Staying on the pre-breach side of things is the main goal in IT security. How can you achieve this state on Windows clients? A large amount of malicious software relies on unpatched vulnerabilities or misconfiguration that can be abused. A few months back, Microsoft added Threat & Vulnerability Management to Microsoft Defender Advanced Threat Protection (MDATP) to tackle those challenges.
Note
This post was originally released in September 2019 and was updated on May 8th, 2020.
You can find the official announcement here: https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/MDATP-Threat-amp-Vulnerability-Management-now-publicly-available/ba-p/460977
Its goal: show unpatched operating systems, applications, and recommendations for security configuration.
You can find the new category in the menu on the left-hand side in MDATP:
Overview
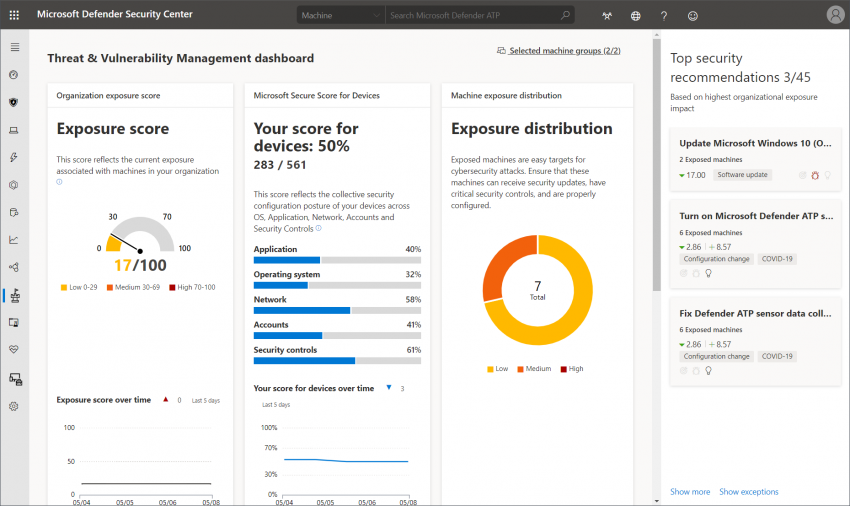
As always, a central dashboard gives an overview of different scores that represent client exposure and configuration. It also shows some security recommendations right away that are ranked based on their possible impact.
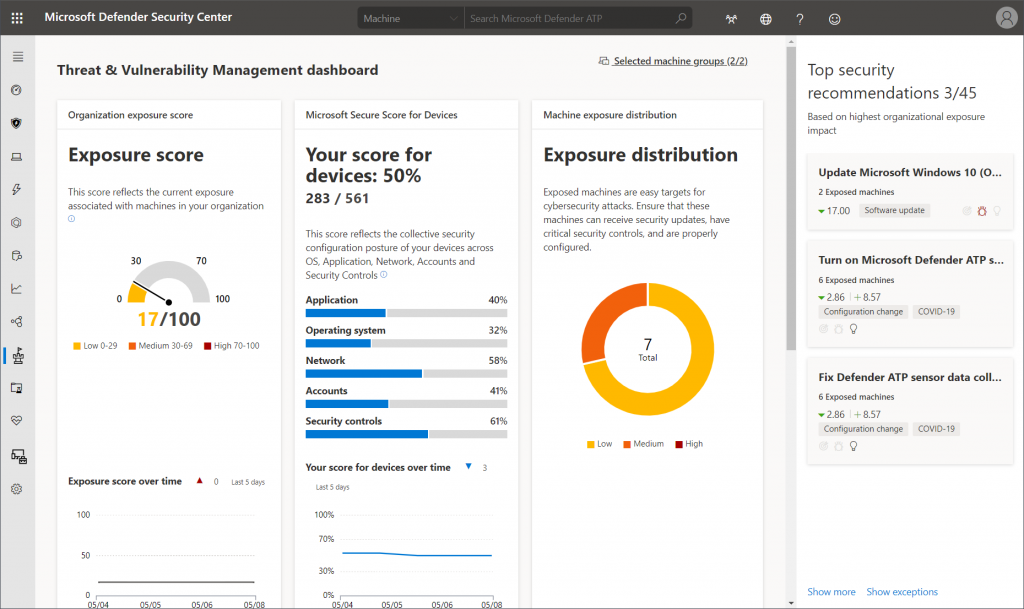
High scores continue with information about top vulnerable software and exposed machines:

Security recommendations
For all clients reporting to MDATP the security recommendations page collects all detected problems. As you can see there a quite different entries. Some ask for software updates (Windows, Office, browsers, other third-party tools), others give recommendations about security configuration you might want to disable to improve the overall resilience of the system.

