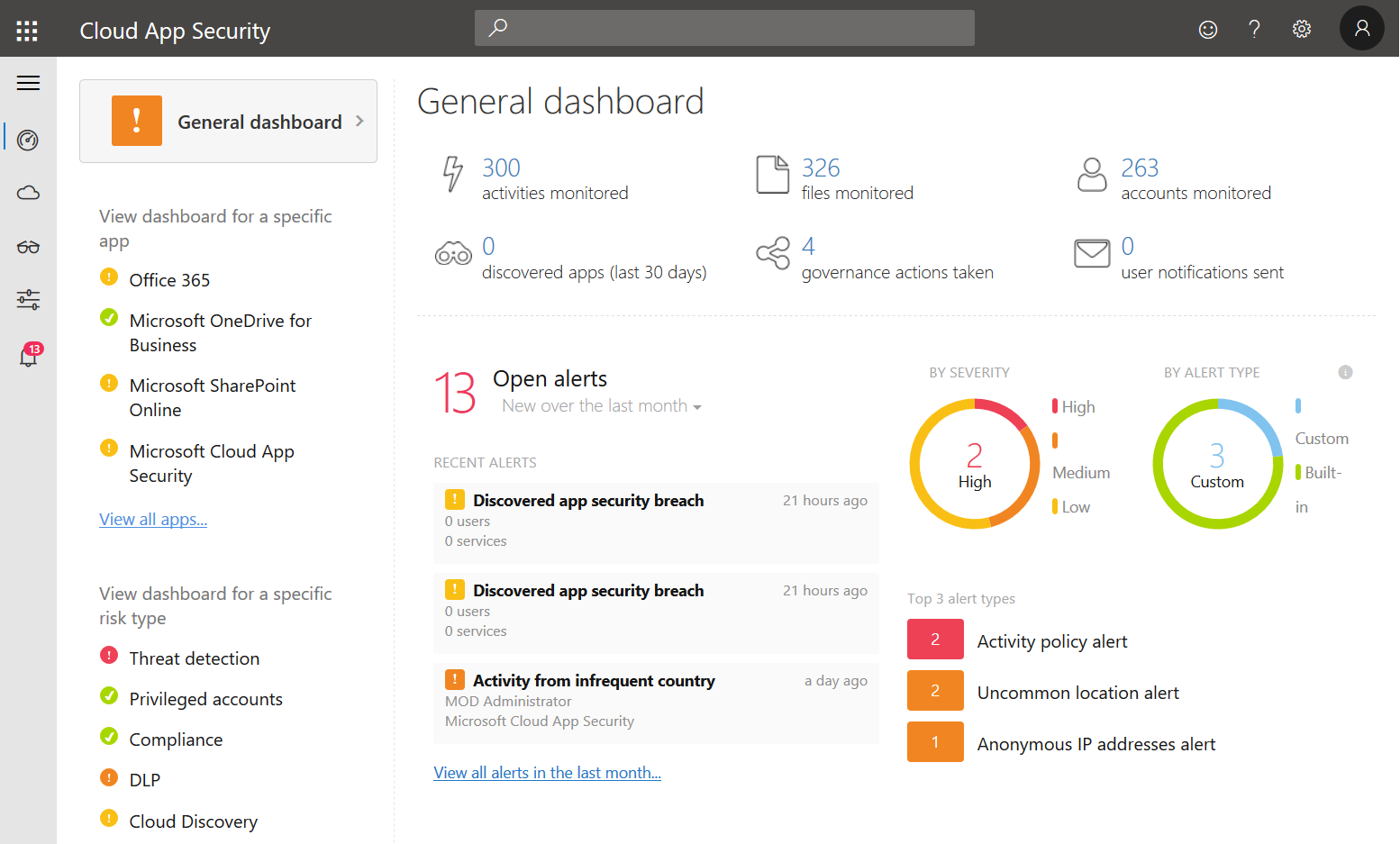
As a Cloud Access Security Broker (CASB), Microsoft Cloud App Security – or MCAS as I will call it in this post – is a central cloud security tool that let’s you gain visibility and control over your cloud services. It also offers a variety of ways to analyse cloud usage and potential threats like information loss.
