It’s Ignite time. Again! In this post I cover the Microsoft Ignite 2021 security news that have been announced at the second virtual version of Microsoft’s conference.
Azure Active Directory
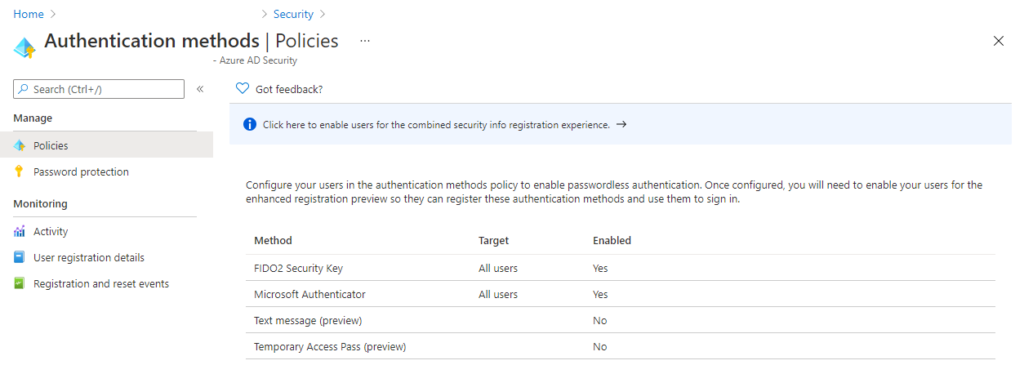
Passwordless authentication is now generally available, Temporary Access Pass (a new feature providing a time-limited code to users) is now in preview. The latter allows users to onboard to passwordless authentication methods without ever having a password to begin with.
My opinion
Passwords are a thing of the past. Even today, I’m working without even knowing my password. FIDO2 and the Authenticator know being GA is a great signal to start using those in combination with Hello for Business depending on the use case.
Temporary Access Pass are now able to fix the boot strap problem we had until now.
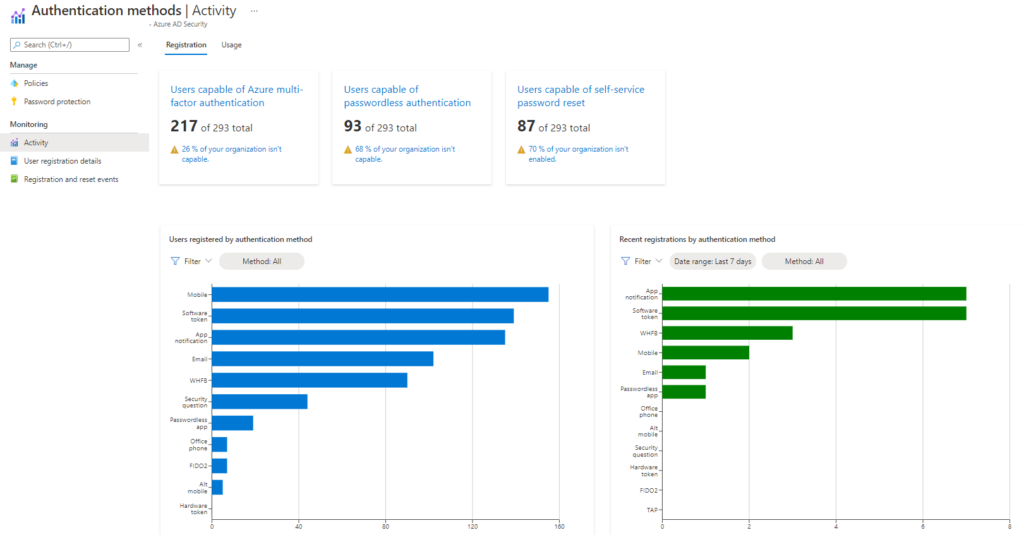
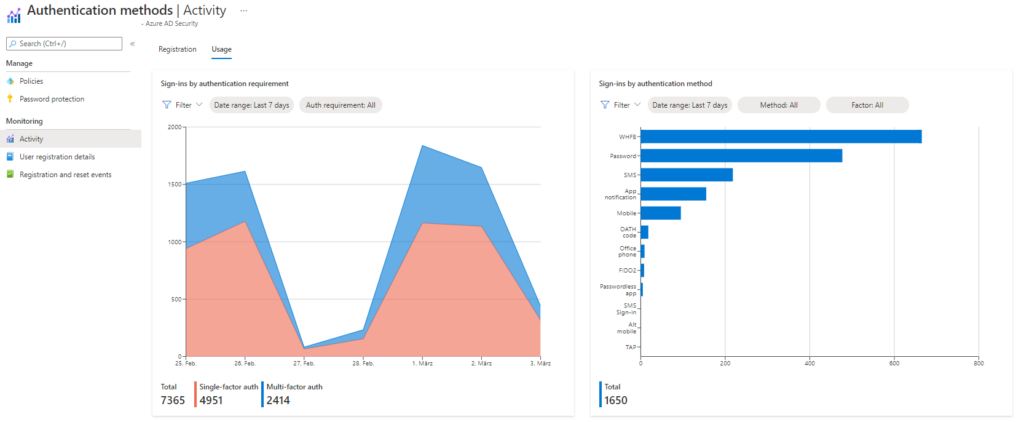
New authentication activity capabilities allow for a more comprehensive monitoring of authentication mechanisms.
My opinion
User experiences require analytics tools for administrator to make sure they are hassle-free and don’t cause frustration. Also, telemetry can help to find gaps in your current authentication solutions.
Azure AD Conditional Access authentication context is now in preview. This enhancement allow more granular controls based on user actions or the data they are accessing.

