Microsoft Defender ATP for Linux is here! Again, Microsoft expand their MDATP ecosystem to match the commitment to open source and operating systems other than Windows (Server). Azure resources are heavily depending on Linux, so this is a logical next step.
In the course of 2020, MDATP’s capabilities will also be extended to iOS and Android. But for now, let’s have a look at MDATP for Linux.
Getting ready
Make sure you are running a supported Linux version. Those are as follows:
- Red Hat Enterprise Linux 7 or higher
- CentOS 7 or higher
- Ubuntu 16.04 LTS or higher LTS
- Debian 9 or higher
- SUSE Linux Enterprise Server 12 or higher
- Oracle Enterprise Linux 7
For this post, I am using Ubuntu Server 18.04 LTS. All terminal inputs refer to it (and Debian).
What we also need:
- about 650 MB of disk space
- Kernel version 2.6.38 or above including the fanotify kernel option
Fanotify is a module of the Linux kernel that allows access and monitoring of files and directories, which is necessary for an AV/EDR solution like Defender ATP.
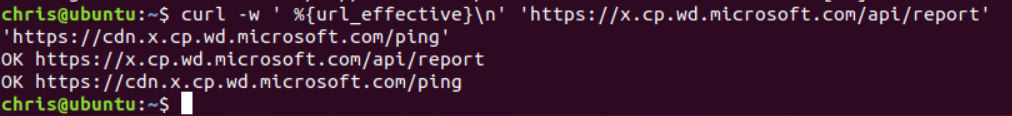
We also need network connectivity to the MDATP cloud endpoint. You can check that in a browser by accessing these URLs:
As a Windows guy, I will mainly focus on GUI configuration, but of course you can always use the Linux Terminal instead:
curl -w ' %{url_effective}\n' 'https://x.cp.wd.microsoft.com/api/report' 'https://cdn.x.cp.wd.microsoft.com/ping'Either way should return ‘OK’.
Get the MDATP onboarding package
Now we need to get the onboarding from the Defender ATP portal:
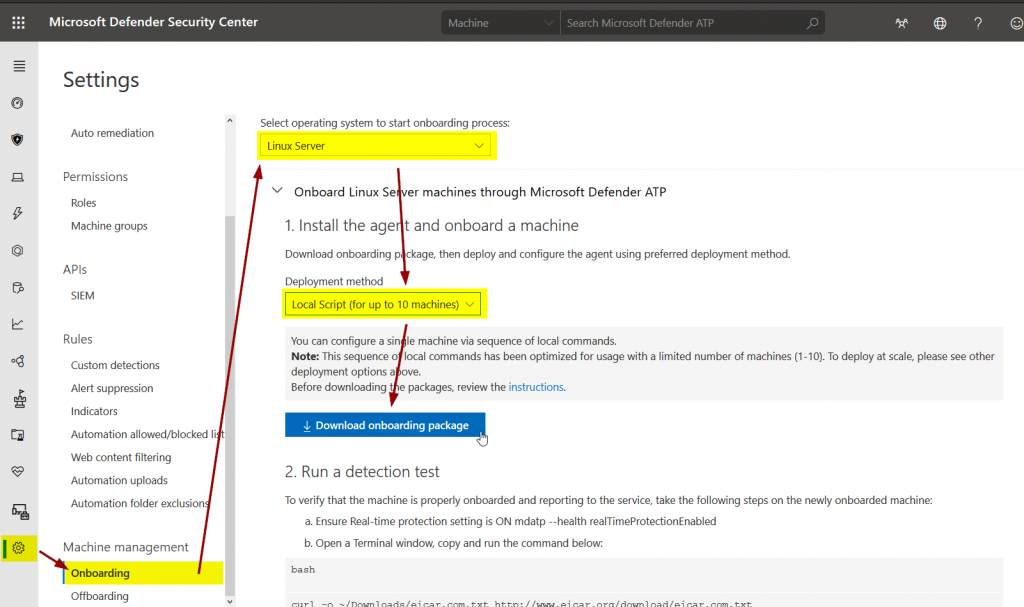
This is a zip file very similar to the one for Windows 10, however, it contains a python script that must be executed:
