The journey continues. Microsoft has just announced the public preview of Defender ATP for Android. In this post, I‘d like to give you a short overview of its capabilities and how it fits in MDATP‘s existing features.
Getting started
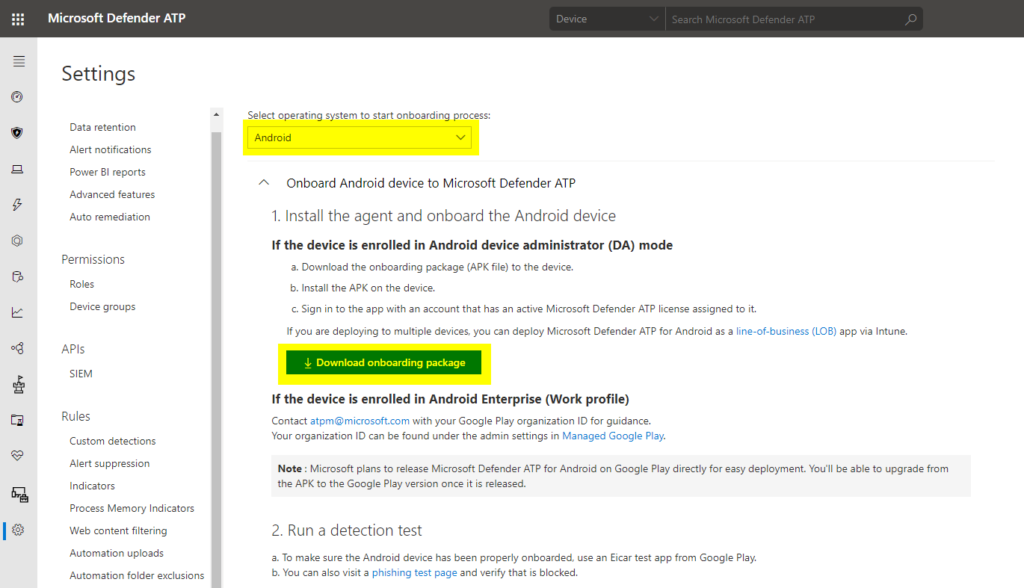
At the moment, the public preview works with standalone or Android devices in Device Administrator mode. You can contact mdatpmobile@microsoft.com to get guidance about Android Enterprise (Work profile) deployment.
The .apk file can be downloaded from the onboarding section in Defender ATP:
Note
All following screenshots are taken from the private preview. However, not much has changed and you will still find your way around.
Local client
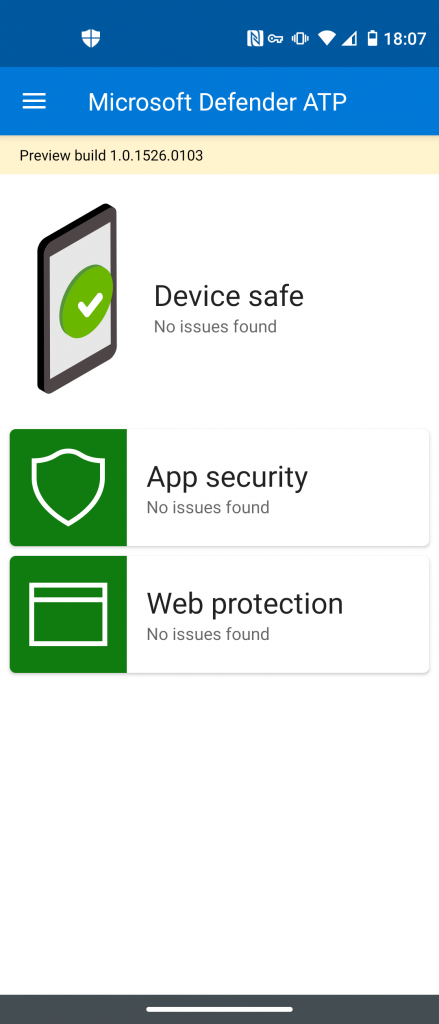
The MDATP client app is visible to the end user on the Android device. So, it is meant to show some status information about findings and security problems. At the moment, it is not possible to hide it.