My opinion
While Conditional Access has been the core feature for Zero Trust, it has also been not that flexible. With authentication context, we will be able to get more granular control for certain scenarios.
Azure AD External Identites are now generally available. They offer different capabilities to manage secure access for external accounts in your Azure AD containing self-service sign-up, Azure AD Identity Protection, and social sign-in capabilities (e.g. Google accounts, Facebook, etc.).

My opinion
Working with external users is the new normal. Integrating them as tightly as possible is therefore very welcome.
Access reviews for guests in Microsoft Teams and Microsoft 365 groups are now also generally available allowing sponsors to clean up accounts not required anymore.
My opinion
Unfortunately, access reviews for guests are still linked to pre-defined users and can not be individually assigned to the account that originally created the invite.
Azure Sentinel
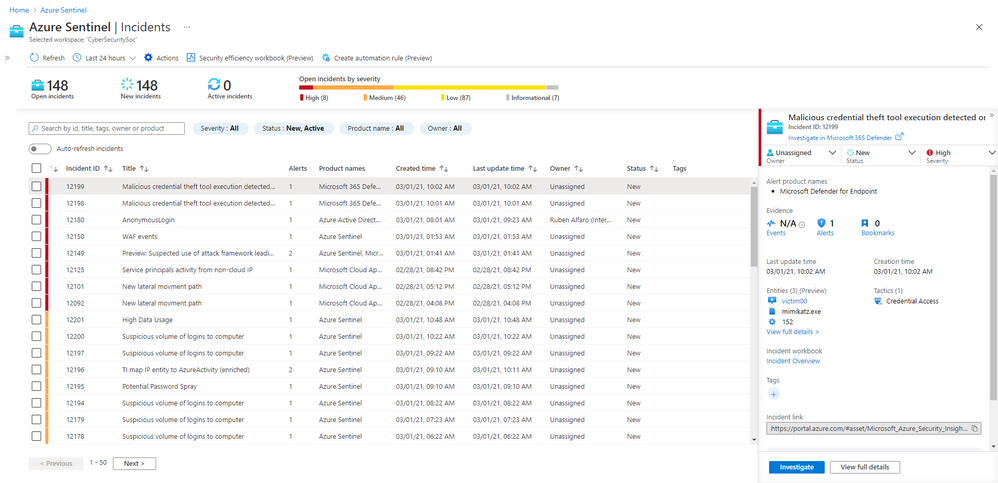
Incidents from Microsoft 365 Defender are now synchronized to Azure Sentinel. Each incidents provides the direct link to M365 Defender to investigate in more depth. Incident status and assignments are now also synced between both systems.