python WindowsDefenderATPOnboarding.pyIn my case, I used sudo and entered the direct path of the .py file:
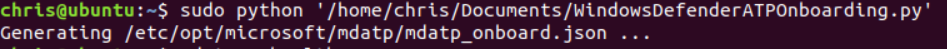
This will place all relevant information to /etc/opt/microsoft/mdatp:
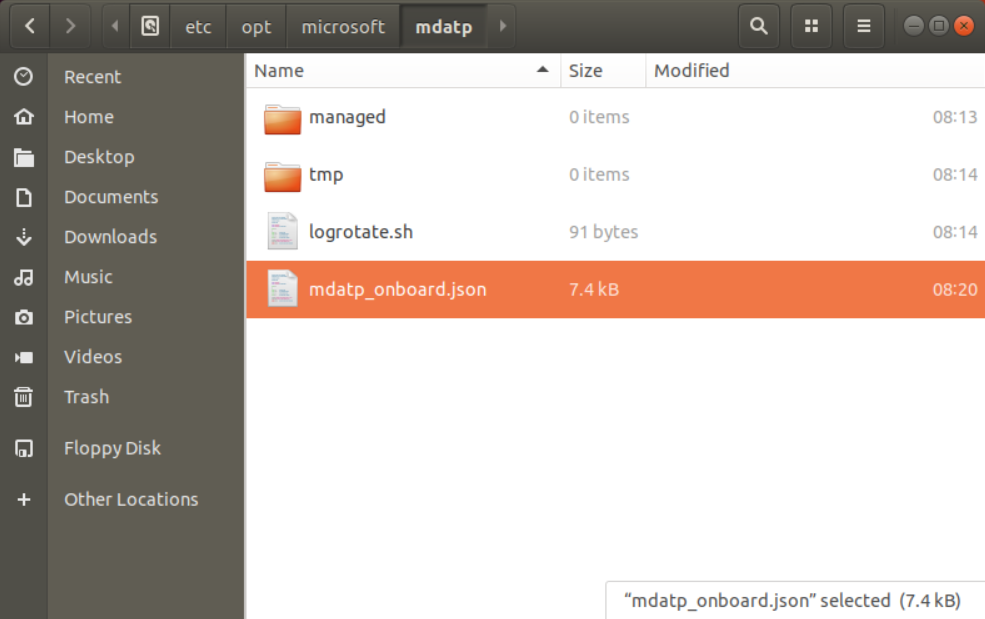
You don’t need to touch any of those files!
Installing MDATP
Now, we only need to install MDATP. There are a few steps we have to take in the Terminal:
Install curl:
sudo apt-get install curlGet the configuration from Mirosoft’s repository:
curl -o microsoft.list https://packages.microsoft.com/config/[distro]/[version]/[channel].listPlease mind the placeholders [distro],[version], and [channel]. You can use a browser to find out what you have to place there: https://packages.microsoft.com/config/
[distro] represents your distribution, e.g. “ubuntu”
[version] e.g. “18.04”
[channel] represents one of the .list files you see for your distribution
Using Ubuntu 18.04 and the insider-fast channel results in the following Terminal input:
curl -o microsoft.list https://packages.microsoft.com/config/ubuntu/18.04/insiders-fast.listInstall the repository information:
sudo mv ./microsoft.list /etc/apt/sources.list.d/microsoft-insiders-fast.listInstall the gpg package:
sudo apt-get install gpgInstall Microsoft’s GPG public key:
curl https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor > microsoft.gpgsudo mv microsoft.gpg /etc/apt/trusted.gpg.d/Install the https driver:
sudo apt-get install apt-transport-httpsUpdate repo metadata:
sudo apt-get updateAnd finally, install MDATP:
sudo apt-get install mdatpMDATP will grab the information we set earlier using the python onboarding script.
