I already posted a few things about FIDO2 and other passwordless authentication scenarios for Azure AD (introduction / additional info). Now (or to be more precise: in Q1/2020), the real funky stuff begins! As Microsoft announced at Ignite 2019, they will be extending FIDO2 support to hybrid Azure AD joined devices which will also grant those machines SSO to on-prem resources.
This is a great enhancement to the FIDO2 offerings. Many customers have asked for this and I really appreciate the implementation. In this post, I’d like to show you how this will be working.
Deployment components
What do we need from a technical point of view to make this work? It’s pretty straight forward. If you have hybrid Azure AD joined Windows 10 machines all components are already there:
- Azure AD Connect
- Windows 10
- Domain Controllers running Windows Server 2016 or 2019
I assume that a adequate number of 2016+ DCs must be present just like it is necessary for hybrid Windows Hello for Business in the key trust deployment modell. However, I am curious if this will really be released with a patch. A the moment, the functionality is already there since last July with Windows Server vNext Build 18945.
Which versions of AAD Connect and Windows 10 you need has yet to be announced – however, Windows 10 20H1 will most likely be the version of choice.
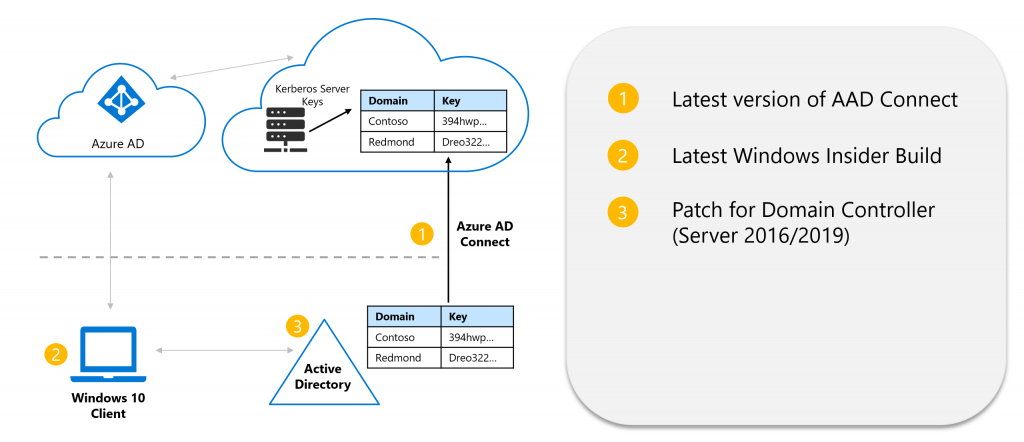
AAD Connect will then go ahead and sync an individual Kerberos Server key for each on-premises AD domain. This will be used to identify the users home domain.
Authentication flow
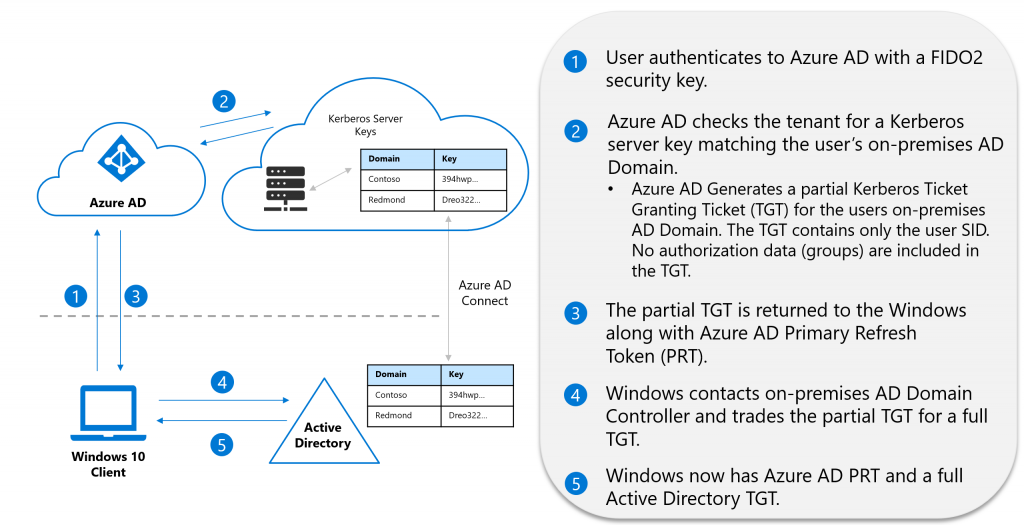
The flow during authentication is also pretty straight forward:
- First, Azure AD is contacted just like on an Azure AD joined device.
- Azure AD checks for a Kerberos Server key that machtes the user’s on-prem domain. It generates a partial TGT for this domain containing only the user SID, no authorization data (like groups).
- Partial TGT and Azure AD Primary Refresh Token (PRT) are handed over to the device
- The device contacts an on-prem Domain Controller and gets a full TGT for the user
- The user now has PRT and full TGT
The user will then have a SSO experience for Azure AD applications but now also for on-prem resources using Kerberos.
User onboarding
Users will be able to register FIDO2 key, just like they do with with the current implementation for Azure AD authentication. I explained how to do that in my first post about passwordless authentication.
Coming next
Passwordless authentication remains one of my favorite security topics. That’s why I will of course follow up on that concept. These posts are planned for the future:
- Part 4: technical implementation for hybrid devices
- Part 5: as Apple is now a board member of the FIDO Alliance, I will take look at leveraging iOS (but also Android) for FIDO2 authentication.
And fyi – there already was a docs article about enabling authentication for on-premises resources: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key-on-premises
Microsoft removed that one, so it is now redirecting to a different article. But you might just keep an eye on that URL. 😉
Thanks for reading!
Chris