In this post, I’d like to give you a short introduction by showing 5 reasons why MCAS is quite useful for cloud security administration.
1. Discover cloud usage
We live in a time where fully controlled IT environments are often not a thing anymore. Employees may use the internet as they want at least on their breaks. So, as cloud services (and especially storage) are on the rise you might want to know what is happening and where data may be transfered to. This is where Cloud Discovery in MCAS can help. Based on URLs and IP addresses Microsoft evaluates either Microsoft Defender ATP data or input from on-prem network appliances to give you an overview of cloud apps that are used.
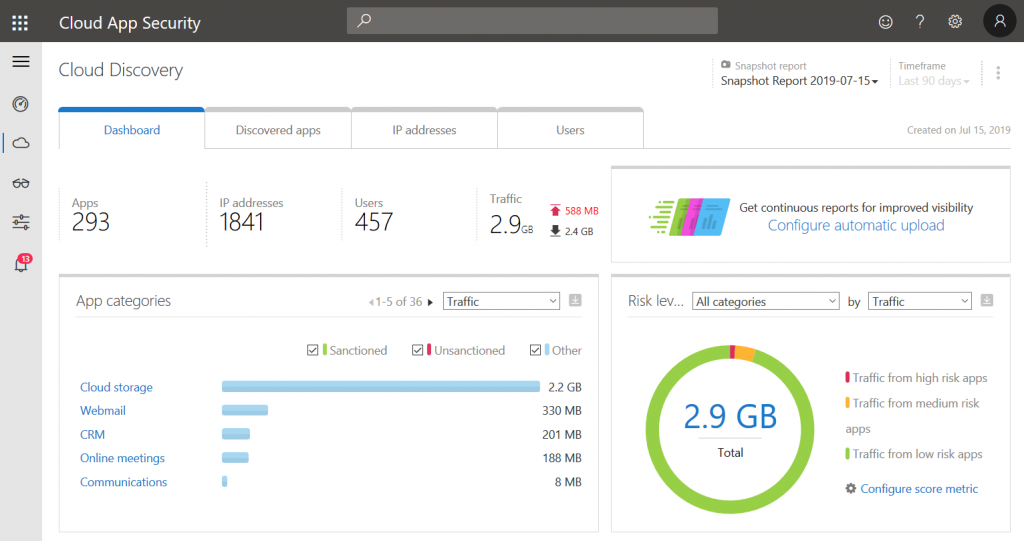
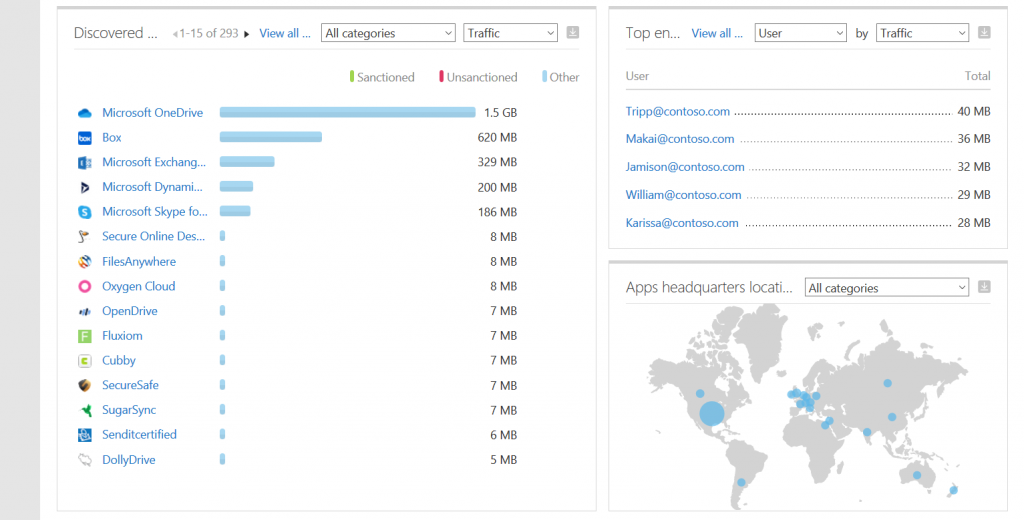
For each detected cloud app MCAS lists telemetry data like traffic and the number of users as well as a score that consists of different checks regarding security, compliance, and legal factors.