For each recommendation, Microsoft also collects information on whether there are threats that are actively abusing vulnerabilities. If you want to dig deeper, you might also take the provided CVEs for further investigation.

For all components of TVM you can also take another approach and start from any client to get information specific to the particular system. The content is the same – just pre-filtered.
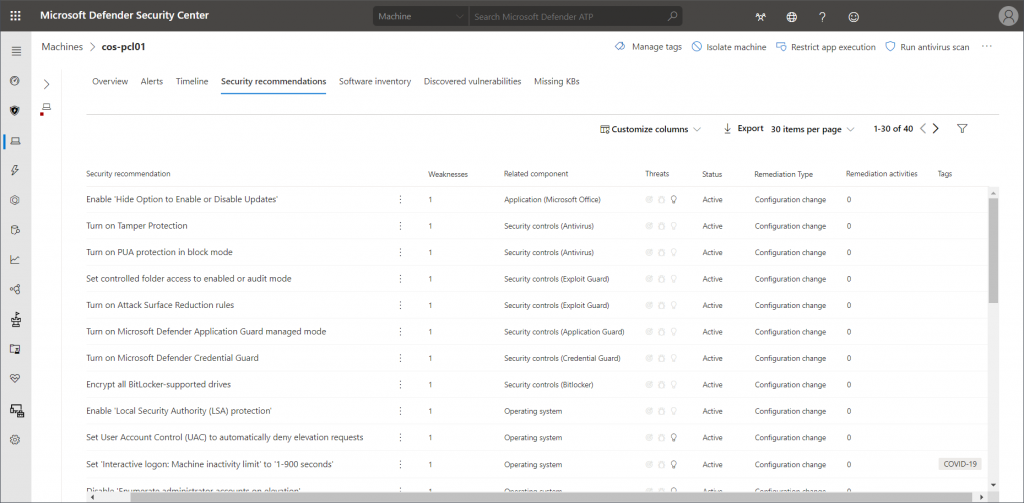
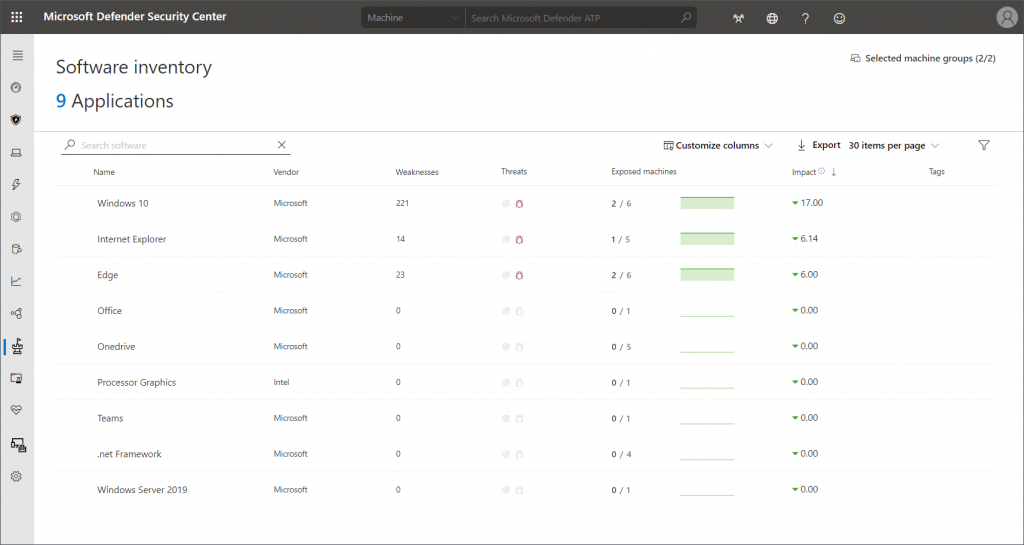
Software inventory
Knowing which software is in use in your organization can be a challenging task. To give security recommendations, TVM also has to be aware of any installed software. This information is also provided to the dashboard. Here you get a general view of detected applications. Weaknesses, threats, and exposed machines are linked here as well.