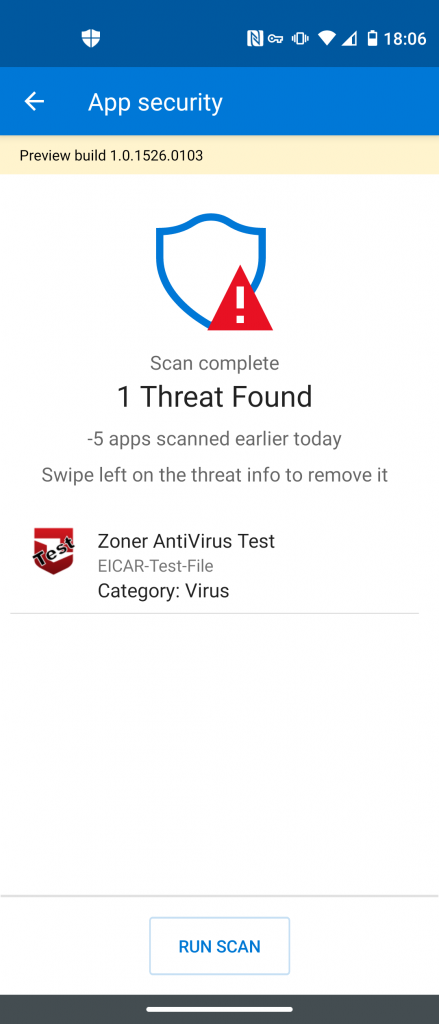
MDATP for Android has two components at the moment: app security and web protection.
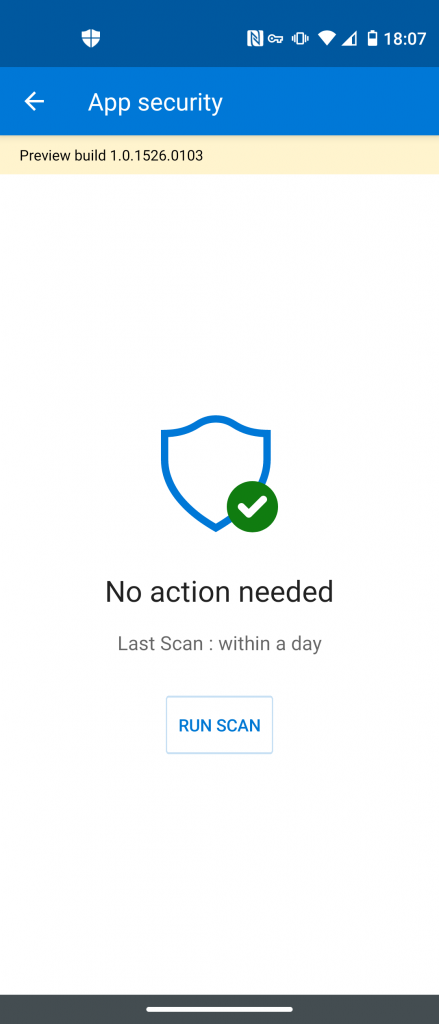
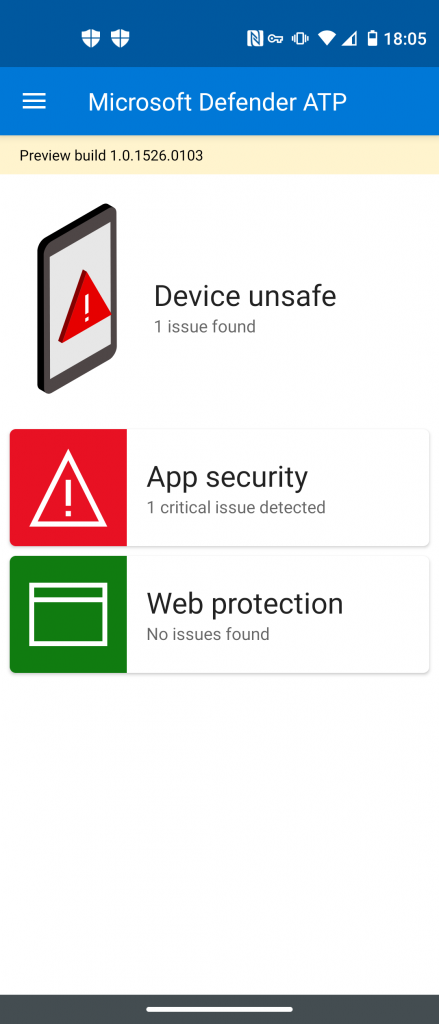
App security will detect malicious applications installed via the Google Play Store or manual .apk installation:
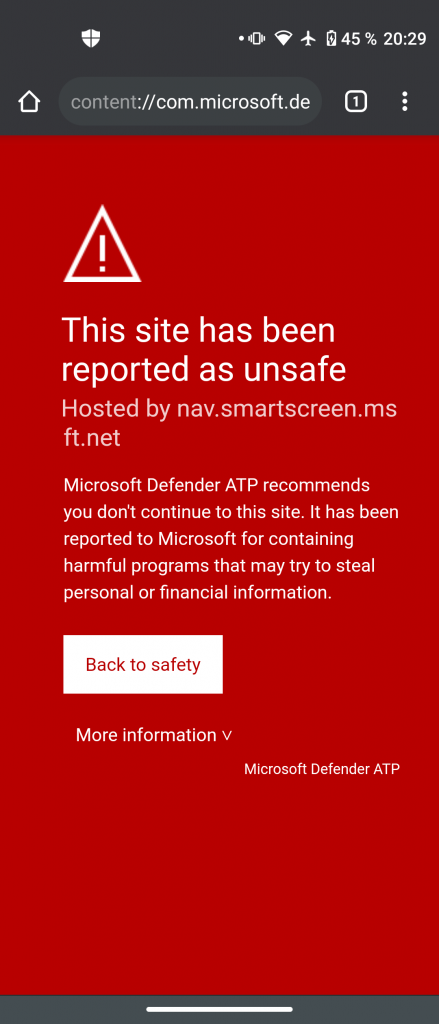
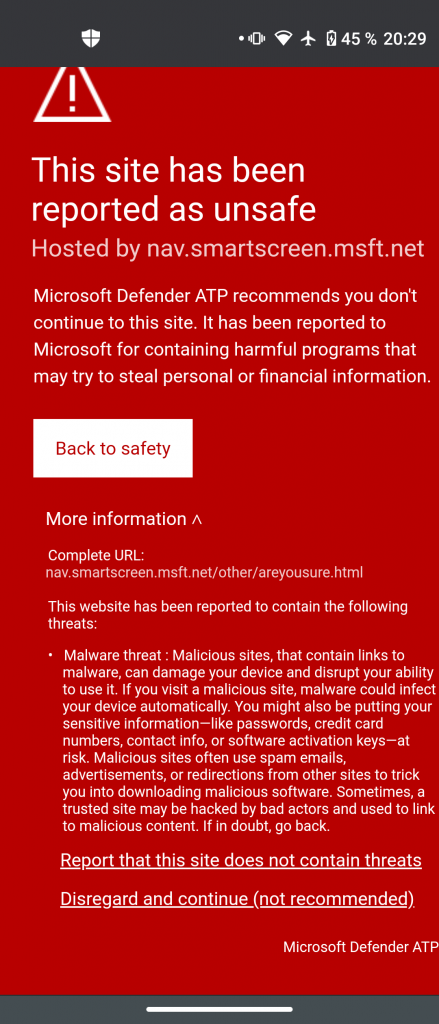
Defender ATP will also register a VPN connection to get access over remote resources the user tries to access. Malicious content will be detected and alerts the user by a quite familiar looking message we already know from SmartScreen on Windows 10 (Edge browsers):
The user has the option to “Disregard and continue” the warning. This will increase the alerts severity in the MDATP portal from Informational to Low or Medium depending on the incident.
What about battery life?
