In this post I will give you a quick overview about cloud configuration of AppLocker using Intune and MDATP.
AppLocker has been with us for quite some time now reaching back all the way to good old Windows 7. Although it is not the best solution from a technical point of view (there’s Windows Defender Application Control including TPM-enforced policy signing) it is still a good way to build a quick solution to stop users from installing software or executing unwanted applications. It is one of my recommendations for a secure Windows 10 baseline.
In this post I assume that you are already some kind of familiar with AppLocker. I will focus on how you can shift it to Intune for deployment and Microsoft Defender ATP’s Advanced Hunting capabilities for monitoring and policy refinement.
Configuration in Intune
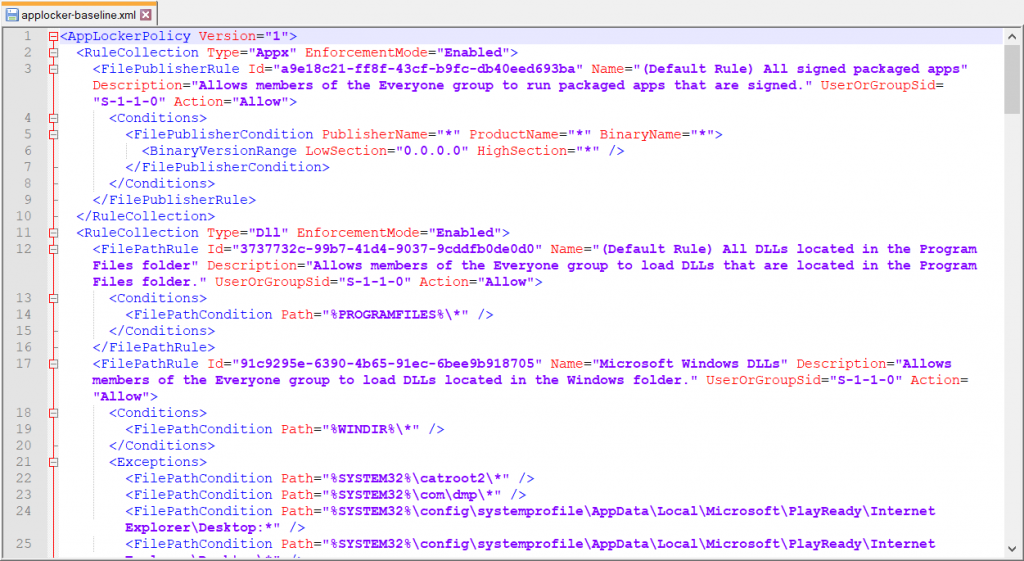
First export your AppLocker configuration from either the Group Policy Management Console in Active Directory or from your local GPEdit Console. Even in a cloud-only scenario with Azure AD joined clients you can still use the latter to build the policy. It will look something like this:
Now we need to jump over to the Intune console to create a new Windows 10 configuration profile using the “Custom” profile type:
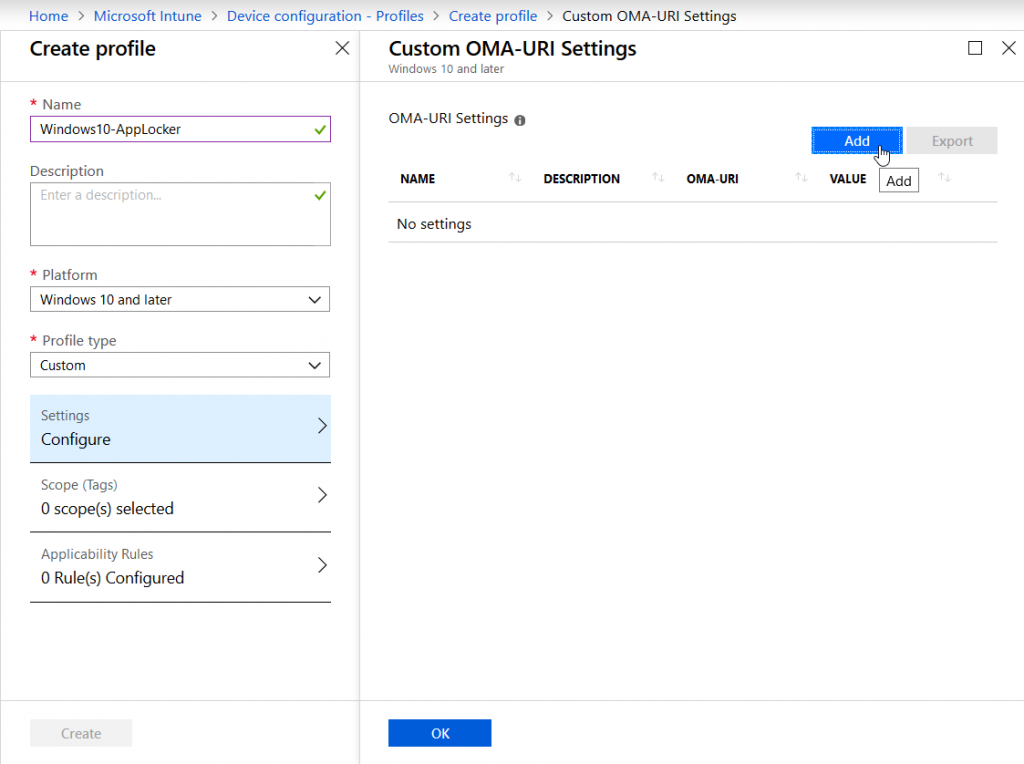
For each of the five different rule collections a distinct entry must be added. These are the OMA-URIs you have to use:
- AppLocker EXE:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/EXE/Policy - AppLocker MSI:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/MSI/Policy - AppLocker Script:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/Script/Policy - AppLocker Appx:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/StoreApps/Policy - AppLocker DLL:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/DLL/Policy
Find out more in the official AppLocker CSP documentation:
https://docs.microsoft.com/en-us/windows/client-management/mdm/applocker-csp
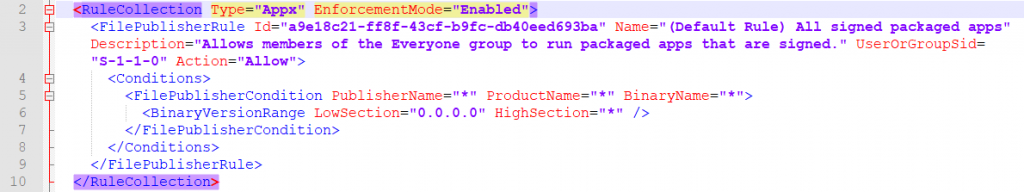
Data type has to be set to “String”, Value equals each <RuleCollection> section from the AppLocker xml. Here’s an example for the EXE rule collection:
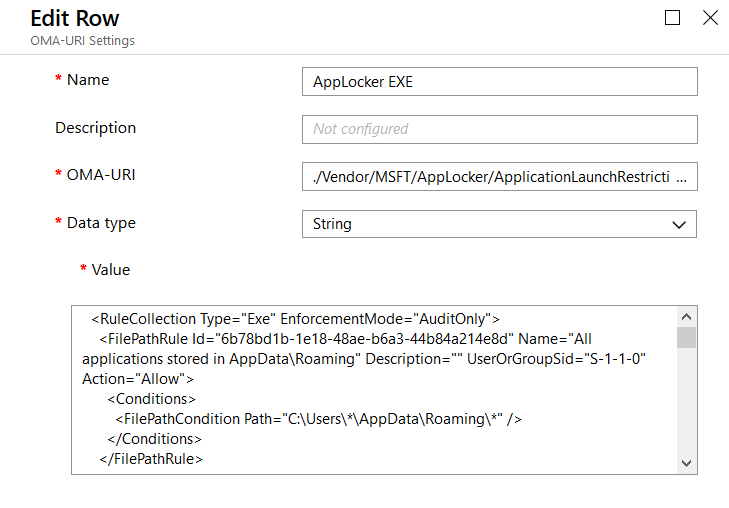
The Value text field must contain each rule collection xml section including <RullCollection …> and </RuleCollection> as marked here in Notepad++:
Once you have added all rule collection types it will look something like this:
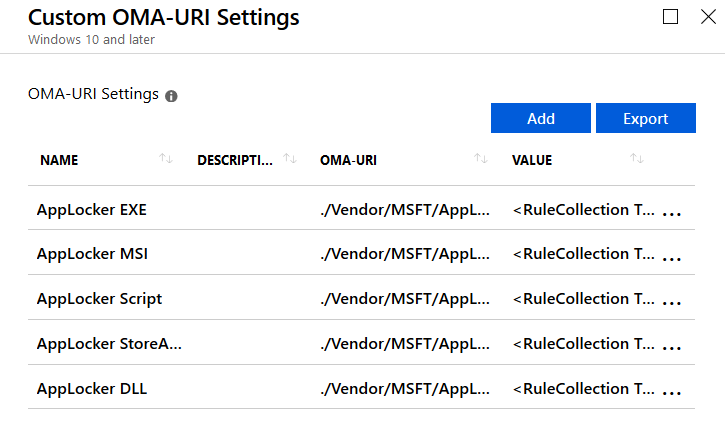
Don’t forget to assign the profile to all users and/or devices you want to target. Although it might seem obvious please remember that deploying any kind of application control in enforced mode could break things without testing it first. So you might want to use AppLocker in audit mode first.
