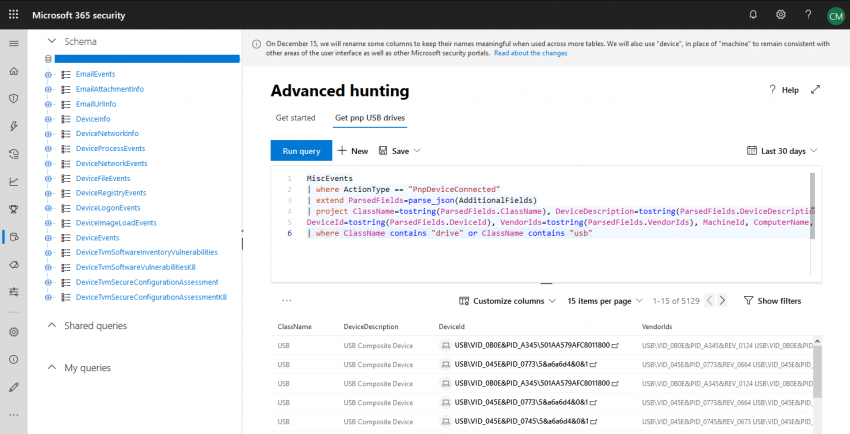
Note This post is part of a series about Microsoft Threat Protection. You can find part 2 about unified incident management here: https://chrisonsecurity.net/2020/01/24/microsoft-threat-protection-unified-incidents/ When you work on security incidents, information is key. What is just as important: correlation. The value of data heavily increases if it can be associated with other signals. At Ignite 2018,…
Category: Blog
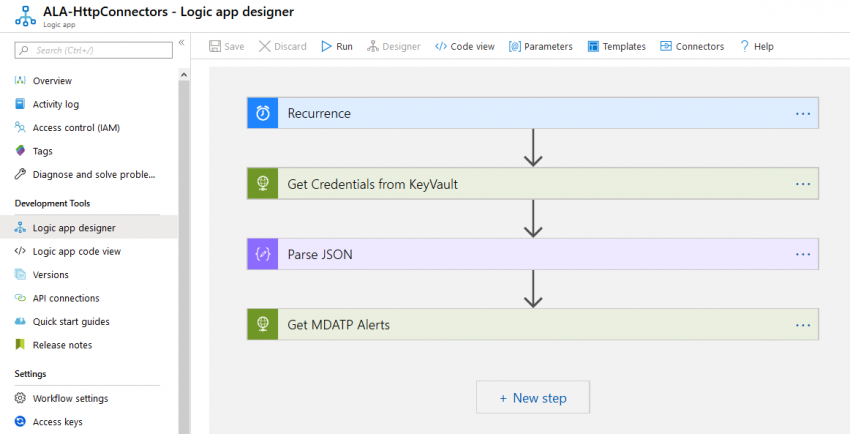
MDATP + Azure Logic Apps: Default connectors vs. HTTP REST
Automating security rocks! In a previous post I showed how to get started with Microsoft Defender ATP and Microsoft Flow: https://chrisonsecurity.net/2019/10/22/automate-mdatp-response-with-microsoft-flow/ Now, lets get a bit more into detail about automating security workflows. Unlike last time, I will use Azure Logic Apps instead of Flow. Both technologies are quite similar, however, they differ in licensing…
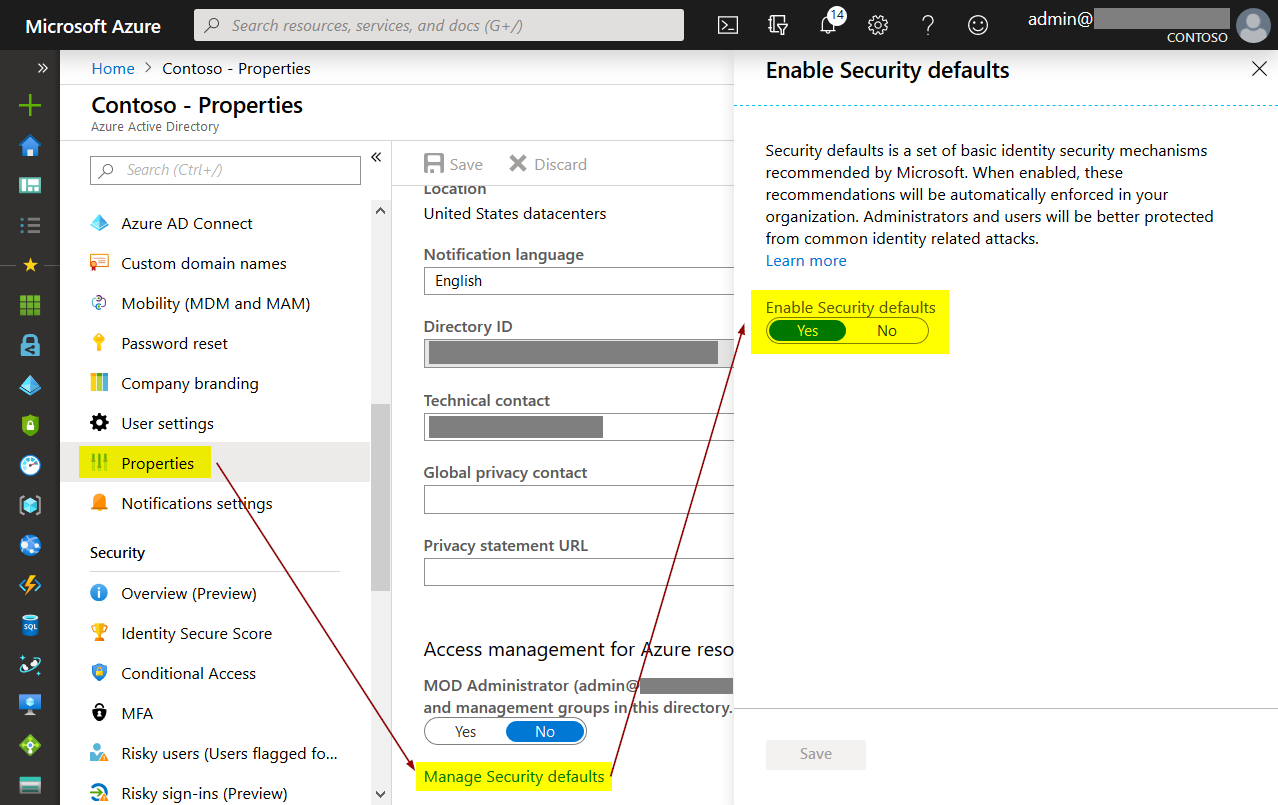
Azure AD Security Defaults – one click and done?