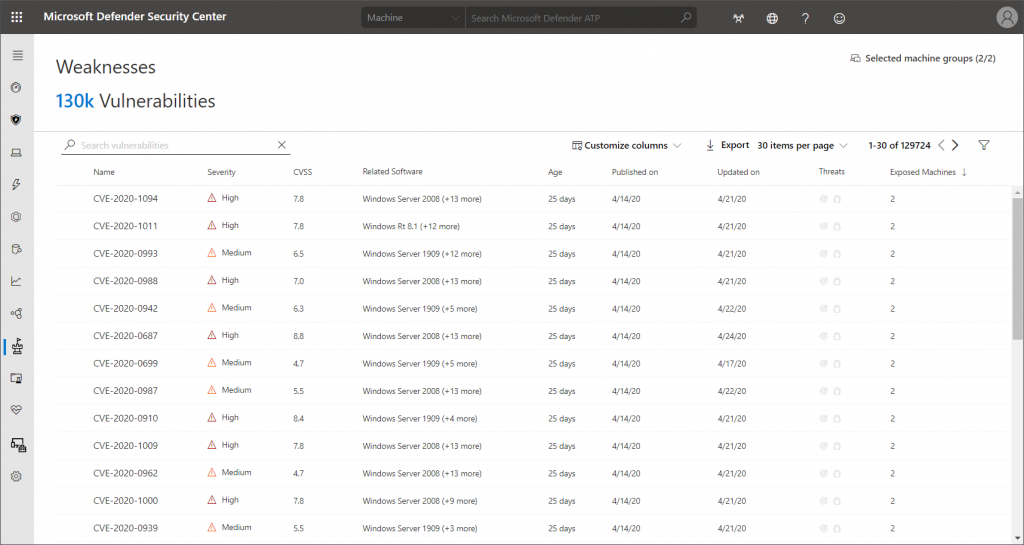
Weaknesses
If you want to start by evaluated know CVEs and their severity levels the weaknesses dashboard is your way to go. This just changes the approach; however, you also get linked information about affected software and exposed machines.
Remediation
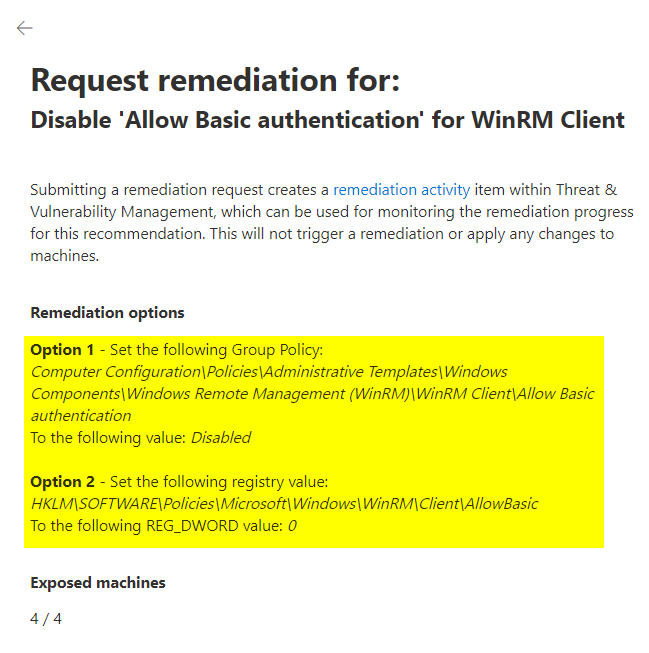
In a production environment it is very likely that a lot of unpatched systems and missing security configs are being found. So, you might ask: how can threats be mitigated? From an information point of view the answer is easy: in most cases, TVM gives you the exact steps you need to take, e.g. by listing the necessary Group Policy configuration.