Monitor AppLocker events in MDATP
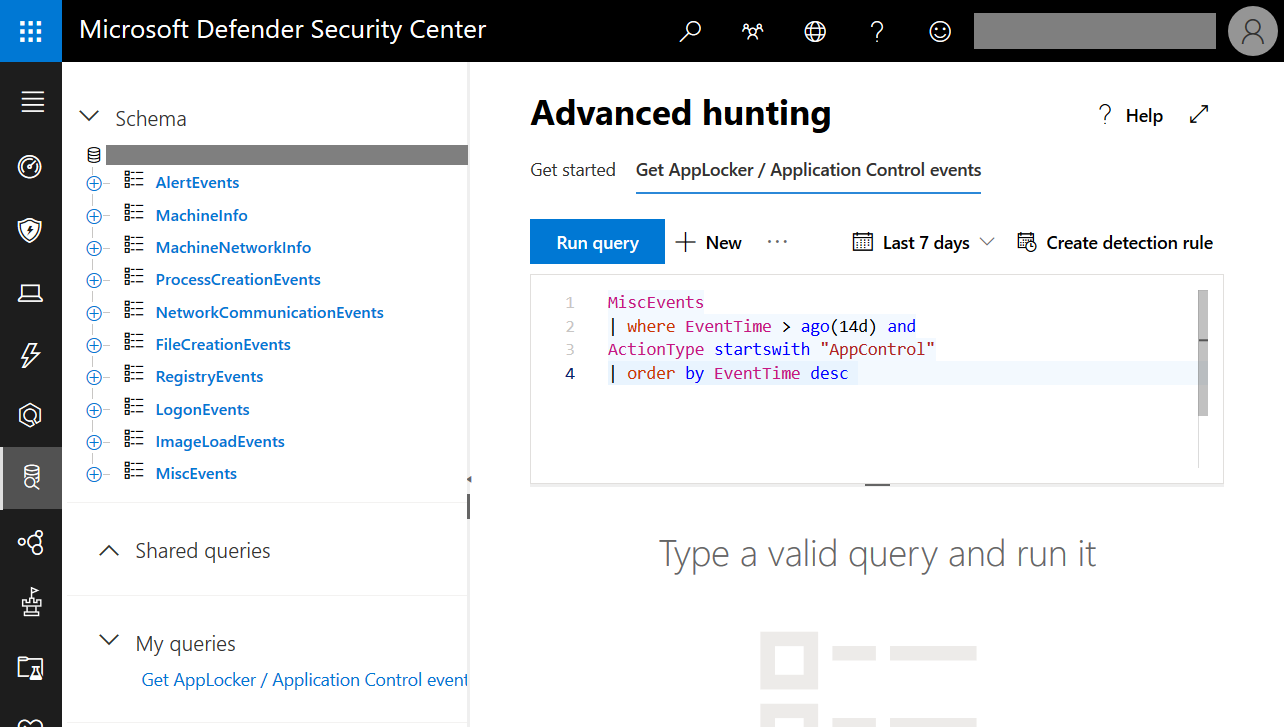
Now we head over to the Microsoft Defender Security Center selecting the Advanced hunting sub-menu. There we add the following query:
MiscEvents
| where EventTime > ago(14d) and
ActionType startswith "AppControl"
| order by EventTime desc
Just paste it to the query text field:
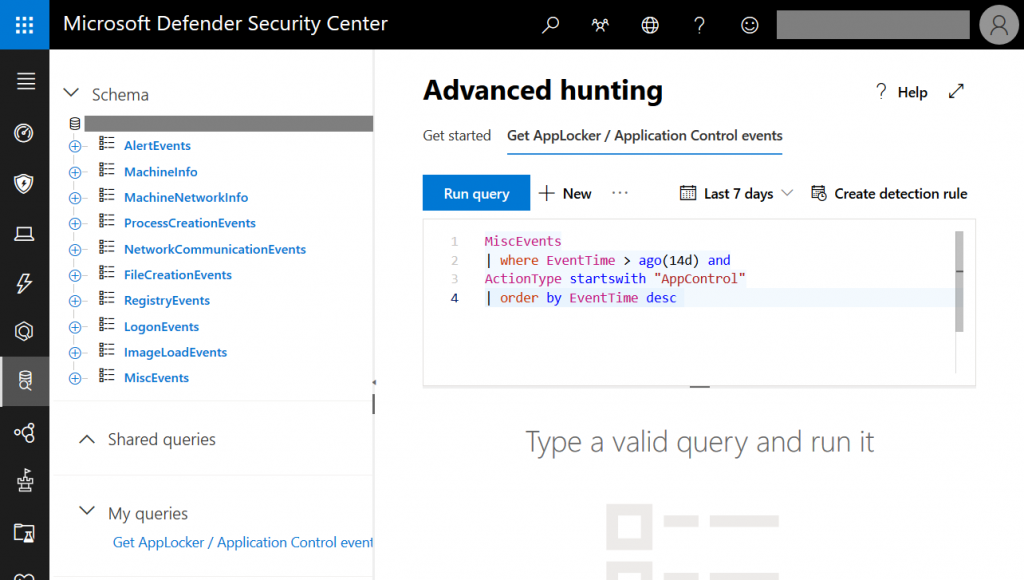
You can modify the query at any time, e.g. by changing the EventTime filter to cover more days in