My opinion
While many customers still criticize for the number of security dashboards this might be a step in the right direction. Microsoft 365 Defender and Azure Sentinel are two different tools, however, customers just want an experience that is as simple as possible no matter if its SIEM/SOAR or XDR.
Azure Sentinel now offers over 100 built-in connectors with more than 30 added just now. A list can be found here: https://techcommunity.microsoft.com/t5/azure-sentinel/30-new-azure-sentinel-data-connectors/ba-p/2176315
If you want to learn more about connecting data sources I’d recommend this docs article: https://docs.microsoft.com/en-us/azure/sentinel/connect-data-sources
As a preview, Azure Sentinel Automation helps to simplify common actions based on conditions (e.g. change user assignment or severity). Logic App playbooks can also be used as actions just like they can already be assigned to individual analytics rules. Allowing this at a global level using Automation is a welcome addition.
Microsoft also added new pre-built playbook connectors that let you block IPs using Azure Firewall, isolate endpoints using Defender for Endpoints, and update a user’s risk state in Azure AD Identity Protection.
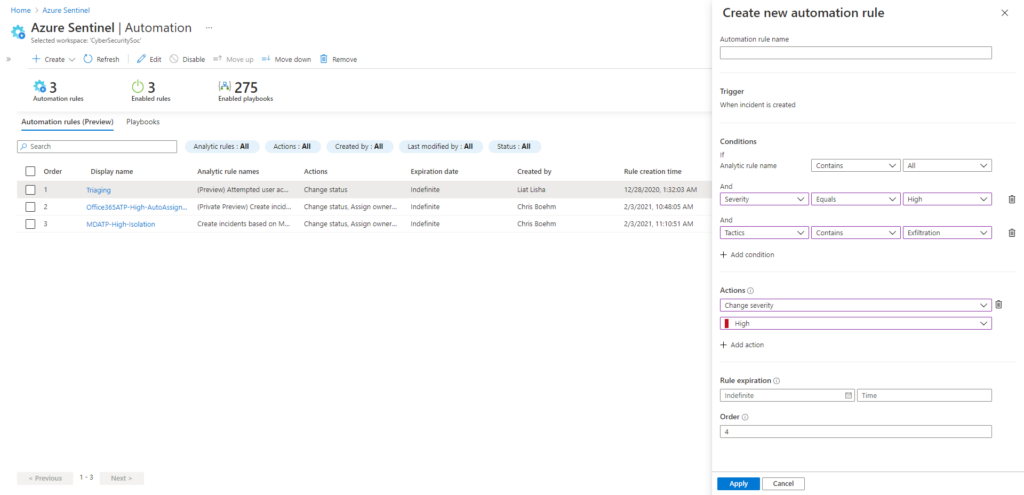
Azure Sentinel Notebooks, introduced at Ignite 2020 in their redesigned experience using Azure Machine Learning, are now also generally available.
My opinion
It’s been a while now since Azure Sentinel was released, still fun to look at the speed it evolves.
Microsoft 365 Defender
Microsoft recently added the new unified experience to the Microsoft 365 security portal often referred to as “portal convergence”. Microsoft 365 Defender can now be used to directly manage, configure, investigate, and remediate across endpoints, email, and identities.