Security in the Microsoft world has never been an on/off switch. Looking back at Windows and especially Active Directory there have always been multiple steps that had to be considered. With the cloud and Azure AD, some companies used the possibility not to start with the same mistakes that were made in the past. Unfortunately,…

Automate MDATP response with Microsoft Flow
I recently met with a customer to discuss their migration from Kaspersky to Microsoft Defender ATP. They also use macmon to query the AV’s database to detect alerts and move affected clients to an isolated VLAN. Although MDATP is capable of handling incidents itself, the customer wanted to retain the capability to auto-isolate machines. At…

Going passwordless with Azure Active Directory – part 2
The passwordless story is not over. A while back, I summarized the possibilites we have to reduce the usage of passwords with Azure AD. You can find this post here: https://chrisonsecurity.net/2019/07/28/going-passwordless-with-azure-active-directory/ This topic will become more and more important in the future, so I decided to to a follow up to cover some additional things….

Defending against obfuscated malicious content via e-mail
When it comes to cyber attacks, e-mails are still in most cases the initial point of compromise. Users are either lured to enter their credentials on a spoofed website or malware is attached in an obfuscated way. For example, by leveraging Office macros or making the user to “Enable content” which is disabled by default…
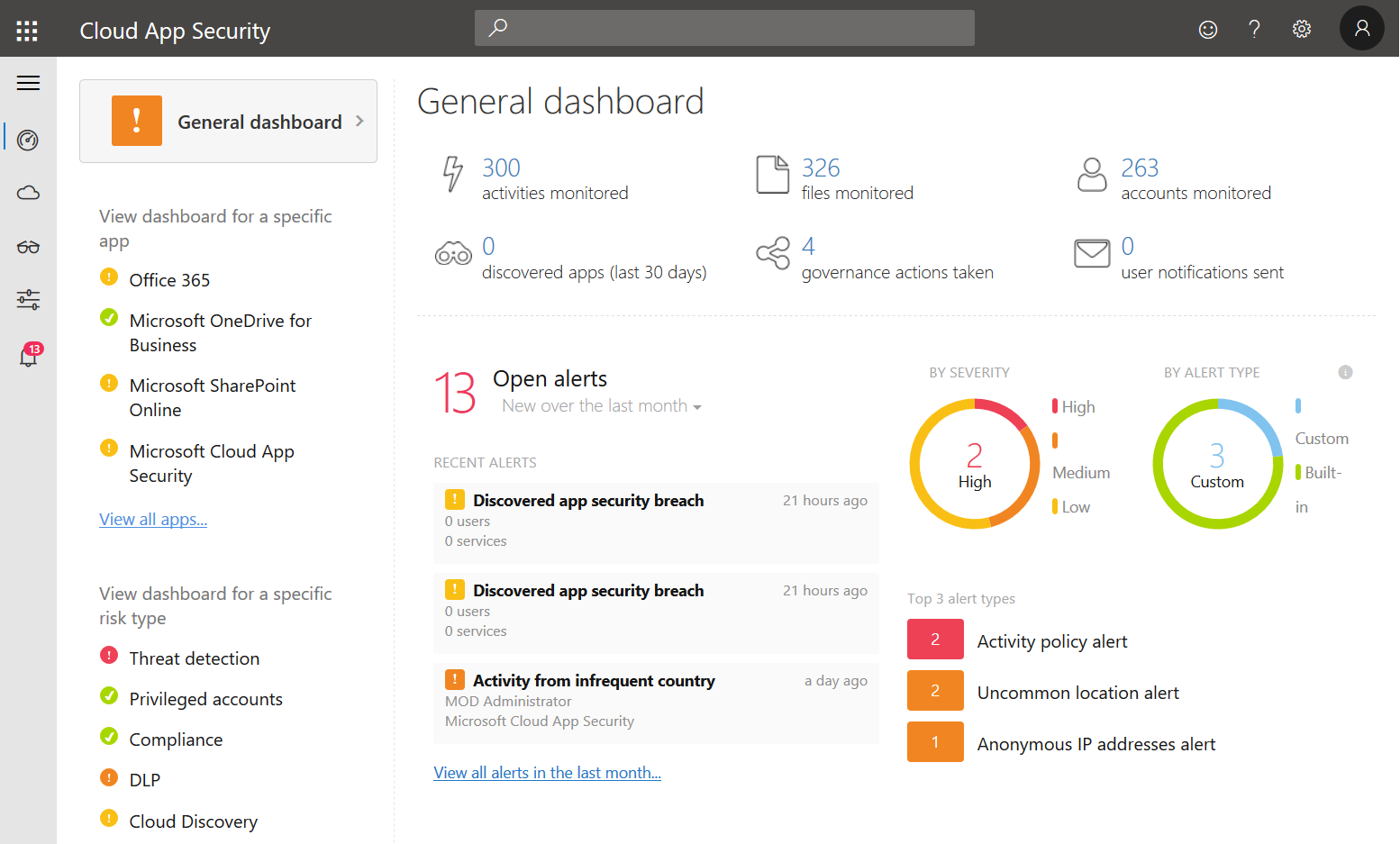
Microsoft Cloud App Security – 5 reasons to start using it
As a Cloud Access Security Broker (CASB), Microsoft Cloud App Security – or MCAS as I will call it in this post – is a central cloud security tool that let’s you gain visibility and control over your cloud services. It also offers a variety of ways to analyse cloud usage and potential threats like…
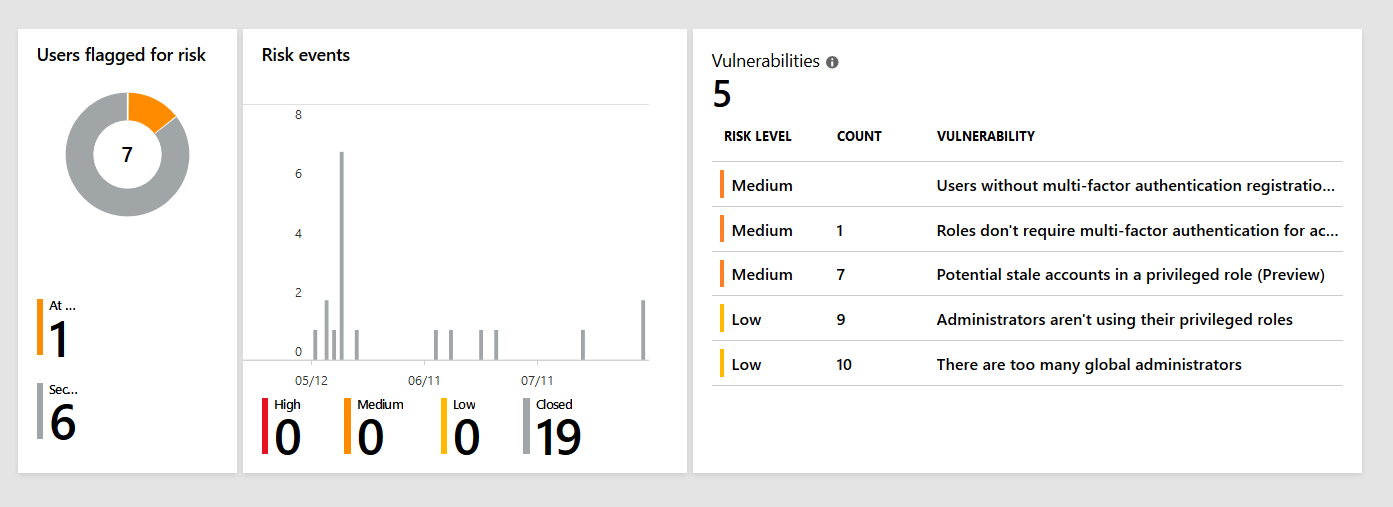
From the field: forced password reset in Azure AD Identity Protection