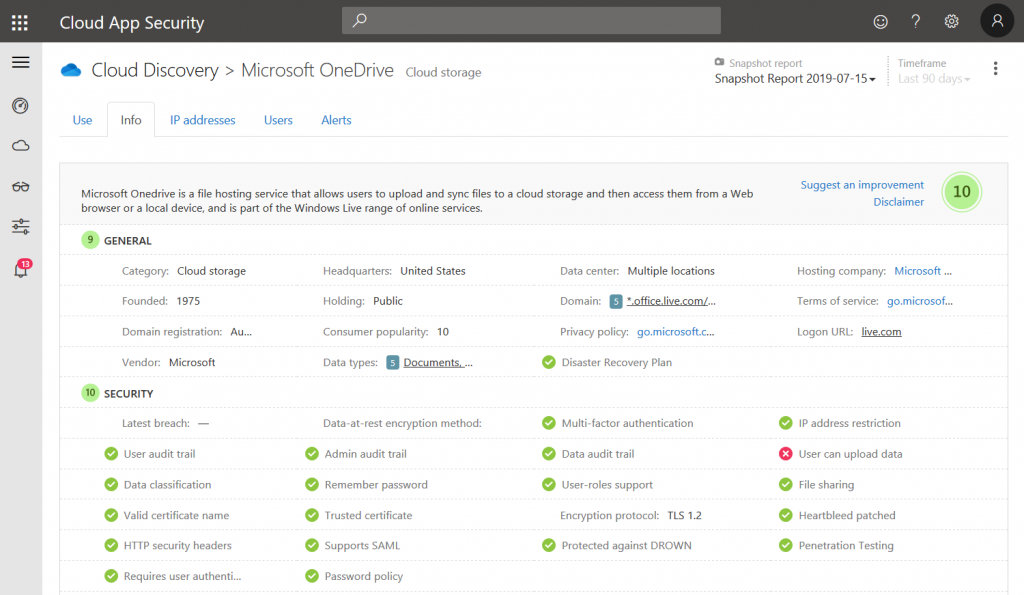
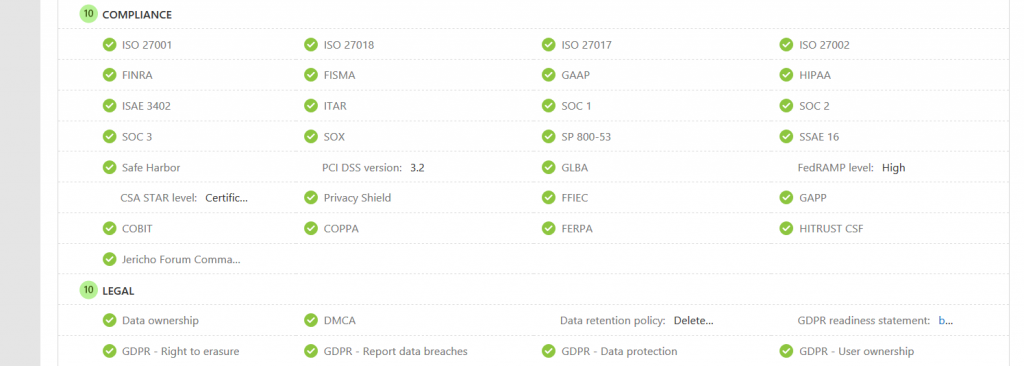
This information is very helpful to evaluate the trustworthiness of a certain cloud app.