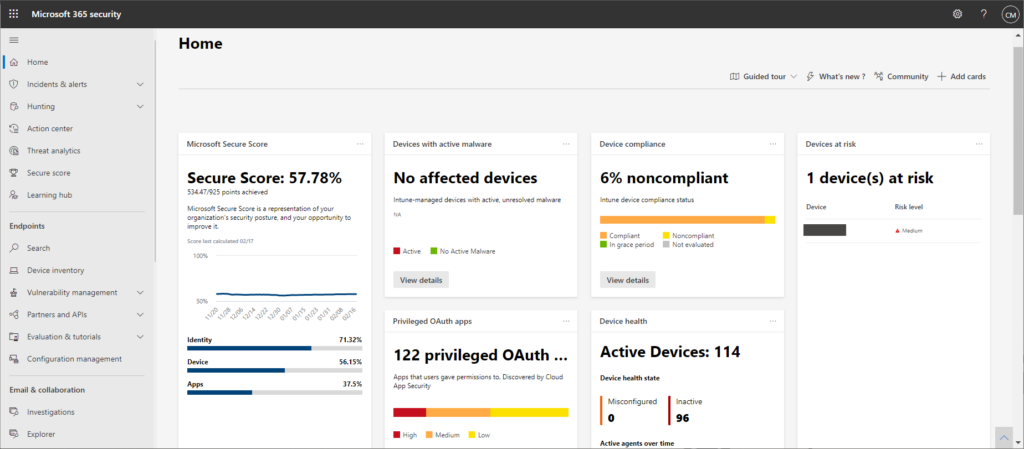
Some features (including the new unified investigation pages) are only available in Microsoft 365 Defender.
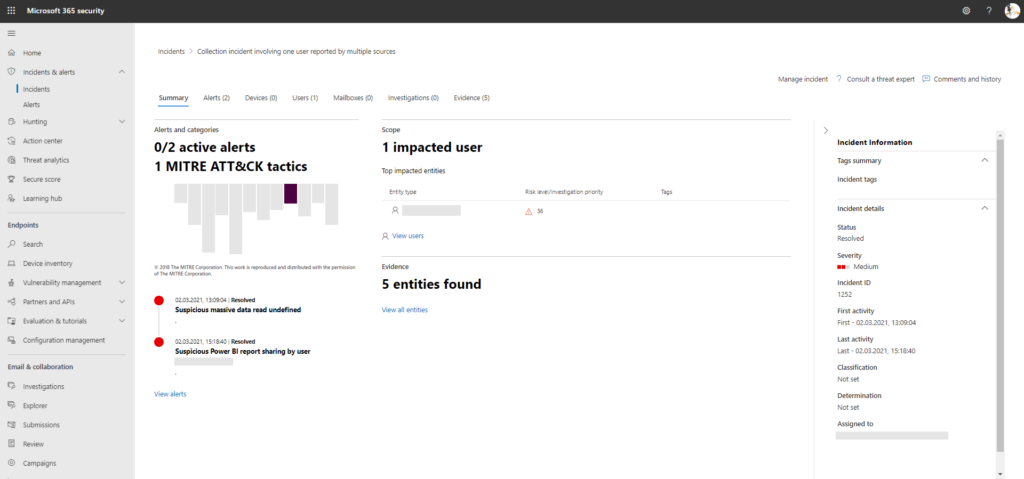
Most notable: configuration of Defender for Office 365, Defender for Endpoint, and other tools from the old security & compliance center have now been migrated to Microsoft 365 Defender. Users can be forced to use the new portal by enabling portal redirection (available for Defender for Office 365 and Defender for Endpoint). I will discuss the new converged experience in a dedicated blog post to cover all aspects.
My opinion
This is one of my favorite changes since Microsoft announced the vision for a unified threat protection dashboard at Ignite 2018 which I attended in Orlando. I often asked myself why it took so long, but now we are finally here.
Windows Server 2022 / Edge devices
Windows Server 2022 is now available in preview. Already know from Windows 10, the next LTSC release of Windows Server will included “Secured-core” – a hardware root of trust built upon TPM 2.0, System Guard and Windows’ Virtualization-based Security (VBS) capabilities.
Windows Server 2022 will also provide AES-256 support for SMB as well as improvements to the the Windows Admin Center (v2103), now also available as part of the Azure Portal in a public preview. TLS 1.3 will be enabled by default.