Working with MDATP locally
After a few minutes, the MDATP agent will turn to healty. You can check that via Terminal:
mdatp --health healthyThis will return ‘1’ once all is set.
You can also use
mdatp --healthto view more information, including the orgId which has to be in place for full functionality:
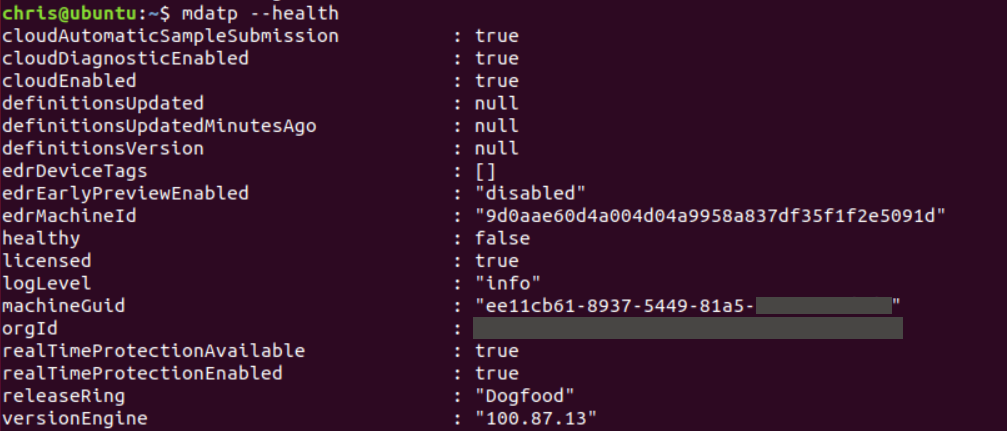
Now, we can do some tests, e.g. download an EICAR test file:
curl -o ~/Downloads/eicar.com.txt http://www.eicar.org/download/eicar.com.txtQuarantined files can be viewed using:
mdatp --threat --list --pretty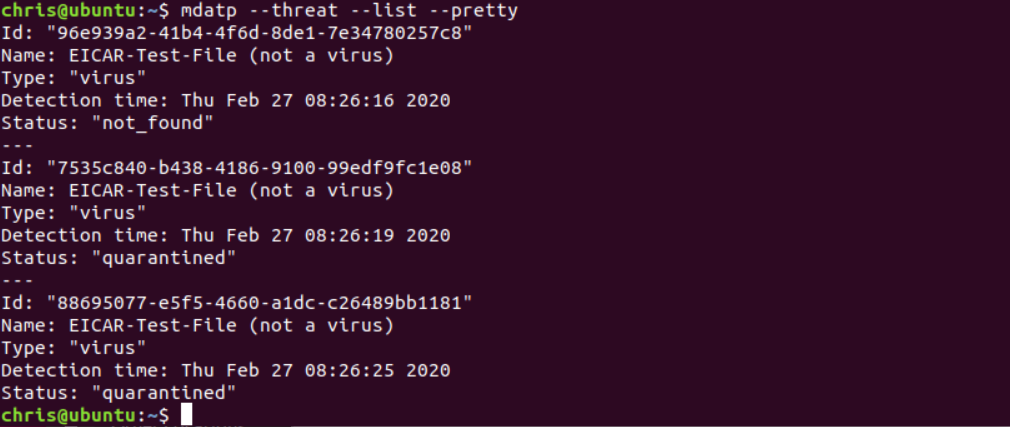
Working with the MDATP portal
After a view moments, the Linux machine and its alerts will appear in the MDATP portal:
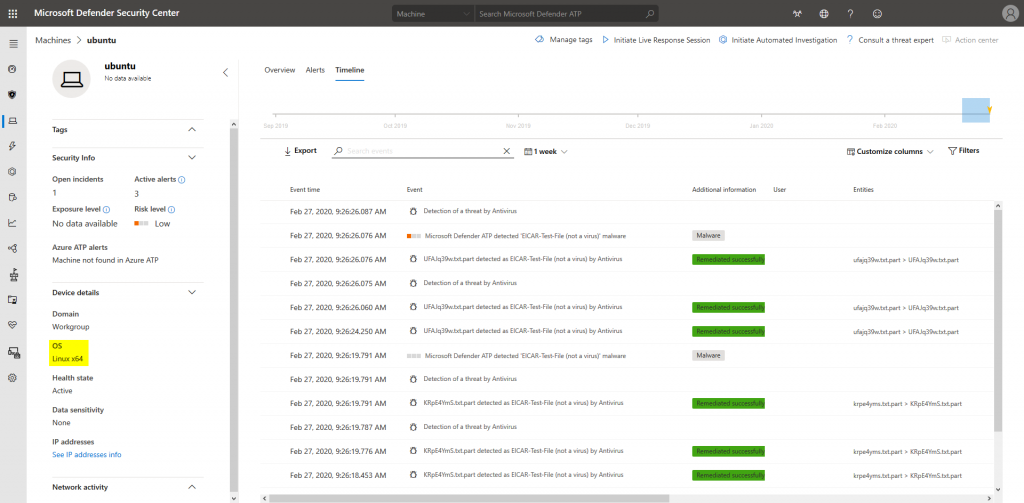
We also get the familiar alert experience:
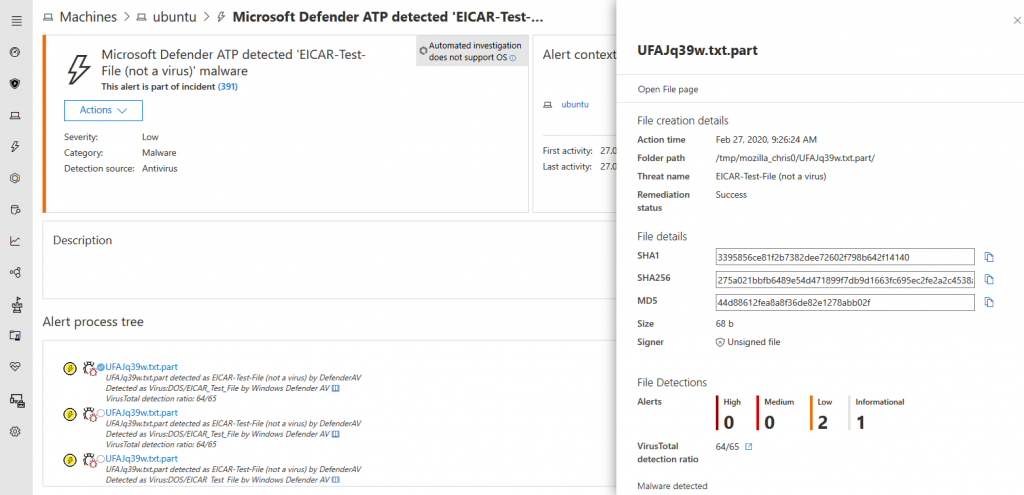
Other tasks
There are some other steps and tasks that might be interesting for you:
- Deploy via Puppet: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-install-with-puppet
- Deploy via Ansible: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-install-with-ansible
- Updating the client: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-updates
- Proxy configuration: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-static-proxy-configuration
- AV preferences: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/linux-preferences
Final thoughts
A unified enterprise EDR solution that covers all relevant platforms – sounds like a dream coming true. 😉 I really look forward to what’s to come with Defender ATP. Especially the upcoming version for iOS and Android will be very interesting. However, after macOS support, MDATP for Linux is already a great addition.
Thanks for reading!
Chris