2. Session control
Session control is probably the most underrated security feature Microsoft offers. With Conditional Access in Azure AD you can control whether a certain user has access to resources based on different factors like the device they are using, or if they successfully authenticated via MFA. But it has a flaw: once you’re in, you’re in. That is where session control comes to the rescue.
For certain scenarios you might want to limit access to a subset of features, e.g. users should be allowed to use the Outlook Web App on their private devices, but downloads should be prohibited.
If you want to know how to get started please have a look at my previous post on Getting started with Microsoft Cloud App Security Conditional Access App Control.
Yep, you’ve read that correctly. Microsoft Cloud App Security Conditional Access App Control is the official product name.
Now let’s have a look at an example. In this case I configured a session policy that checks whether the device is either Intune compliant or Hybrid Azure AD Joined and will react to any file download:
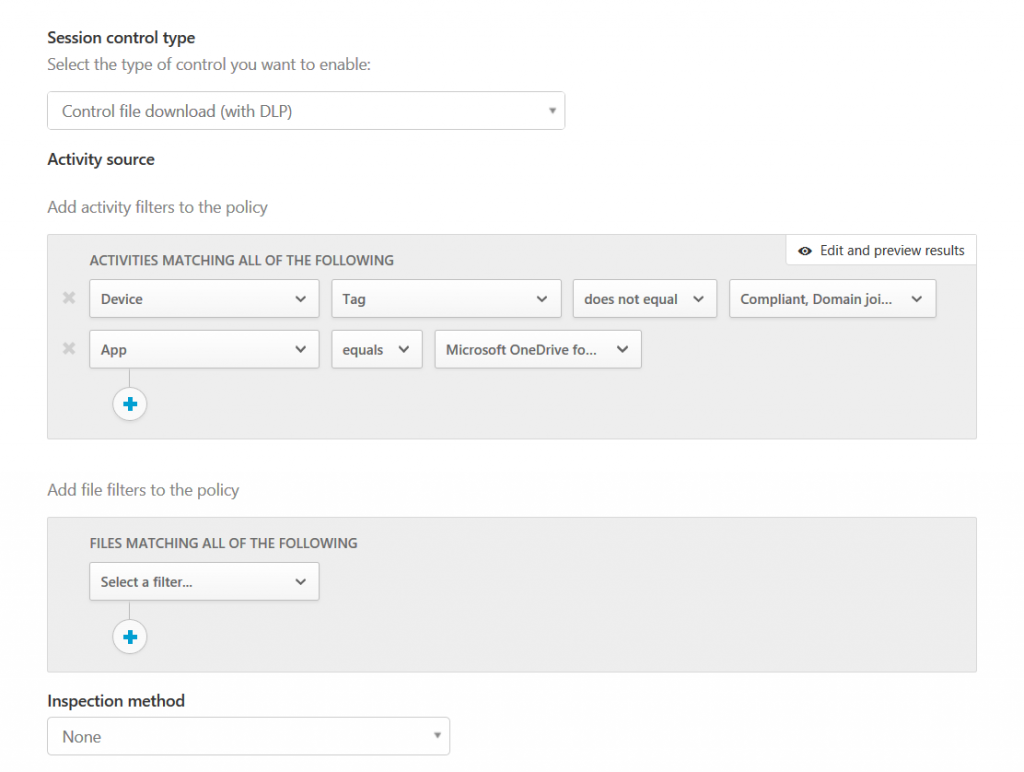
For OneDrive for Business it will then apply a custom permission to the file that still lets the user view read it. However, any other user (especially outside of your organization) won’t be able to get access to the information.