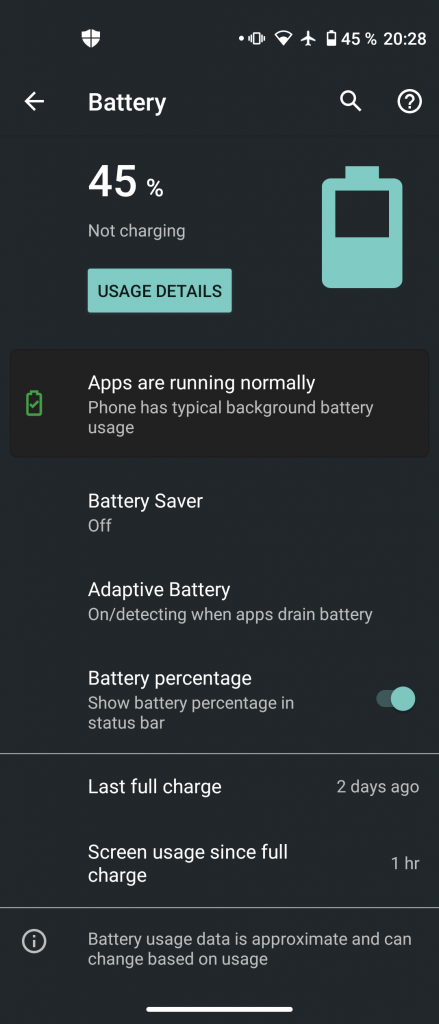
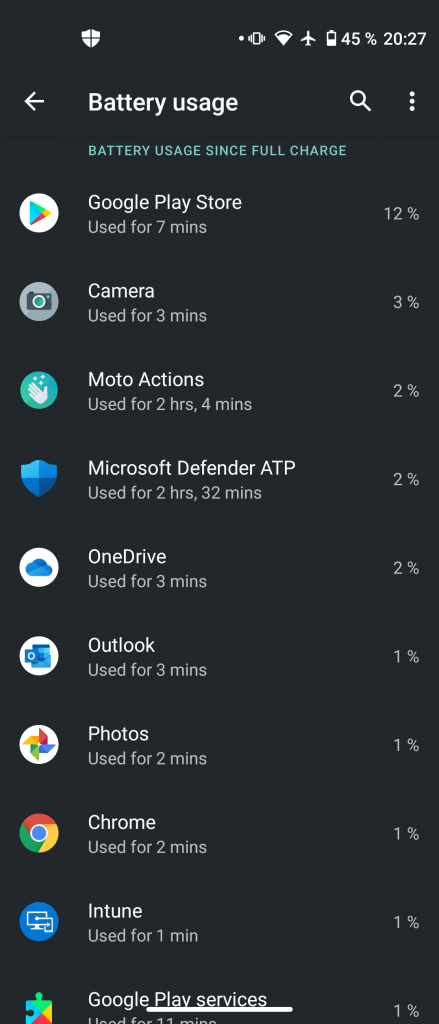
In my testing, the MDATP for Android preview ran just fine causing no significant decrease in battery life. It didn’t even trigger any “xy is running in the background” Android alert:
As you can see in the screenshot on the right, Microsoft Defender ATP consumed 2% of battery charge over 2 hours and 32 minutes, so about 1 percent per hour. Over the course of 24 hours this might be significant, losing about 10% on a normal workday seems to be reasonable, however. Of course, there is always room for improvement. 😉 It’s an early preview after all.
