Microsoft Cloud App Security Conditional Access App Control – phew, what a name. A good reason to keep the technology behind it as simple as possible.
So, what does it do? Basically, Microsoft Cloud … ok ok I’ll keep it a bit shorter, MCASCAAC is a reverse proxy architecture that allows you to actively control the session of a user. While MCAS takes a small amount of time to react to certain actions or activities you can also take a real-time apporach by leveraging MCASCAAC for even more protection of your data. At the moment, MCASCAAC relies on SAML or Open ID Connect authentication to do its magic, therefor, the number of supported cloud apps is limited:
| AWS
Feld Concur CornerStone OnDemand DocuSign Dropbox Egnyte G Suite GitHub |
HighQ
JIRA/Confluence Salesforce ServiceNow Slack Tableau Workday Workiva Workplace by Facebook |
Exchange Online (Preview)
OneDrive for Business (Preview) Power BI (Preview) SharePoint Online (Preview) Azure DevOps (Preview) Yammer (Preview) |
Fortunately, Microsoft’s own apps are starting to become available for the service.
How to prepare for MCASCAAC
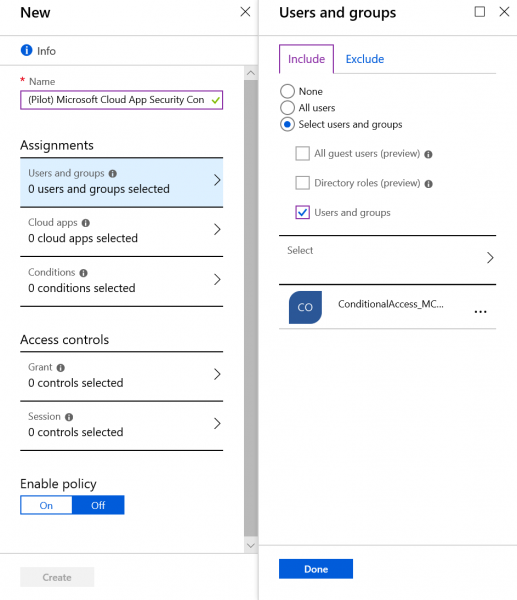