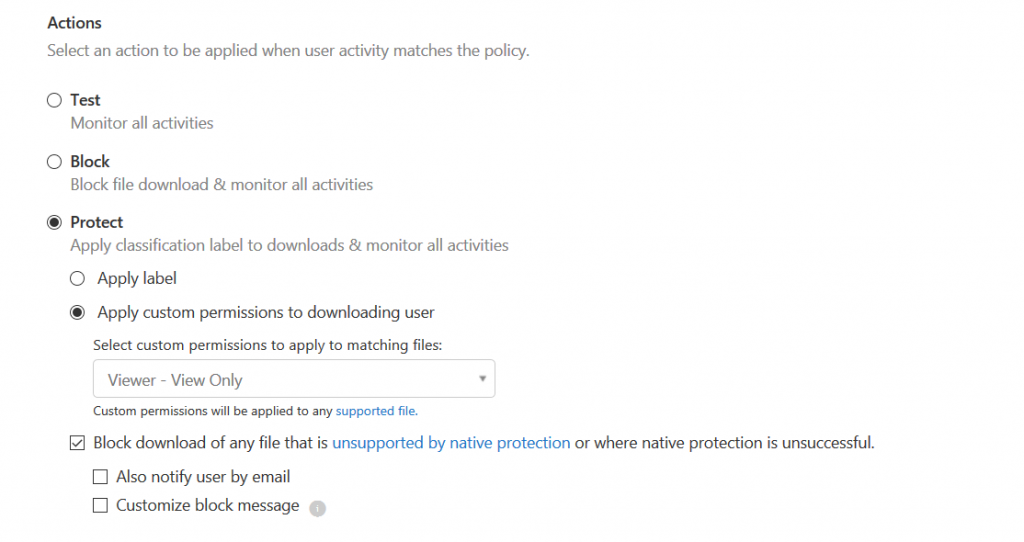
As you can see from the screenshots, there are plenty of other options like blocking the download completely or adding an already existing label to the file. The possibilities are endless.
3. DLP
Data Loss Prevention is an important topic in the cloud. You might want to make sure that sensitive information stays within your organization or at least under your control. Office 365 does offer a powerful DLP engine, however, I never really liked the interface. Good thing that Cloud App Security can help here as well.
With the previous section about session control we already looked at a very specific kind of DLP that can be configured to be applied on-demand based on either Conditional Access or other filters within session policies.