Ironically, Intune configuration is missing for most remediation recommendations. To be honest, I can’t blame Microsoft. Intune heavily relies on GUI configuration, there’s just not enough space in a panel of this size. Here’s an example on how that looks:
Regarding update advisories, the main remediation is – you guessed it – switching to the most recent version of the product.
The bad news is, that there are no automated processes available at the moment. The good news being: you can let your Intune administrators know that they might want to have a look at a certain configuration or app by creating a remediation request in TVM:
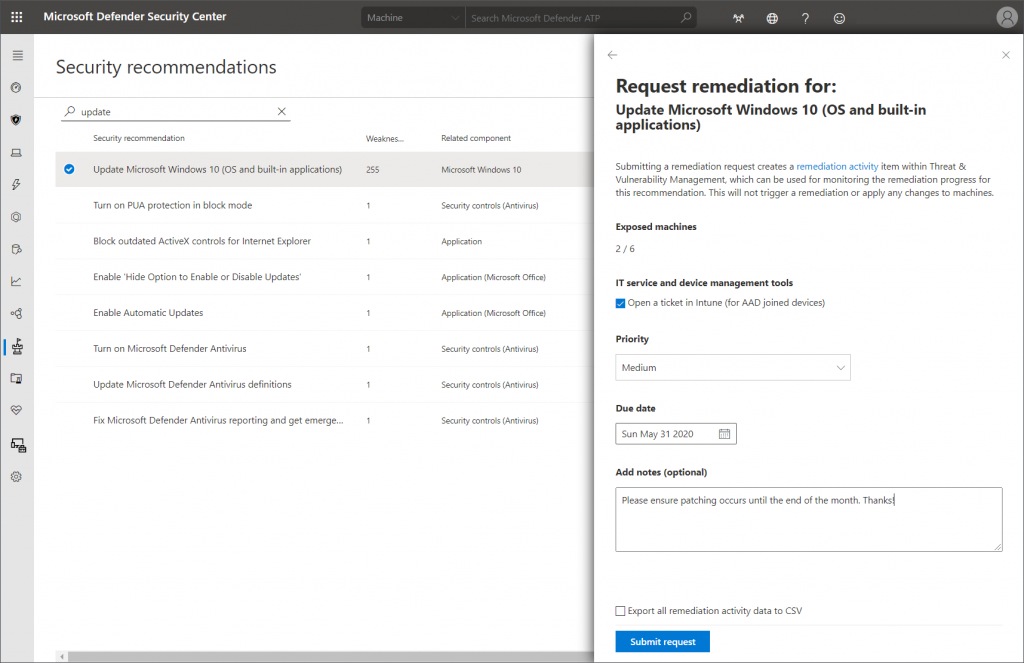
This request will pop up in the newly created “Endpoint Security – Security tasks” section in the Microsoft Endpoint Manager admin center:
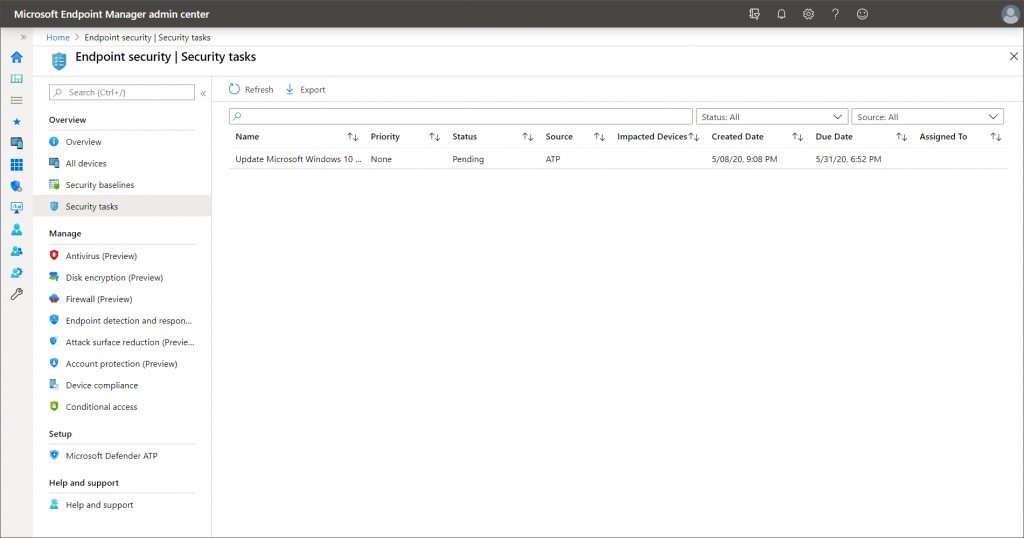
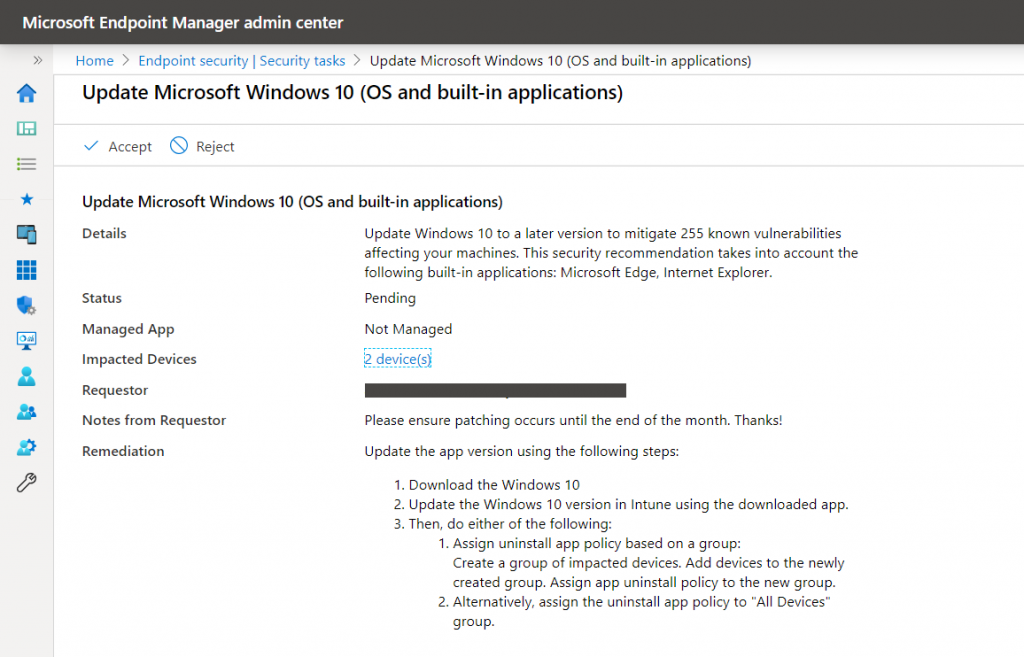
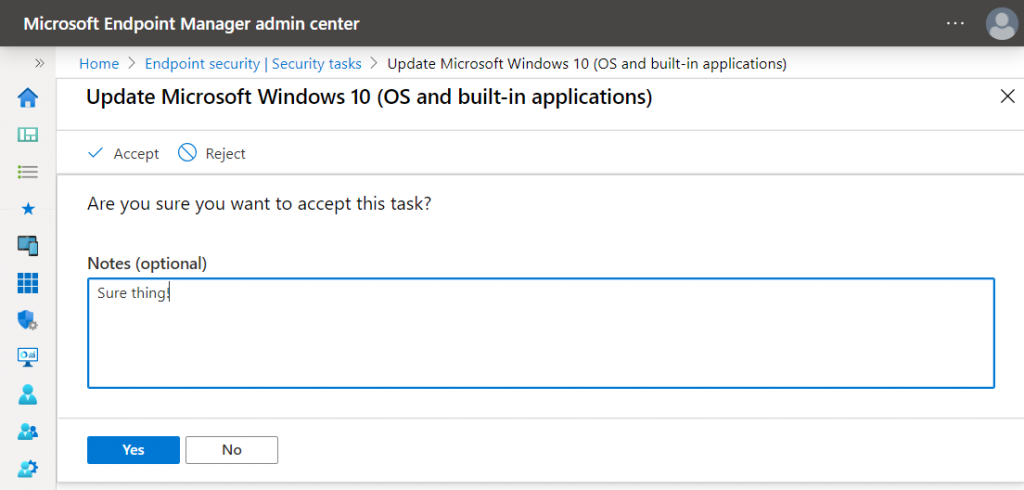
The Intune admin can then get a quick overview of all requests and have a look at the details the MDATP admin specified. Depending on the team spirit in your IT department, they can either “Accept” or “Reject” the task.