As the name already implies, Microsoft Cloud App Security Conditional Access App Control is sort of an extension for Azure AD’s Conditional Access. So that’s the place where you configure which users or groups are controlled by MCASCAAC. So first, you add a group of users you want to onboard to MCASCAAC:
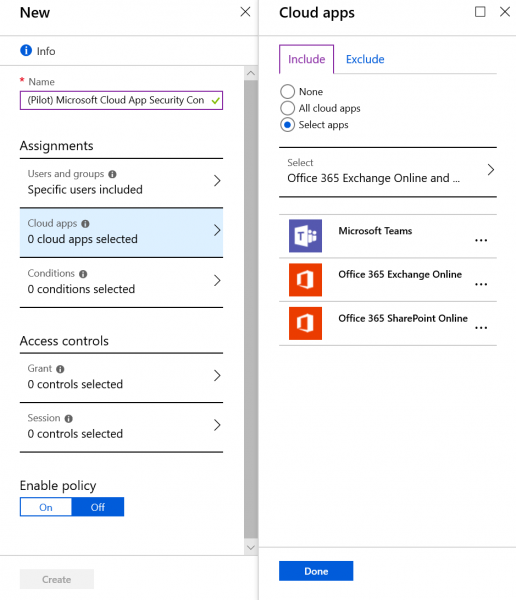
Second, select the cloud apps you want to have in scope of MCASCAAC:
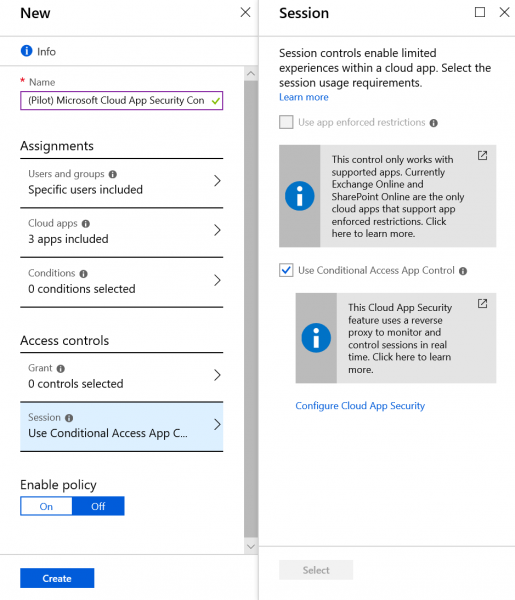
Finally, select “Use Conditional Access App Control” under “Sessions”
How to configure MCASCAAC
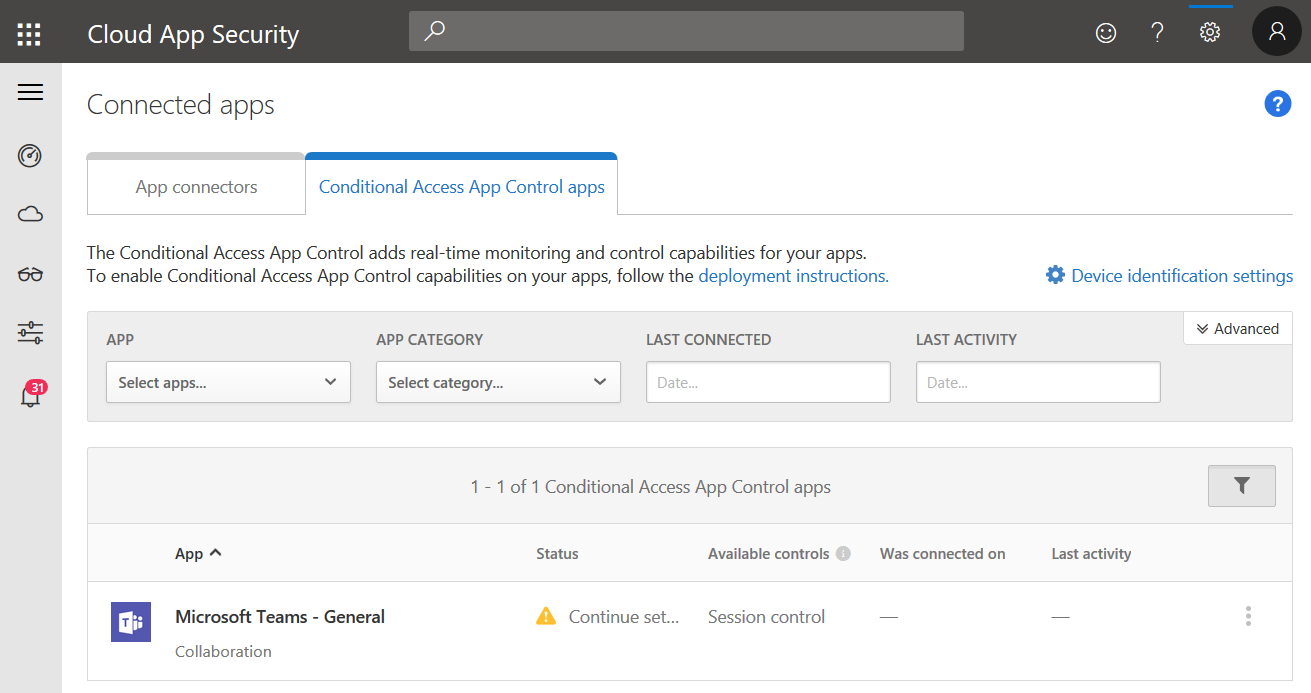
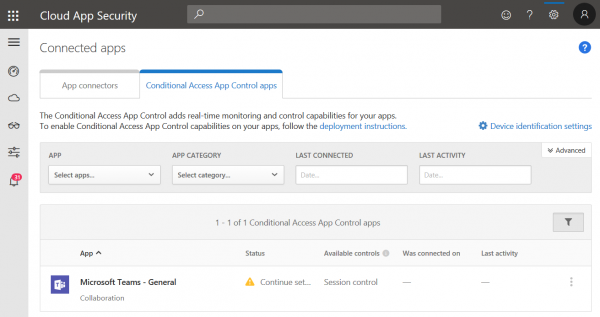
Now we can go back to the MCAS portal. Once a user with an assigned MCASCAAC policy signs in to one of the cloud apps we selected in the Conditional Access policy this app will appear under “Conditional Access App Control apps”:
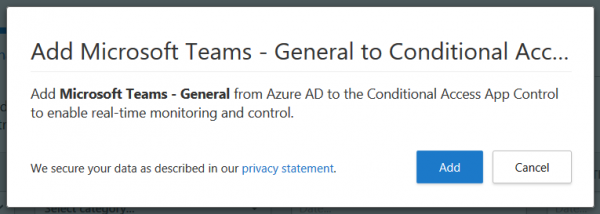
Click “Continue setup” to add the app to MCASCAAC:
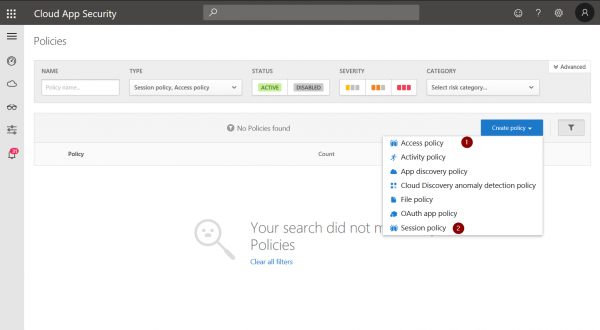
Now, you can define Access (1) and Session (2) policies for apps that are controlled by App Control:
Session policies
Session policies are quite similar to regular MCAS polices.