Besides these real-time controls, MCAS can also be used to scan and remediate any unwanted file sharing based on so-called file policies. Here’s an example: let’s check for externally shared files and remove access for people outside you organization automatically. So first, we would filter based on access level and select DLP as an inspection method:
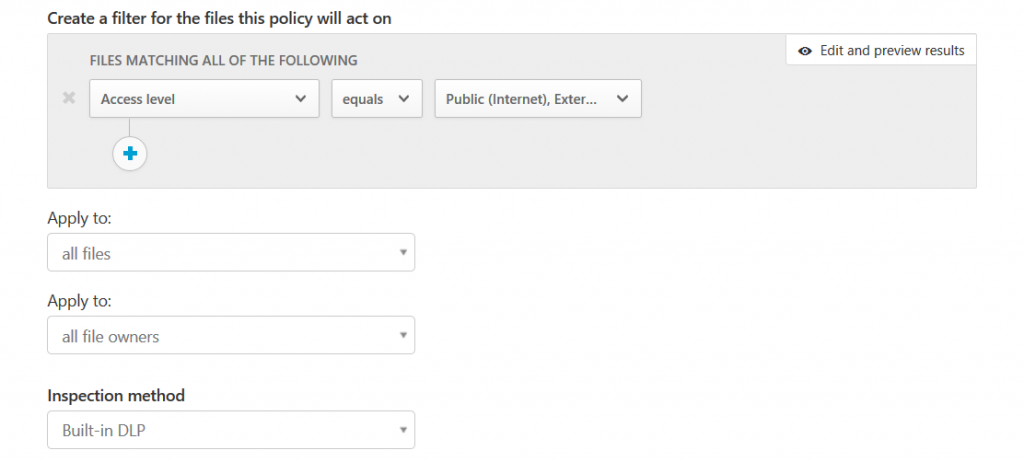
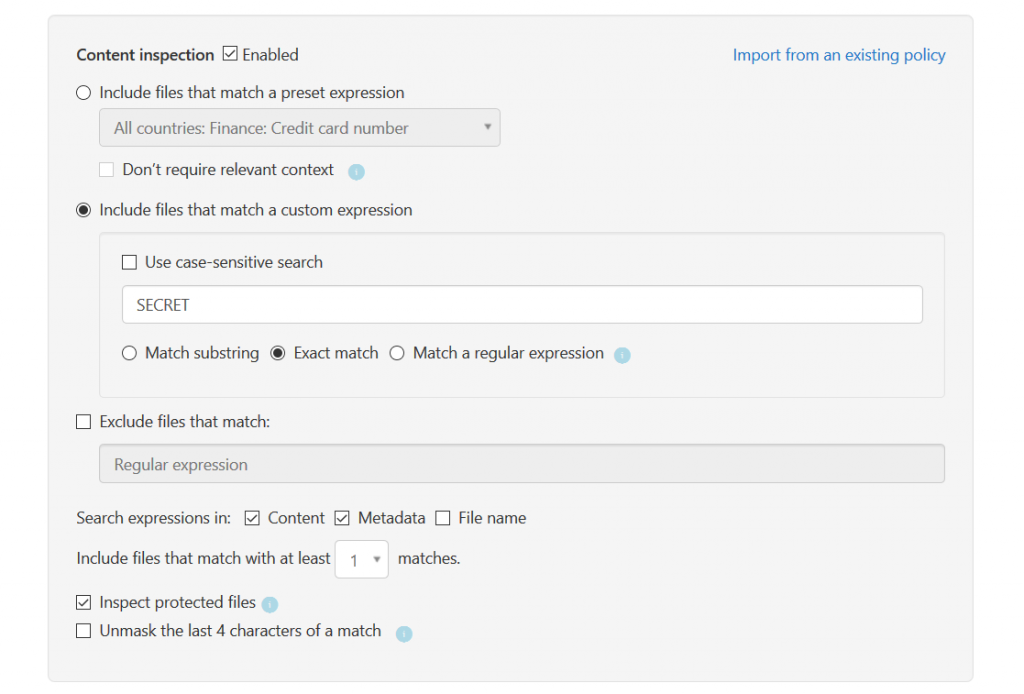
Content inspection would then check files based on a custom expression, a regular expression, or a pre-defined set of known pre-sets like financial data:
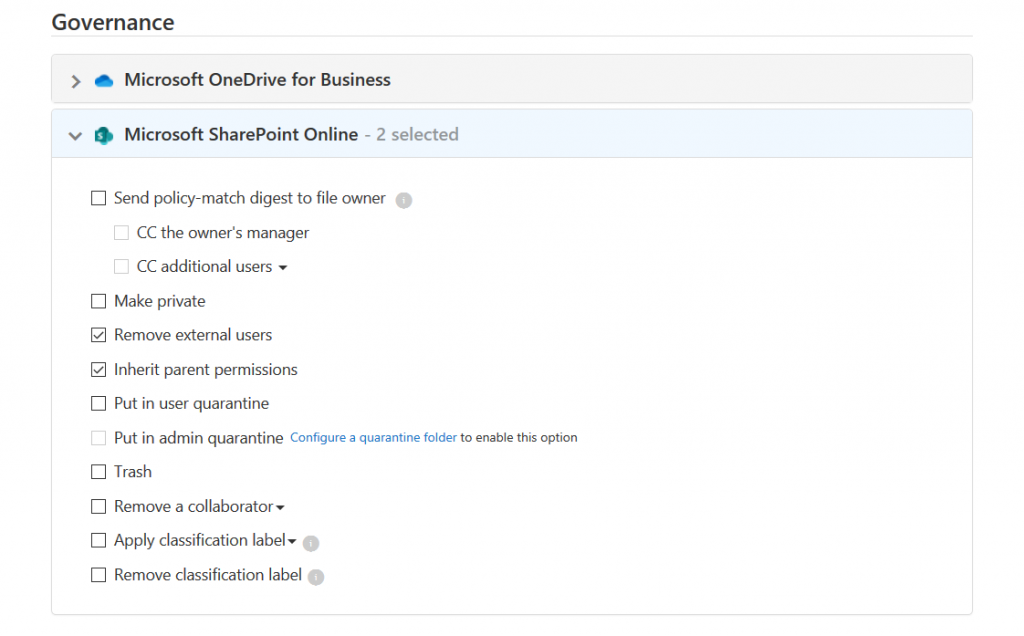
To remediate potential data loss, SharePoint Online (and OneDrive for Business) will then automatically take governance action on the file and remove external users:
Of course, this was as well just an example. You can get much more detailed if you want to.
