Azure AD always had a big advanced over on-premises Active Directory: a very granular RBAC approach when it come to administration. However, there is also a downside – roles can only be applied globally without a limited scope. This has changed now. Being in a PowerShell based preview for quite some time, Azure AD Administrative Units (AUs) can now be easily defined via the Azure Portal.
This enables administrators to cluster users and groups, and delegate administrative access to entities inside a particular AU only.
Configure Administrative Units via GUI
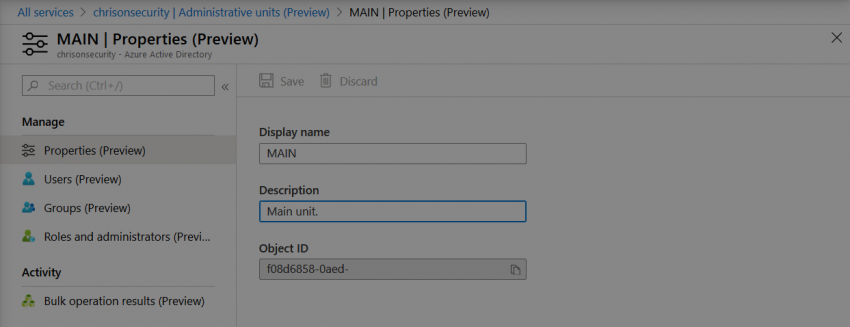
Administrative Units can now be found in Azure Active Directory:
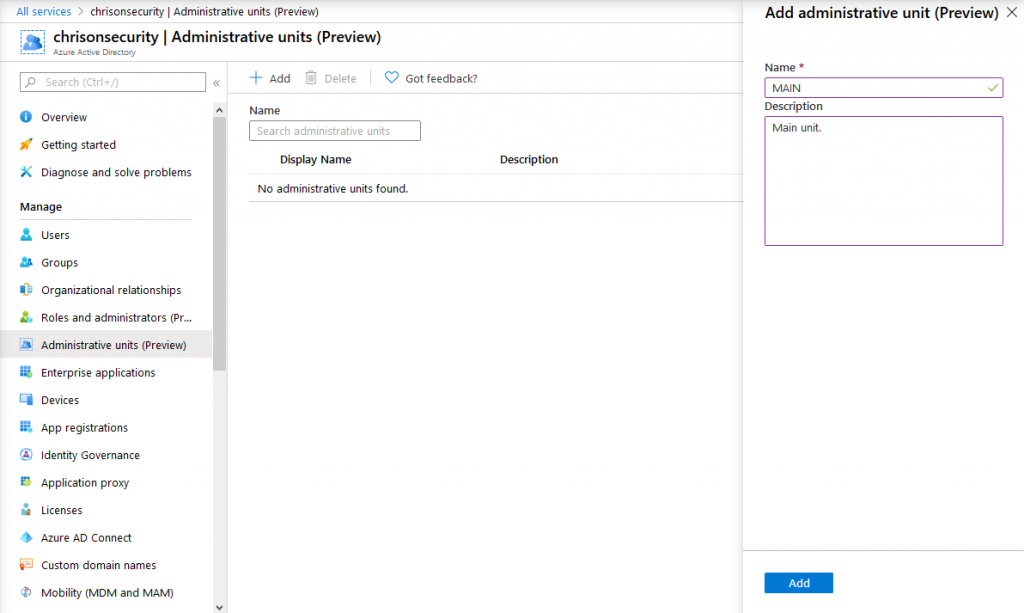
Creating them is quite easy by setting a name and description. After that, they appear right away in the AU list:

Each AU consists of users, groups, and the corresponding roles and administrators:
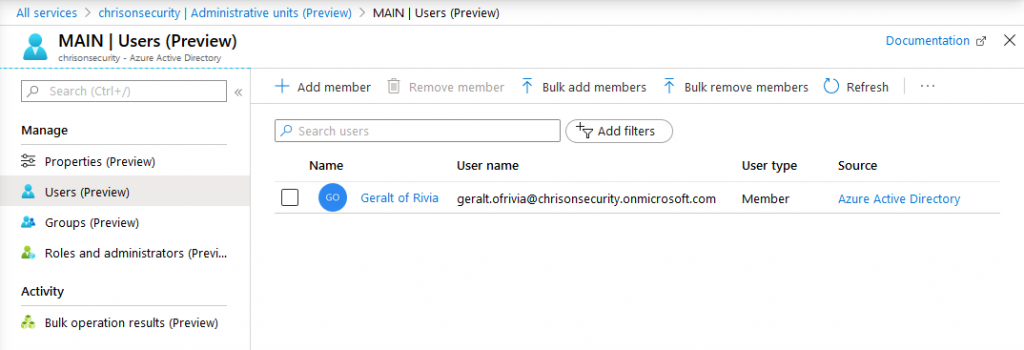
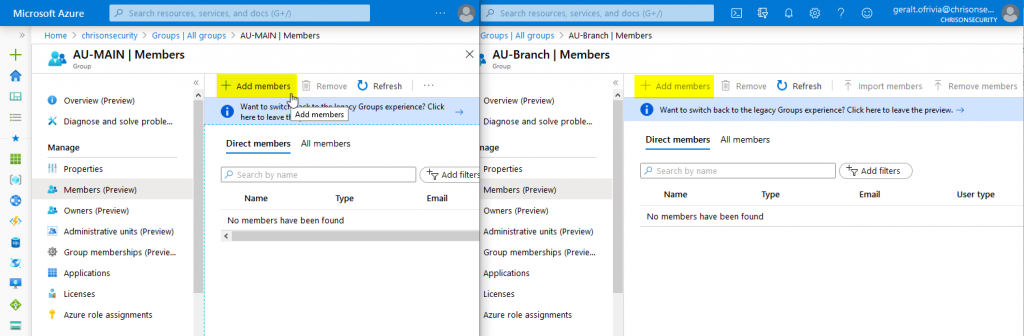
You can then go ahead and add users and groups to the AU:
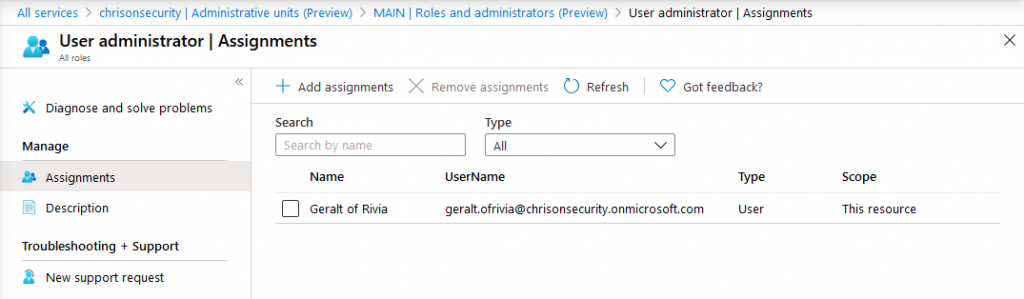
Each AU also has its own set of administrators. Those are:
- Authentication administrators