At the moment, there is no auto-remediation. However, depending on the individual security recommendation that was used for the request, the security task will also contain information on how to do it.
The status will then be synced back to TVM in MDATP:
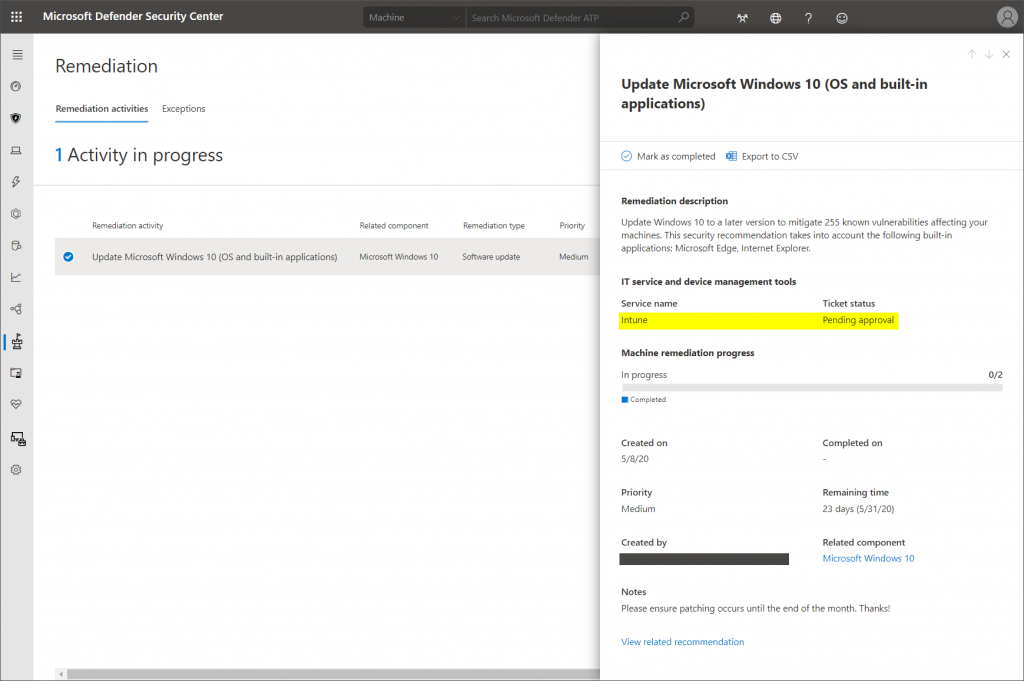
Notes from the field
Here are some thoughts about the daily use:
- The progress bar in the image above does automatically increase no matter why the remediation occurred. So, if e.g. Windows 10 clients just patched themselves, you get no indication that an Intune admin actually did something.
- Be patient after patch days. 😉 Even if you enforce Windows and Office updates very quickly, some users might take a while to restart their devices.
- Same applies to all auto-updating applications. It can take a while until e.g. Chrome or Firefox engage a forced restart for updates.
- Know your security posture! TVM can help to add previously overlooked security configurations to your clients. However, TVM does not know your intentions. So some of those recommendations can be ignored if you know why you decided to skip them.
- Make sure you know what you’re looking for to save time. Clicking through the dashboards can be distraction as the mass of information is quite fascinating. So, decide:
- General overview: TVM dashboard
- Improve overall security: Security recommendations
- Monitor software that is in use: Software inventory
- Evaluate particular weaknesses: well… Weaknesses
- Details about a client: visit the client’s machine page
- Don’t blame Threat & Vulnerability Management for not being able to patch systems automatically. Implementing this is a big challenge, also for most third-party solutions.
Thanks for reading!
Chris