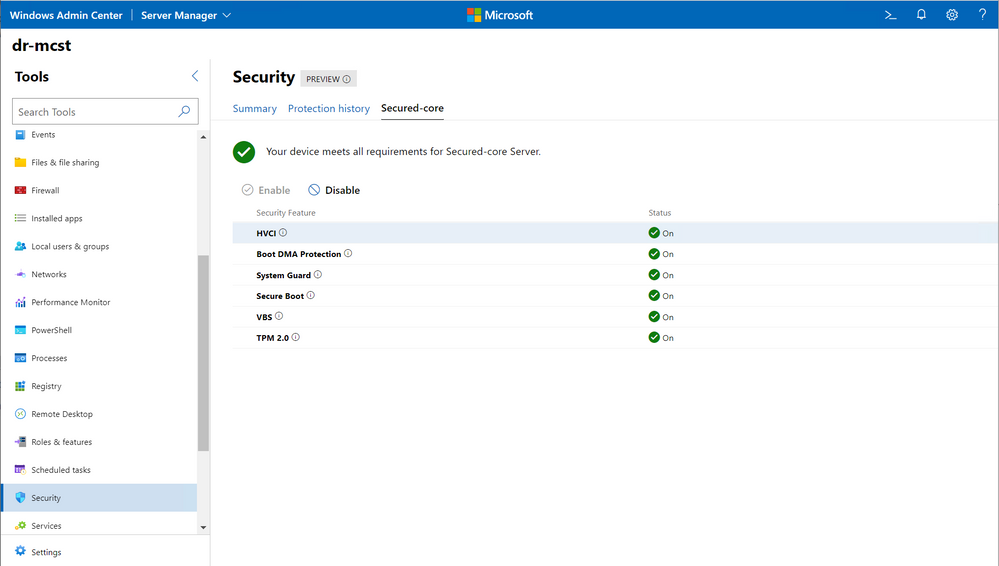
Windows Server 2022 will be generally available later this year. The preview can be downloaded here: https://www.microsoft.com/en-us/software-download/windowsinsiderpreviewserver
“Edge Secured-core” extends this certification by identifying edge IoT devices. This label is part of the Azure Certified Device program, making it easier to select certified devices. As an addition, those will also include built-in support for Azure Defender for IoT.
My opinion
I’m mostly doing cloud security projects at the moment, but hybrid datacenters are still a thing at most customers. Windows Server 2022 seems to be an evolved version of Server 2019 which is already a reliable and secure OS.
Azure Security Center / Azure Defender
Azure Defender now offers improved alerts for Windows Server 2019 including EDR support as part of Microsoft Defender for Endpoint. Incidents are now aligned to Azure Sentinel’s user experience.
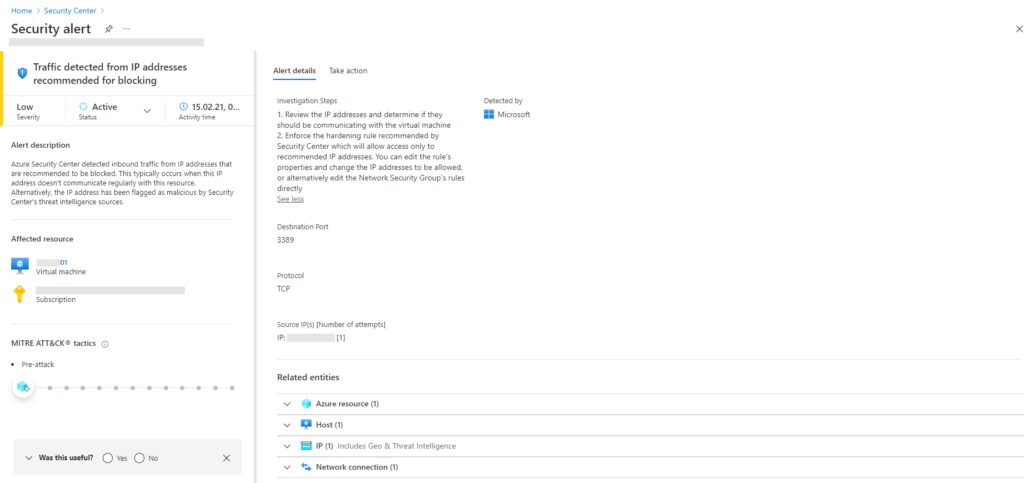
Azure Security Center now includes the security status of Azure Firewalls through integration with the Azure Firewall Manager.
