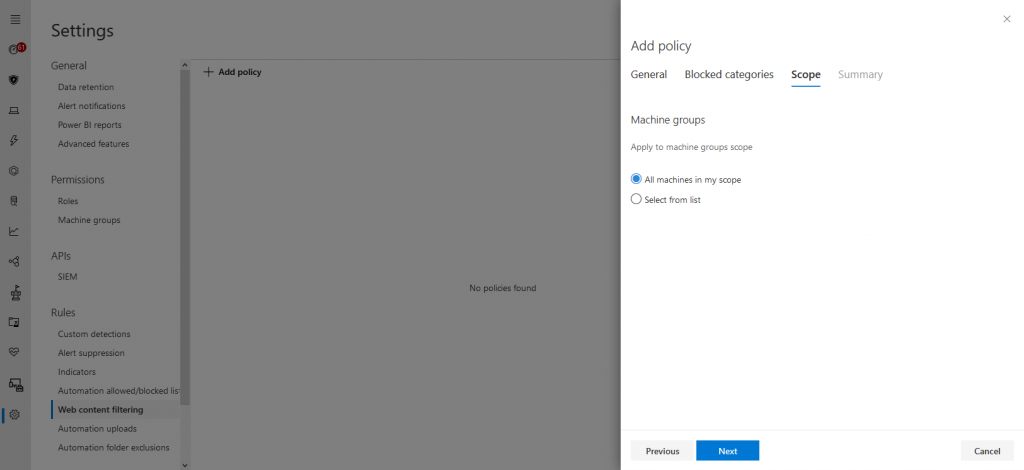
Of course, the policy will appear in the list after creation:
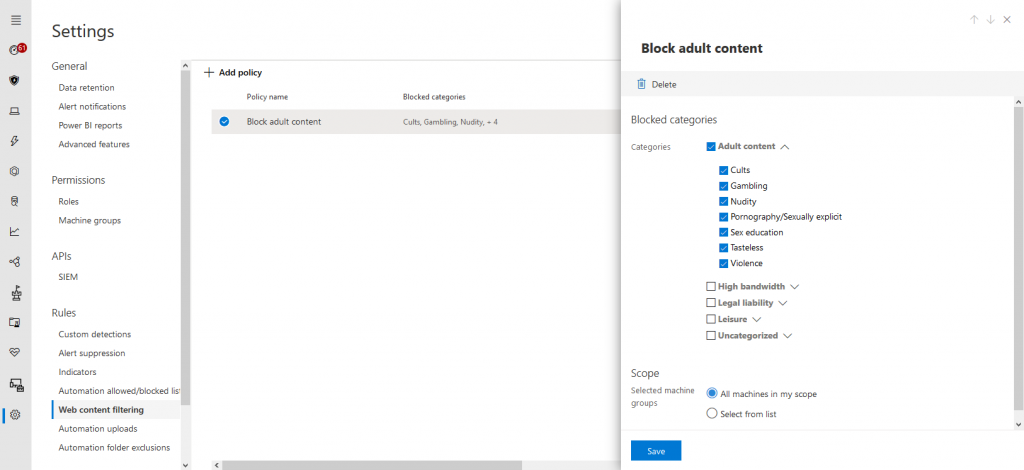
I then went ahead and tried to visit an online casino:
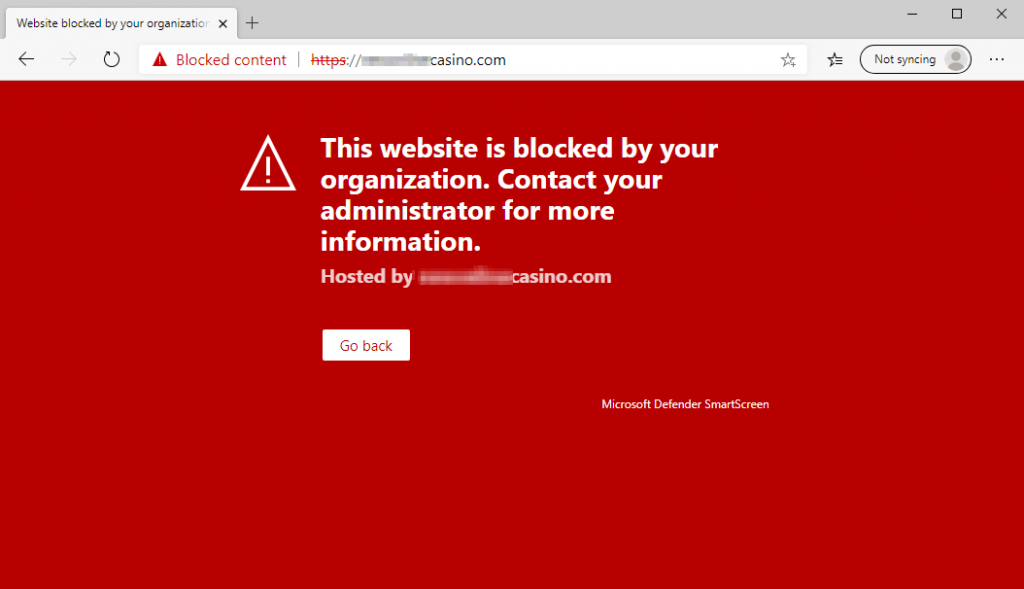
Browsers without SmartScreen also block it via Network Protection:
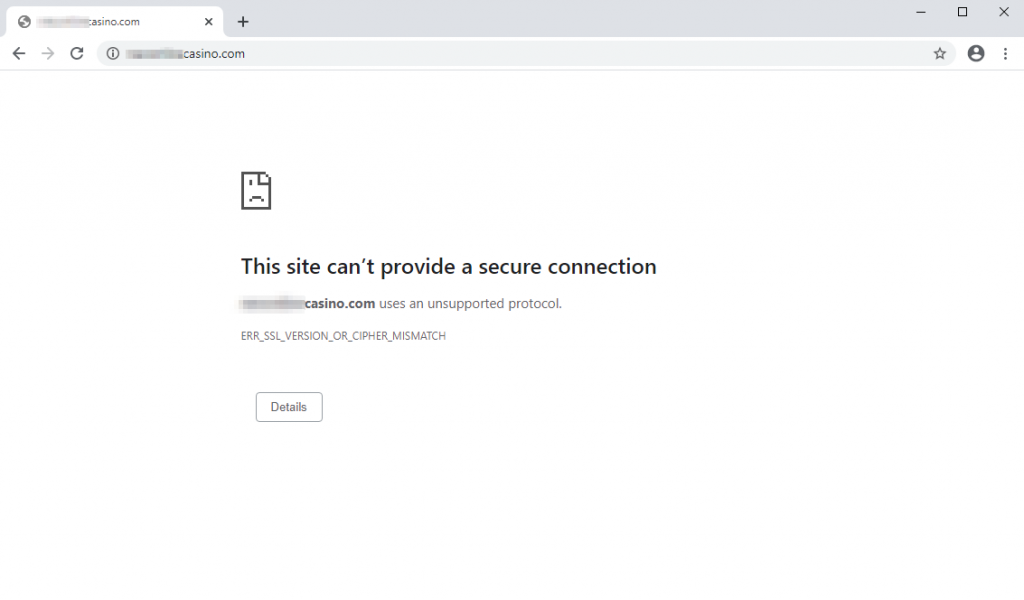
Mission accomplished!
Summing things up
Personally, I think it is really incredible to watch the progress the MDATP team achieves in such a short time. Defender ATP has been a great EDR tool right from the start, with enhancements like Threat & Vulnerability Management and now full network control its usefulness only increased. I’m looking forward to what’s yet to come.
Thanks for reading!
Chris