Management in the MDATP portal
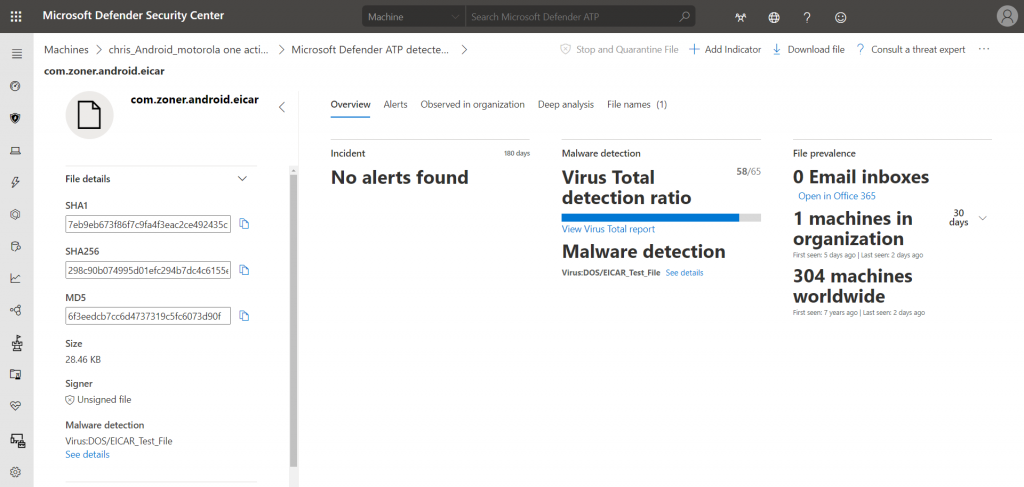
At the moment, the Android version of MDATP only has limited capabilities in the MDATP portal. However, alerts will be generated just fine. We even get the exact name of the APK and the file hashes:
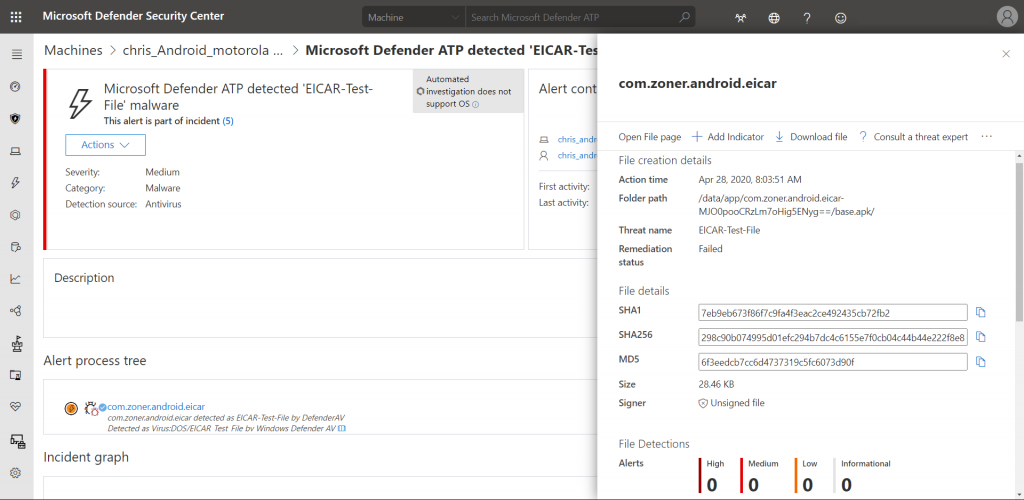
Each detected file also gets a seperate file page, just like on Windows 10:
The timeline of each Android device only consists of alert activities at the moment:
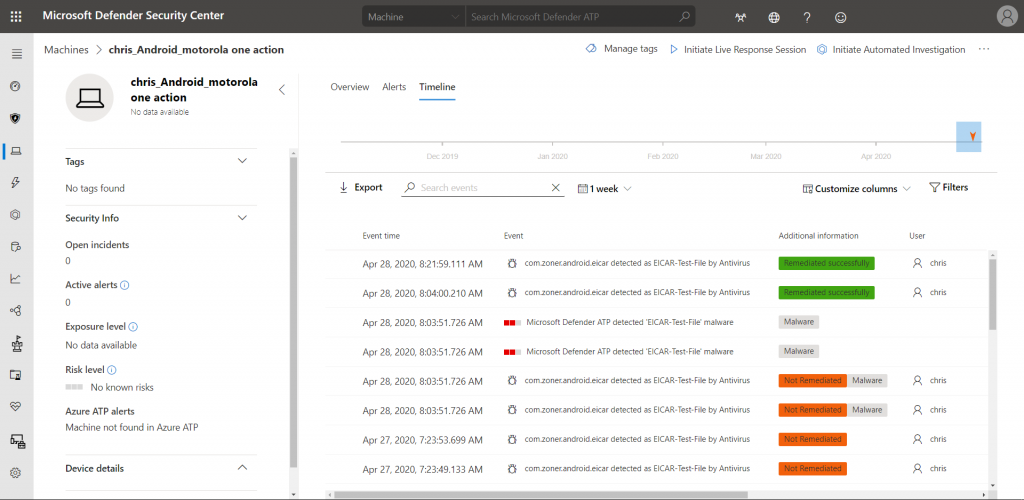
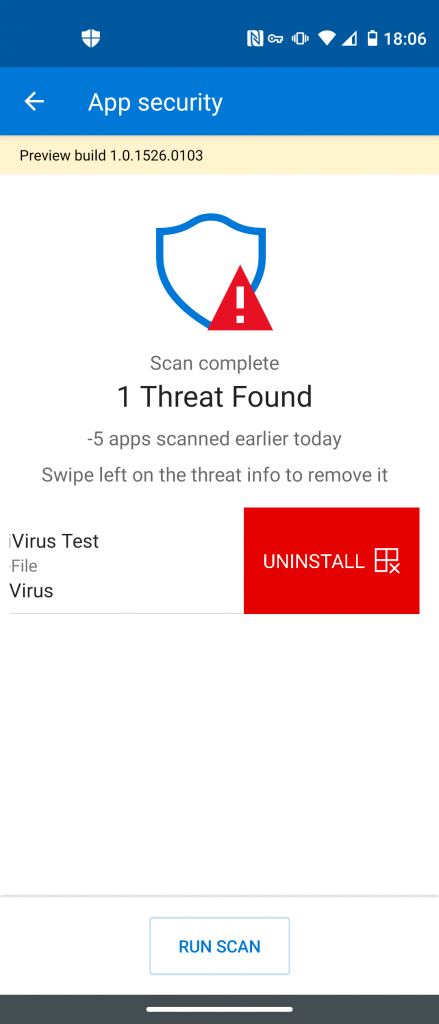
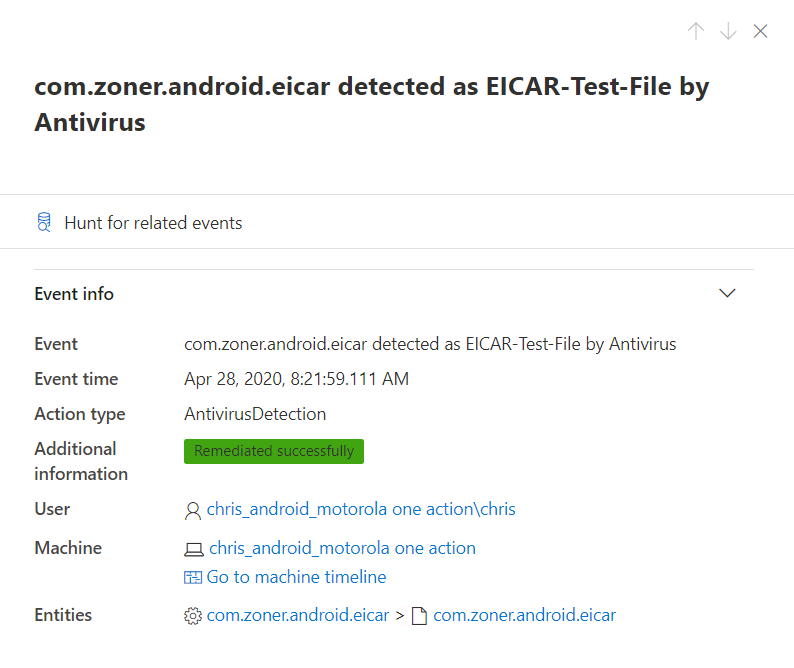