- Groups administrators
- Helpdesk administrators
- License administrators
- Password administrators
- User administrator
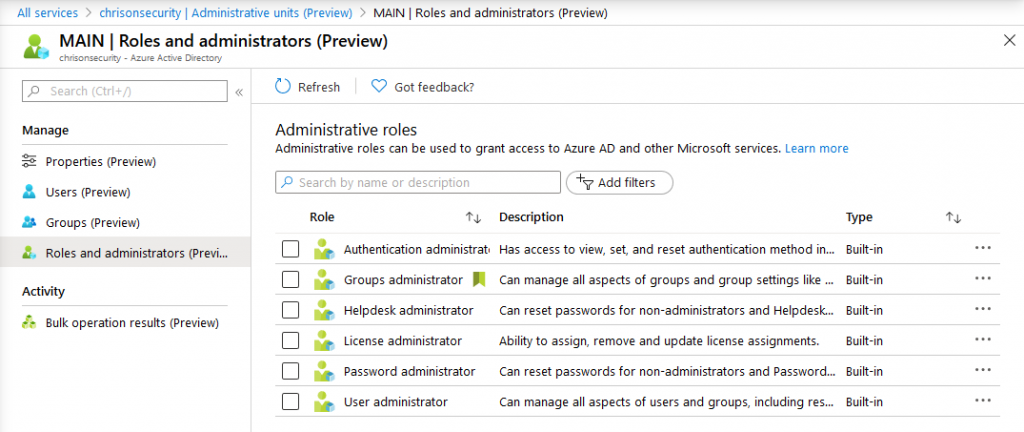
Each role is independent from the global ones in Azure AD. So you can easily delegate administrative access to users that should only administer a certain AU.
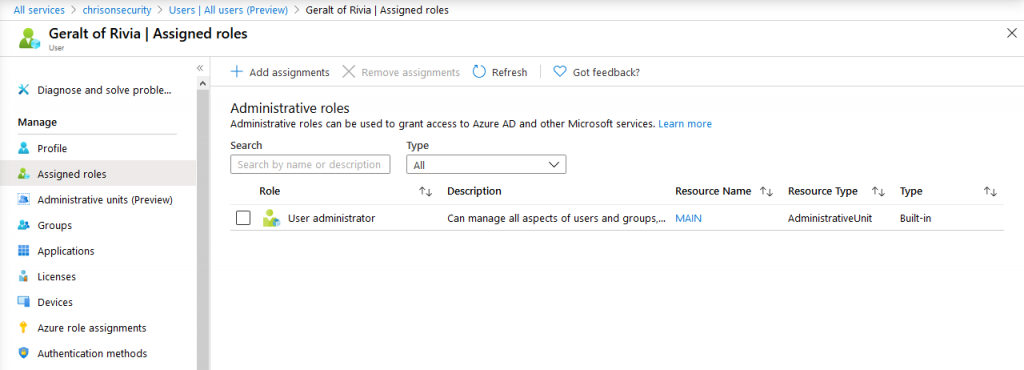
The role also appears on the user’s Azure AD profile and it luckily also indicates in which AU the role was assigned:
Now, my test user Geralt can edit resources from the MAIN AU, but not other groups and user:
Summing things up
The Azure AD RBAC model has been not flexible enough to delegate administrative access to only certain entities. Administrative Units are now a great solution for that problem.
You might have noticed that AUs only contain users and groups at the moment. Of course, there are other elements that should be considered – mainly regarding device management in Intune. Luckily, Intune already has support for customized RBAC roles:
So, Administrative Units and Intune roles can be used in combination to delegate most tasks for local branch offices.
Thanks for reading!
Chris