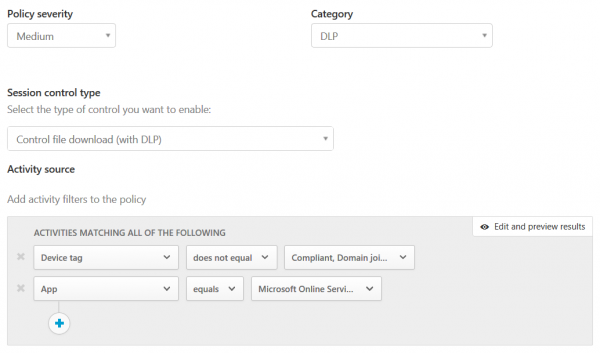
You can define severity, category, and control type.
You can also define custom activity…
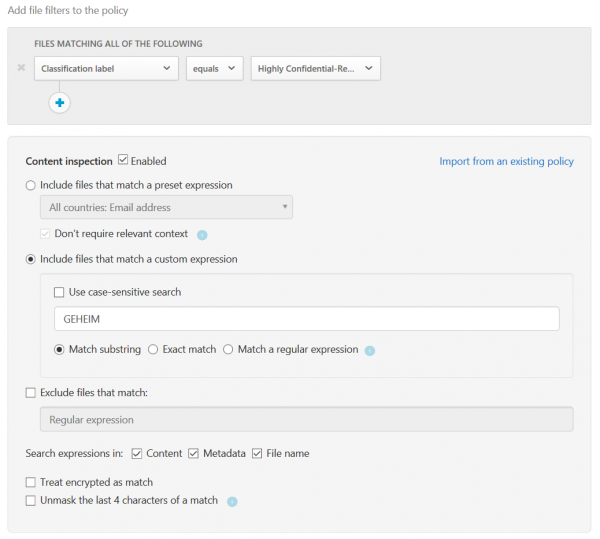
… and file filters for each policy.
Session policies are also capable of “content inspection” which offers DLP capabilities for each policy.
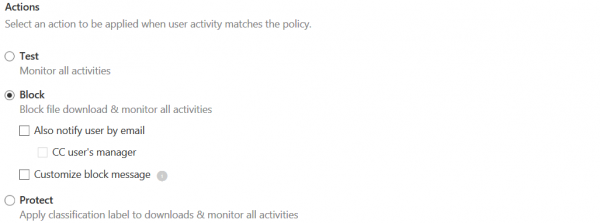
Finally, you can decide on what to do with a session if it meets your filter criteria:
Access policies
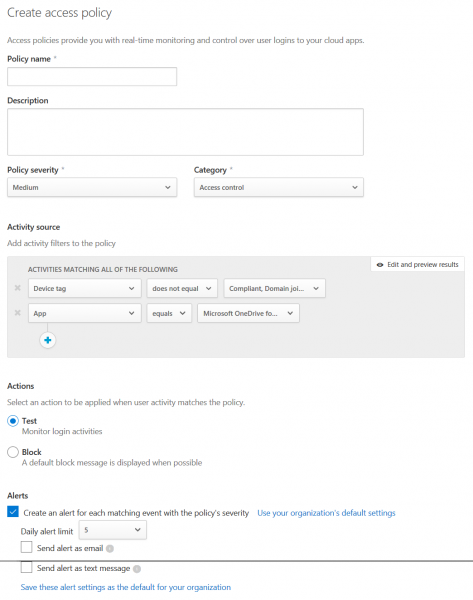
Access polices are quite similar. However, they offer less configurable options compared to session policies:
User experience
Once a user signs in to an app that is in scope of MCASCAAC a hint will be shown that notifies the user about enhanced session control:
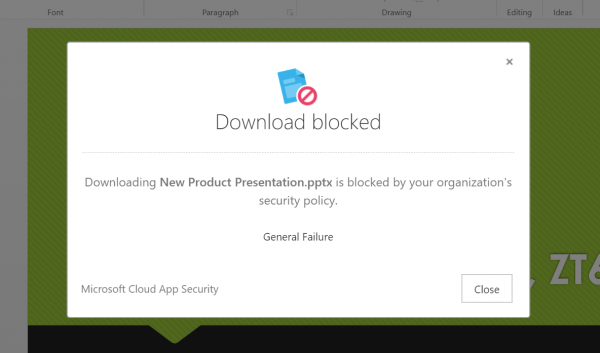
App Control will also always notifiy the user if they are limited by a policy:
They will also notice that URLs are now rewritten, as they are redirected to the MCASCAAC service.
There you have it. A quick introduction to Microsoft Cloud App Security Conditional Access App Control. Of course you can dig much deeper into it but I leave that up to you.
Cheers and thanks for reading!
Chris