Security in the Microsoft world has never been an on/off switch. Looking back at Windows and especially Active Directory there have always been multiple steps that had to be considered. With the cloud and Azure AD, some companies used the possibility not to start with the same mistakes that were made in the past.
Unfortunately, numbers show that even in 2019 only around 8% of administrative accounts in Azure AD use multi-factor authentication. For a consultant like me it might seem to be the best business oppurtunity to work with customers that still have their way to go. But I can tell you that’s not the case. Every successful cyber attack poses a threat to businesses which also puts jobs and people at risk. So I am very happy that Microsoft works on providing out-of-the-box settings to increase security. They started with Conditional Access baseline policies a few months back and have now introduced a new concept: Azure Active Directory security defaults. Let’s have a look!
How to enable it
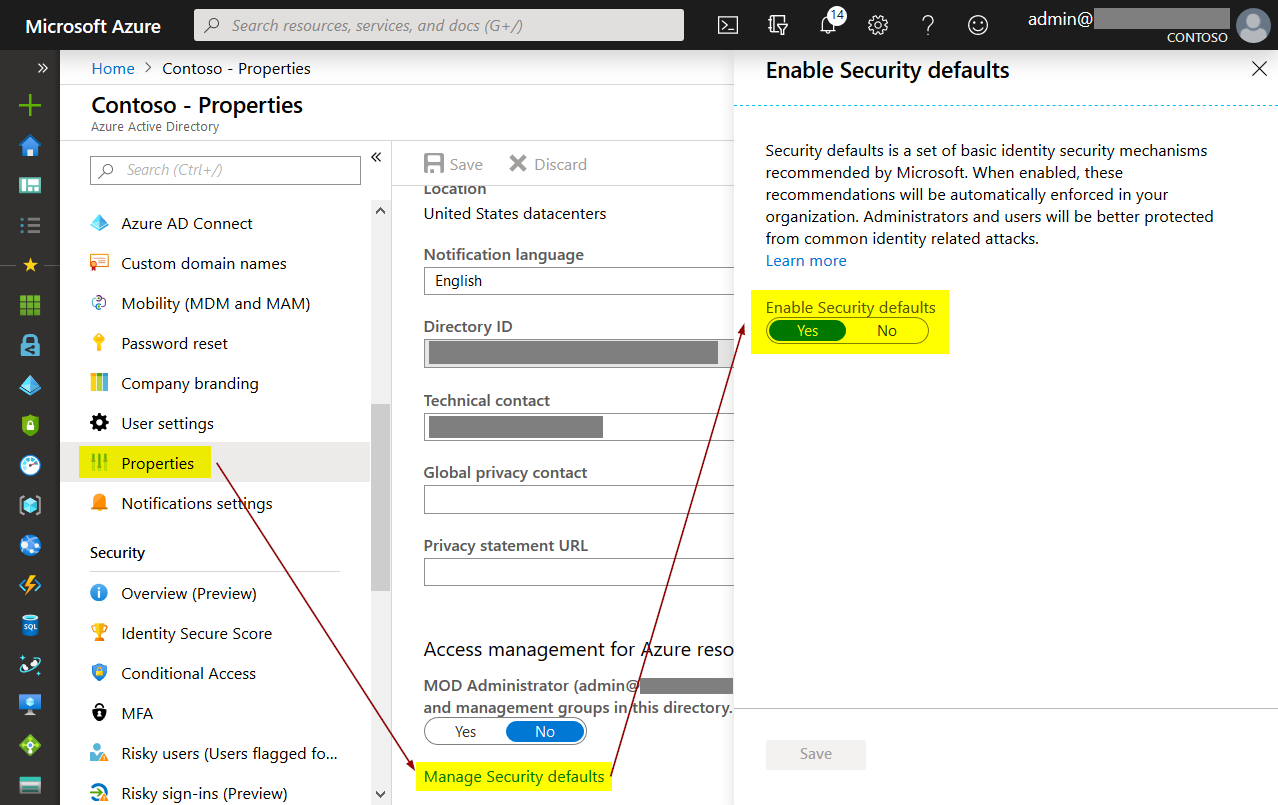
Enabling Azure AD Security Defaults is quite simple. The setting is hidden under the “Properties” section in the Azure AD portal:

Note
If you already use custom Conditional Access policies, security defaults cannot be enabled!
What “Security Defaults” does
At the moment, this is what security defaults enable:
MFA registration
All users of the tenant will be prompted to register for multi-factor authentication. Each account has a unique 14 days perios to complete registration. After that, it will be enforced at the next sign in (in a browser to one of the companies Azure AD linked cloud resources, e.g. Office Online).
MFA enforcement for administrators
These administrative roles will be enforced to use MFA every time they sign in:
- Global administrators
- SharePoint administrators
- Exchange administrators
- Conditional Access administrators
- Security administrators
- Helpdesk administrators / Password administrators
- Billing administrators
- User administrators
- Authentication administrators
Note
There are other administrative roles that you might want to secure. If you enable security defaults you can’t add additional Conditional Access policies. So using the old Azure portal to enforce MFA for other accounts could be necessary.
Note
It is best practice to have at least one emergency access account that is not forced to use multi-factor authentication. With Security Defaults, exclusions can’t be made to satisfy this recommendation! Another point that shows they are intended for smaller companies.
“On-demand MFA” for users
With Security Defaults, standard users will also be prompted for strong authentication. However, in this case it’s not enforced for all sign-ins but to protect the account “whenever necessary”. What this means can be taken from the Conditional Access baseline documentation that I already mentioned in the beginning: Microsoft takes the risk level of the user and their sign-in to enforce MFA if anything seems suscpicious.
Blocking legacy authentication
Microsoft cloud security features like Conditional Access and MFA rely on modern authentication to be used. That’s why Security Defaults will also block these legacy authentication methods:
- Mail protocols like IMAP, SMTP, and POP(3)
- Older Office clients with no modern auth capabilities (like Office 2010)
Note
As it is still commonly used, Exchange ActiveSync is not in scope of this policy. However, your long-term goal should be modern authentication only.
Protecting privileged Azure API actions
Security Defaults will also protect access using the Azure Resoure Manager API, including:
- Azure portal
- Azure PowerShell
- Azure CLI
In this case, it doesn’t matter if a user has an administrative role. As standard users without any roles can also be delegated to Azure resources, every account using one of the listed methods is in scope.
MFA registration is enforced immediately without the 14 days period. Sign-ins must be protected by MFA.
Verdict and considerations
I really appreciate Microsoft bringing more secure defaults to tenants. The most common problem in production will be the conflict with excisting Conditional Access policies which block the activation of Security Defaults. That’s by design! For enterprise customers, custom Conditional Access policies should be in place. All settings in the defaults can be implemented manually.
For SMBs, however, Security Defaults are a good solution to be secure right from the start while still having the option to switch to custom configuration in the future.
Please also keep in mind that all settings will have implications. Users must be familiar with using MFA. You should also take some time to evaluate if anything might break. This especially applies to legacy authentication.
Here you can find the official documentation: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-security-defaults
Thanks for reading!
Chris