4. Governance
We already used governance controls in the previous example about DLP. But it goes on. Governance can also be applied to other events.
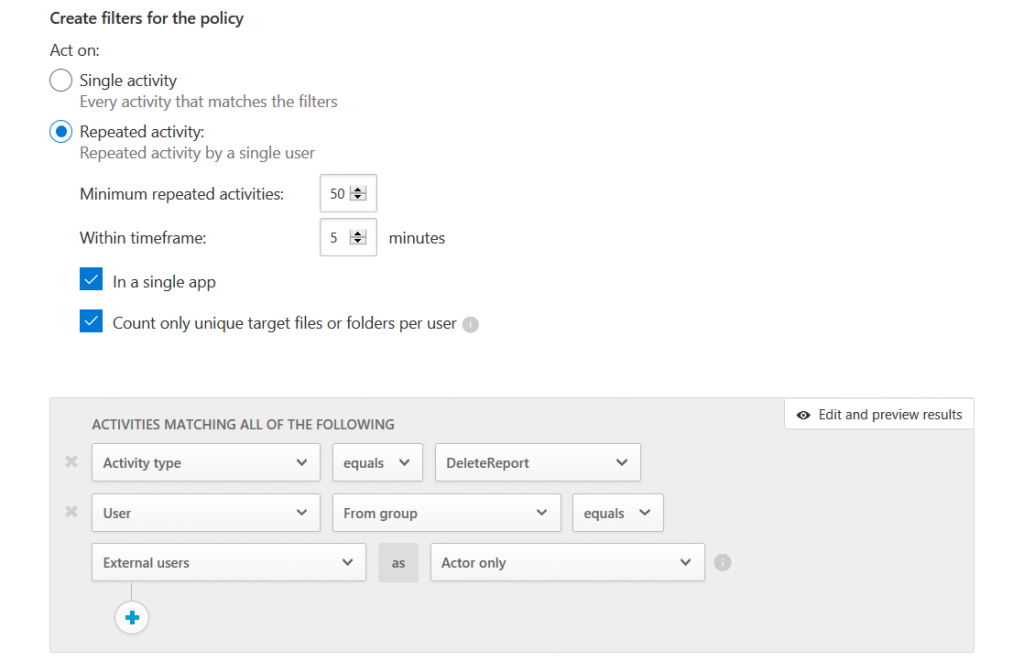
In this example we check whether an external user is mass deleting PowerBI reports:
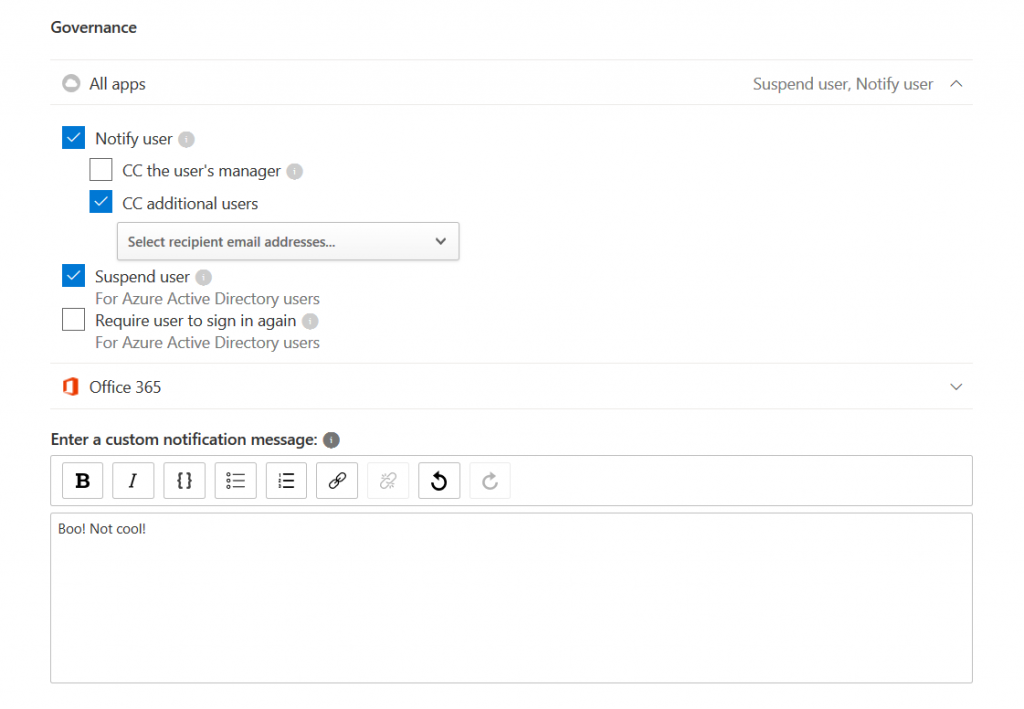
The user will then be notified and suspended:
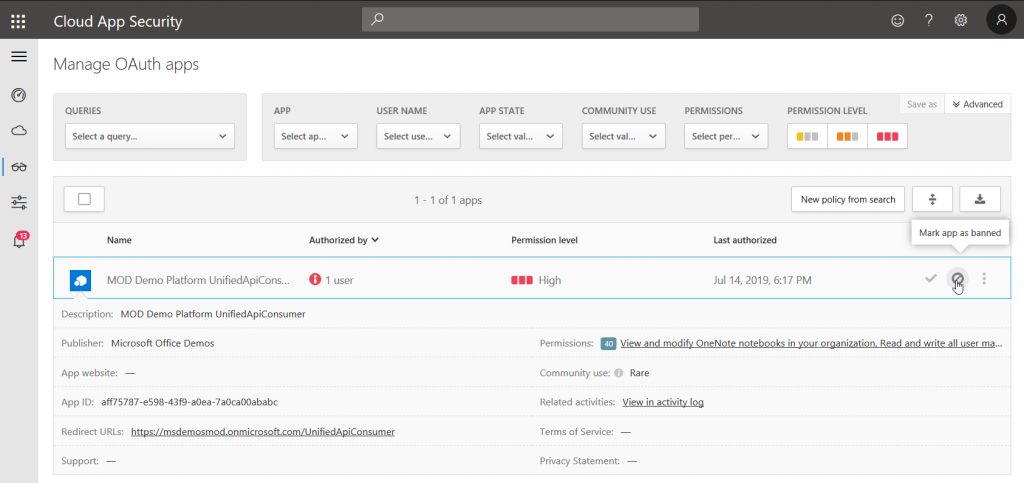
Another example for governance is the control of OAuth apps that are attached to Azure AD. In MCAS, you can either approve or ban them:
5. One ring to rule them all
Central integration of security controls is a key benefit of using MCAS. Here’s a list of features that are importing data:
- Azure AD
- Azure AD enterprise applications
- Conditional Access
- Azure AD Identity Protection
- Intune
- Microsoft Defender ATP
- Azure ATP
- Office 365 ATP
- A vast amount of third-party network appliances
- Azure Information Protection
- Office 365 DLP
- Office 365 audit log data
- Azure Security Center
- Azure subscription activities
- Third-party software like AWS, Box, Dropbox, G Suite, Okta, Salesforce, ServiceNow
So as you can see, MCAS really is a powerful single instance that can be used for central tenant security & compliane management.
Thanks for reading!
Chris