Microsoft Information Protection
While Microsoft sees Information Protection as a compliance solution, it still has significance for security as well. The following capabilities have now been announced
Co-authoring and AutoSave are now available in preview on Microsoft Information Protection-encrypted documents, even in the full Microsoft 365 desktop apps (Windows and Mac). The function has to be enabled manually and is a one-way task!
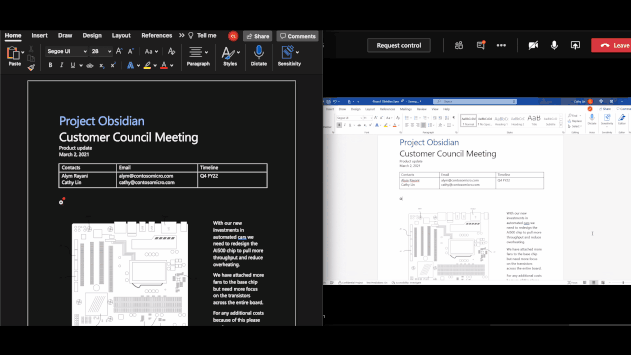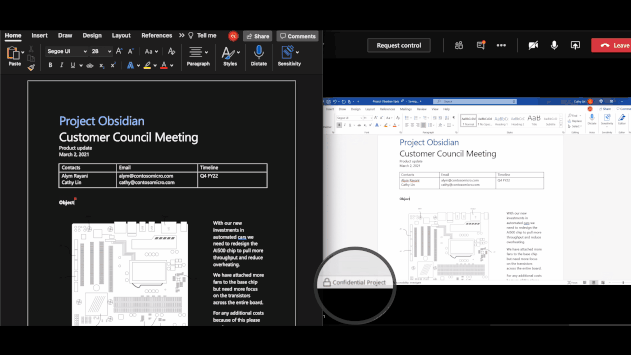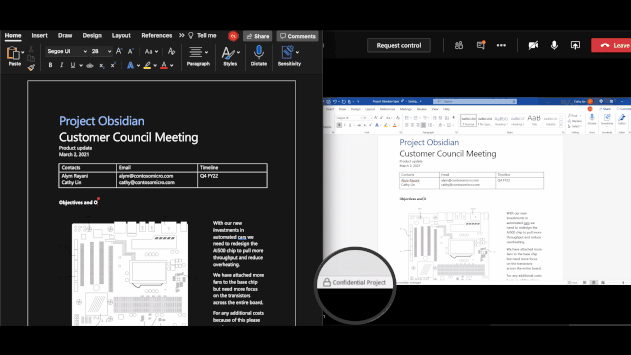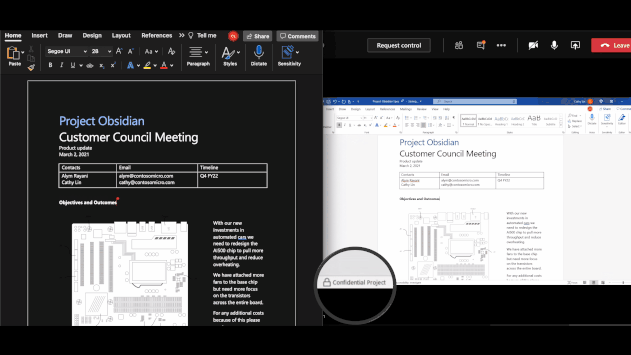
On macOS office apps (version 16.44+), client-based automatic and recommended labeling is now available detecting sensitive content. This was already implemented in Microsoft 365 Apps on the web and the Windows Version of Microsoft 365 Apps.