Azure AD Identity Protection is one of the most sophisticated features in Azure Active Directory (Premium P2). Based on Microsoft’s Intelligent Security Graph it detects users and sign-ins at risk and responds at a level you select. If you have the required licenses it should be part of every cloud security baseline. It features different…
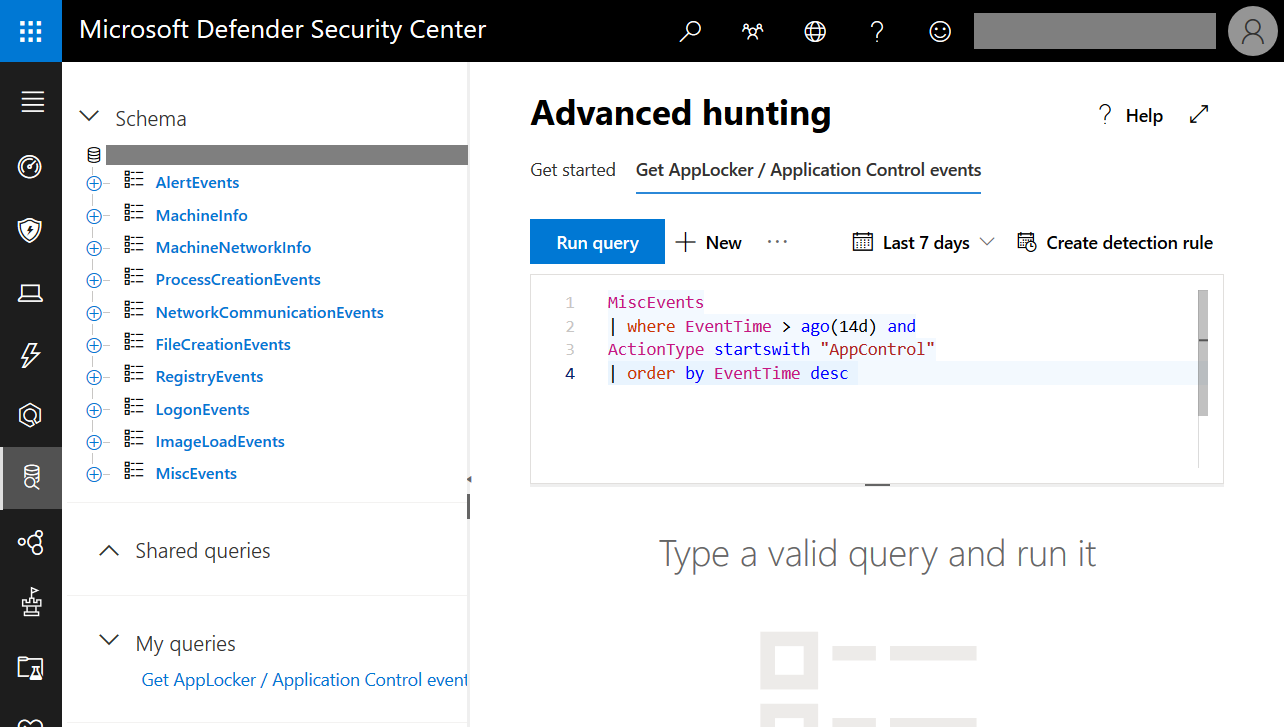
Cloud configuration of AppLocker using Intune and MDATP
In this post I will give you a quick overview about cloud configuration of AppLocker using Intune and MDATP. AppLocker has been with us for quite some time now reaching back all the way to good old Windows 7. Although it is not the best solution from a technical point of view (there’s Windows Defender…

Going passwordless with Azure Active Directory
Passwords are not ideal A world without passwords! Passwordless – seems to be the dream for anyone that has to manage a number of accounts. Who even likes passwords? Well, I know who doesn’t: IT admins don’t like passwords Why passwords are a major pain point for many organizations: reused credentials across multiple services increase…