Please note that MDATP for Android is not capable of uninstalling malicious applications. Like seen in the “Local client” chapter, the user will be notified and has to start the process manually. Once done, the alert will switch over to “Remediated successfully”:
Using device risk for Conditional Access
Conditional Access is capable of using mobile devices’ risk state since quite some time now. However, only via Mobile Threat Defence partners. With MDATP for Android, this changes. It can now be natively connected in the Intune or Endpoint Manager admin center:
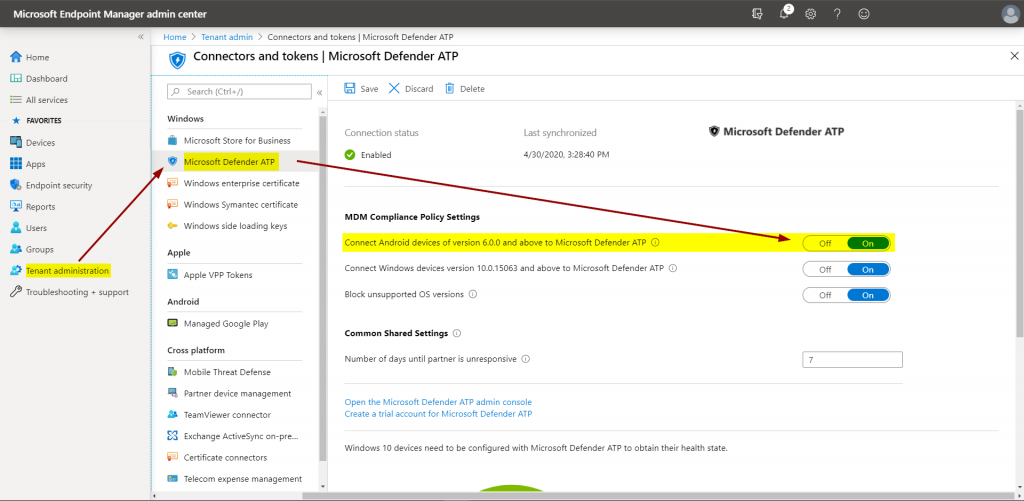
The corresponding setting is available in Android compliance policies:
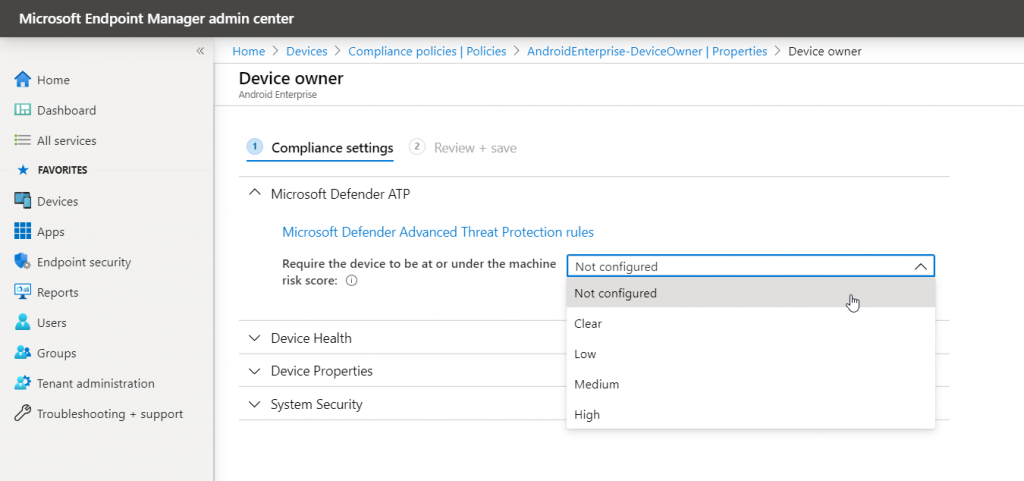
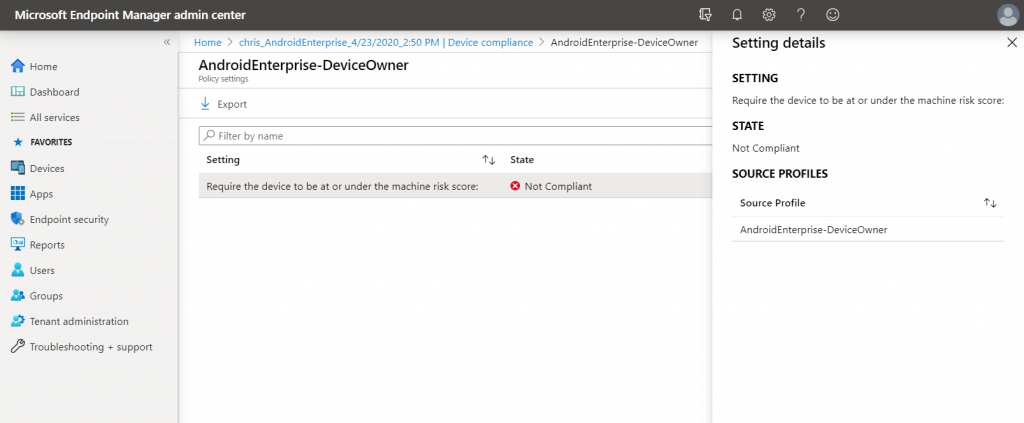
Any risk score that exceed the risk score you define the device will be marked as non-compliant:
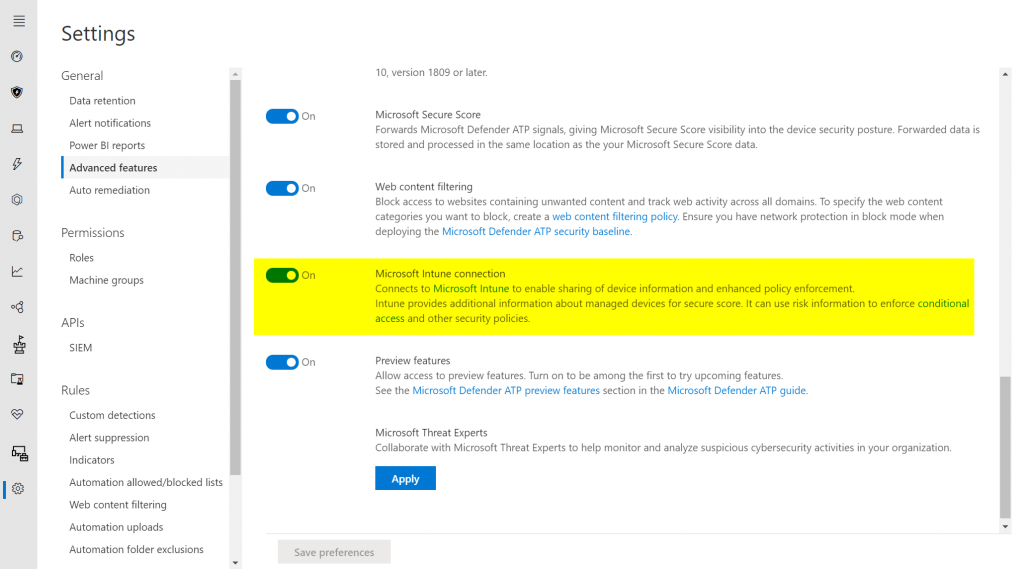
Just like for other operating systems, the Intune connector in MDATP must also be enabled:
Summing things up
Microsoft keeps extending MTP with enhanced capabilities and brings it to more and more plattforms. Microsoft Defender ATP for Android now allows to protect Google’s OS natively which is especially handy for access control via Conditional Access. Now let’s wait for the also announced iOS/iPadOS version.
If you want to learn more about the Microsoft Threat Protection platform have a look at these posts:
- Microsoft Defender ATP for Linux
- Microsoft Defender ATP – network control made easy
- Microsoft Threat Protection – unified incidents
- Microsoft Threat Protection – unified hunting
- Automate MDATP response with Microsoft Flow
- Threat & Vulnerability Management – improve client security with MDATP
Thanks for reading!
Chris