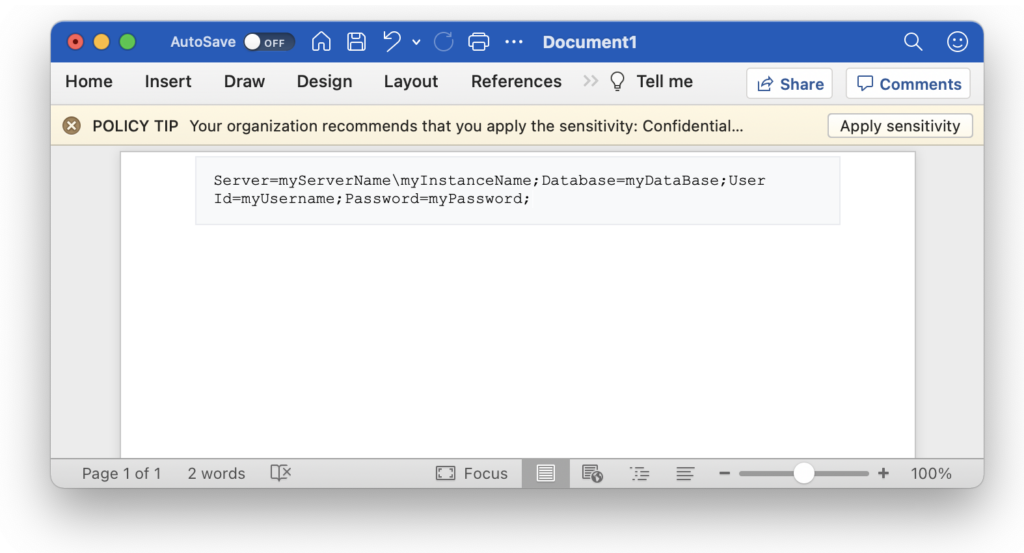
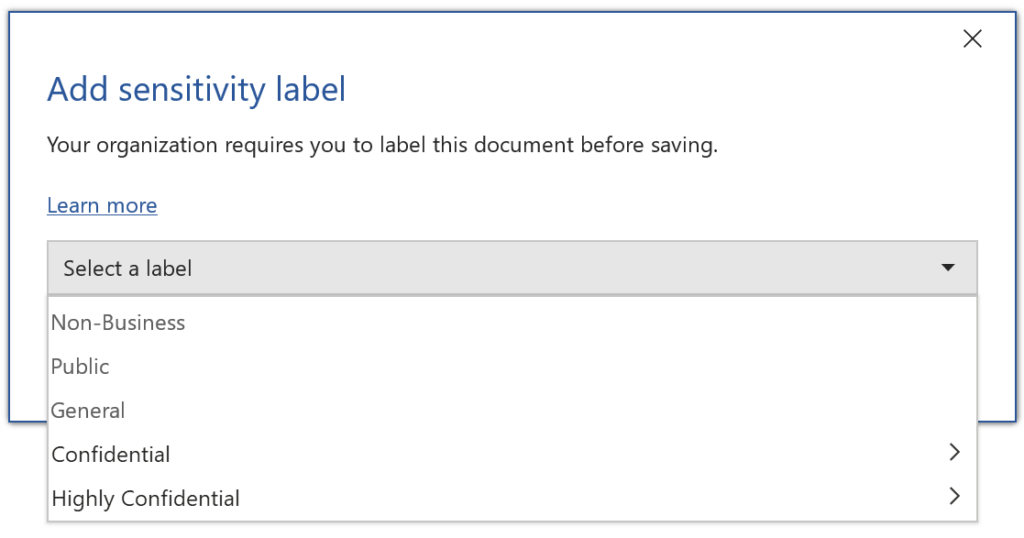
Mandatory labeling is now built-in within Microsoft 365 Apps on all platforms. The Azure Information Protection client is no longer necessary. Customized label policy settings like “Set a different default label for Outlook” and “Exempt Outlook messages from mandatory labeling” will also be respected without the AIP client.
Auditing label activities in Activity Explorer is now filled with data generates by Microsoft 365 Apps also rather than just by the Azure Information Protection Client giving full visibility of all file operations regarding labeling and DLP.
Variables and per-app content marking is now also available natively within the Microsoft 365 Apps on all platforms without the need for the Azure Information Protection client. Web apps will follow soon.
My opinion
Nice additions regarding Information Protection. Co-authoring on encrypted files is a step into the right direction. Making the Microsoft 365 Apps independent from the Azure Information Protection client will also simplify many deployments. Now on my wish list: full feature support of all configuration options without the AIP client.
That’s it for the Microsoft Ignite 2021 Security news.
Thanks for reading!