the past. Once you run the query you get all files that are recognized by AppLocker (or Defender Application Control):
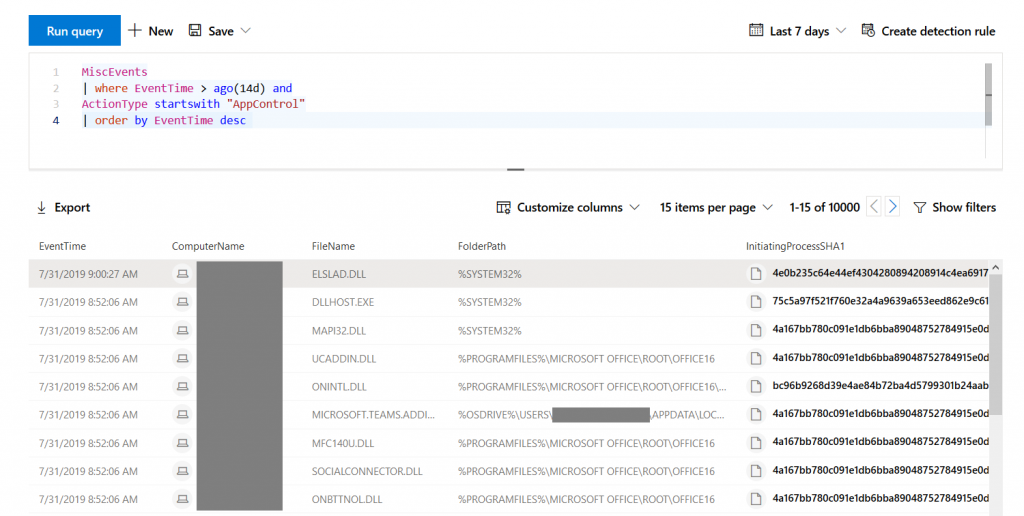
Depending on how you use AppLocker you can extract information about either paths, file names, signature, or file hashes to enhance your policy which you would then edit in either GPMC or GPEdit. Then you can continue by exporting it as xml and pasting each rule collection into the Intune profile again.
Thanks for reading!
Chris